
The Bitwarden open-source password management service has introduced a new inline auto-fill menu that addresses the risk of user credentials being stolen through malicious form fields.
The issue was highlighted nearly a year ago when Flashpoint analysts demonstrated that it was possible for attackers to inject rogue iframes on vulnerable legitimate sites or subdomains susceptible to hijacking.
Bitwarden's response to the risk at the time was that the iframe auto-fill function should remain available for serving legitimate usage scenarios, like for icloud.com or apple.com, but will continue to be disabled by default.
Users who wanted to enable it would receive a visible warning about the risk of activating the option in the extension menu.
A few days later, the Bitwarden team announced they would add another layer of safety, allowing iframe auto-fills only on trusted sites and subdomains from the origin domain.
Today, the password manager introduced a system that incorporates lessons learned from past security challenges, enabling users to fill login credentials without risking losing their sensitive data to phishing actors.
Specifically, the following safeguards now ensure the security of the auto-fill system:
- Bitwarden will only fill credentials when a user selects a form field, mitigating the risk of automatic credential filling on malicious websites or iframes without user awareness.
- Users have the option to password-protect login information, adding another layer of security when using autofill.
- Extensive third-party penetration testing was conducted and to identify and close security gaps, presumably including those related to iframes and subdomains.
In terms of the user experience, the new inline auto-fill feature was designed to keep auto-filling an easy process by keeping the menu on top of all other visible elements, repositioning it based on page size and scrolling position, allowing keyboard navigation, and only displaying results if the user is logged into the extension.

By default, the feature is turned off but users can enable it from Bitwarden's extension icon in 'Settings' → 'Auto-fill', where they can set the 'Show auto-fill menu on form fields' dropdown options.
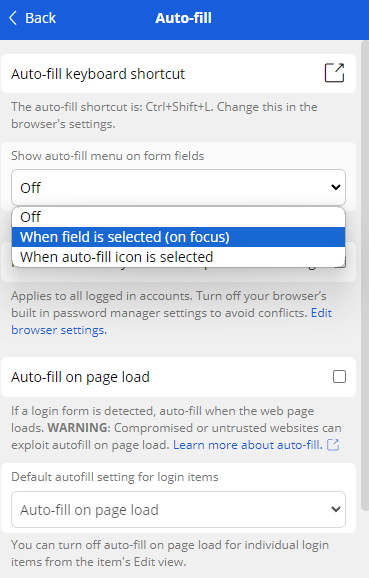
To avoid conflict, it is recommended to turn off auto-filling features on your web browser if it's enabled on the Bitwarden extension.
The password manager features multiple auto-fill options that include keyboard shortcuts, a dedicated context-menu, auto-fill on page load, and manual auto-fill.
Users can also set specific parameters for the trusted URLs they want Bitwarden to provide the auto-fill option.


Comments
fromFirefoxToVivaldi - 1 week ago
"Bitwarden will only fill credentials when a user selects a form field, mitigating the risk of automatic credential filling on malicious websites or iframes without user awareness."
If I were a user I would find this incredibly annoying.
Secondly, how does "credential filling on malicious websites" even work? Does Bitwarden not fill in password only websites the user has defined themselves? If so, do they not have any protections like warning about newly registered domains or potential typosquatting?
tech_engineer - 1 week ago
tech_engineer - 1 week ago
""Secondly, how does "credential filling on malicious websites" even work? Does Bitwarden not fill in password only websites the user has defined themselves? If so, do they not have any protections like warning about newly registered domains or potential typosquatting? "
read the article linked at the beginning of this article: they used iframe
fromFirefoxToVivaldi - 1 week ago
So in that hypothetical scenario the website is already compromised?
Wouldn't the attackers be able to do whatever with the credentials anyway? Even if they are put in legitimate form, wouldn't the be able to use JS to send all inputted text to their servers regardless?
0Willy - 1 week ago
That would depend on your definition of 'compromised'. https://perspectiverisk.com/real-world-xss-attacks-2-iframe-credential-harvesting/
https://owasp.org/www-community/attacks/xss/
0Willy - 1 week ago
Being safe online is not annoying. Needing layers of security to be safer is the annoying part.
The reality on many well-programmed sites is that focus is set on the logon name/password field. Depending on user auto-fill options, details auto-fill once the page finishes loading (also optional via settings). Sites that use pop-over logon may at times not auto-fill. Better that than hacked.
What is incredibly annoying is that I do not save my password to Bitwarden for my bank logon, only my logon name. Every time I log on, Bitwarden offers to save the password. There seems no way to stop the behavior.
tech_engineer - 1 week ago
"What is incredibly annoying is that I do not save my password to Bitwarden for my bank logon, only my logon name. Every time I log on, Bitwarden offers to save the password. There seems no way to stop the behavior. "
I fix this by writing the phrase "password not saved" or "you know the password" in the password field so the password manager doesn't complain about insecure password, then you can type your real password
0Willy - 1 week ago
I don't get an insecure password message. A blank functions the same as your phrase. Phrase of blank, when you type your password and Enter, BitWarden asks whether you wish to save the password. Every time!
On some sites, Bitwarden doesn't prompt to save logon content. So many, I no longer trust it and work with Notepad in case it needs to be done manually.