AI service Cutout.Pro has suffered a data breach exposing the personal information of 20 million members, including email addresses, hashed and salted passwords, IP addresses, and names.
Cutout.Pro is an AI-powered photo and video editing platform for image enhancement, background removal, diffusion, colorizing, old photo restoration, and content generation.
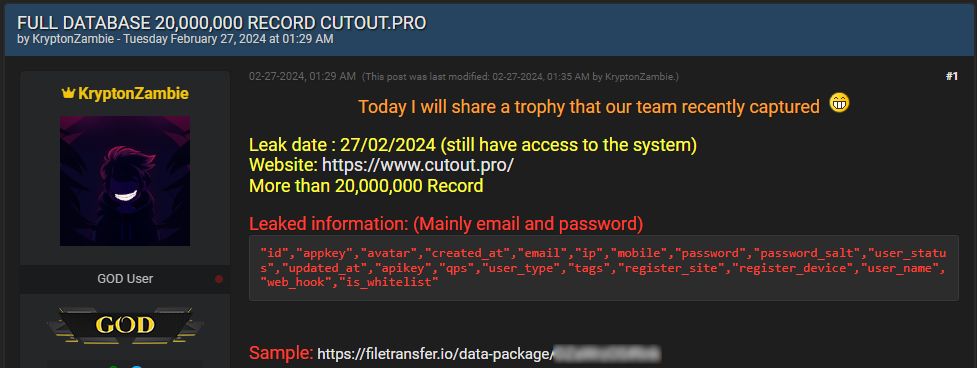
On Tuesday, someone using the alias 'KryptonZambie' shared a link on the BreachForums hacking forum to CSV files containing 5.93 GB of data stolen from Cutout.Pro.
These CSV files contain what appears to be a database dump consisting of 41.4 million records, with 20 million of those records consisting of unique email addresses.
The cybercriminal also stated that they still had access to the breached system, so the victim hadn't realized the compromise by the time of the data publication.
Source: BleepingComputer
From samples seen by BleepingComputer, the data that was leaked includes the following information:
- User ID and profile picture
- API access key
- Account creation date
- Email address
- User IP address
- Mobile phone number
- Password and salt used in hashing
- User type and account status
Data breach monitoring and alerting service Have I Been Pwned (HIBP) added the breach to its catalog yesterday, confirming that the leaked dataset includes the information for 19,972,829 people.
Also, the threat actor distributes the files on their personal Telegram channel, causing a much wider circulation of the stolen data.
Though Cutout.Pro has not verified the security incident from their side via an official statement, HIBP's founder Troy Hunt told BleepingComputer that he independently verified multiple matches from the leaked email addresses, confirming that password reset requests went through.
BleepingComputer also confirmed yesterday that emails listed in the data leak match legitimate Cutout.Pro users.
BleepingComputer emailed the company today and yesterday but did not receive a response. Hunt says he also tried to contact the service provider, with similar results.
If you have used Cutout.Pro in the past, it is recommended that you reset your password immediately on the service and any other online platforms where you might be using the same credentials.
MD5 password hashes are considered relatively easy to crack by modern standards, which is why more secure algorithms like bcrypt have superseded them. Hence, threat actors brute-forcing the leaked password hashes is a realistic possibility.
Furthermore, all Cutout.Pro users should be on the lookout for targeted phishing scams that attempt to gather further information from the user.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now