
The Phishing as a Service (PhaaS) platform 'LabHost' has been helping cybercriminals target North American banks, particularly financial institutes in Canada, causing a notable increase in activity.
PhaaS platforms provide turnkey phishing kits, infrastructure for hosting the pages, email content generation, and campaign overview services to cybercriminals in exchange for a monthly subscription.
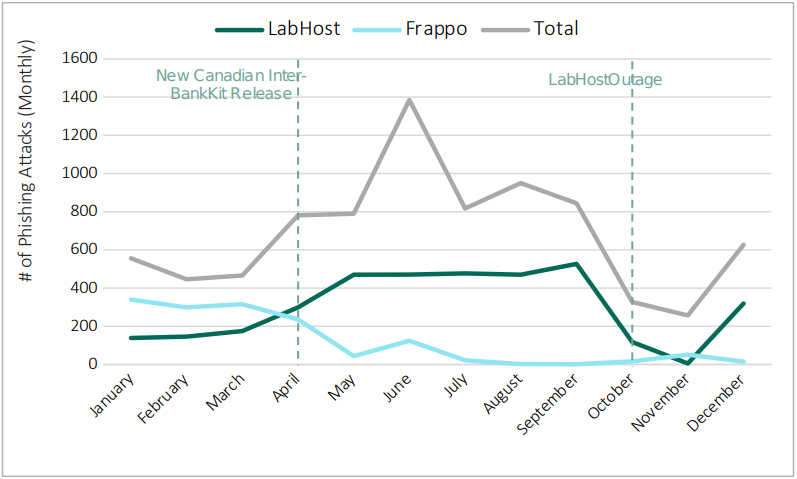
LabHost isn't a new provider, but its popularity surged after introducing custom phishing kits for Canadian banks in the first half of 2023.
Fortra, following the cybercriminal's activity, reports that LabHost has overtaken cybercriminals' previous favorite PhaaS platform, Frappo, and is now the primary driving force behind most phishing attacks targeting Canadian bank customers.
Though LabHost suffered a disruptive outage in early October 2023, it has restored its activity to notable levels, counting several hundreds of attacks per month.
Fortra first published a post on its blog section two weeks ago to alert about the emerging threat but added many more details about LabHost and its internal workings yesterday, after presumably infiltrating the operation with an account of their own.
A look inside LabHost
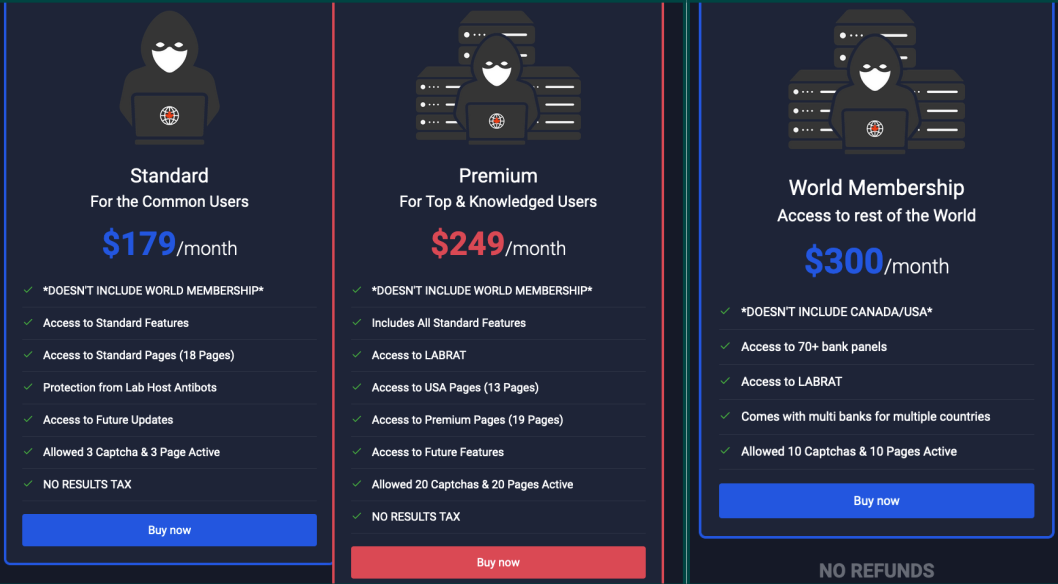
LabHost offers three membership tiers: the Standard ($179/month), Premium ($249/month), and World ($300/month).
The first focuses on Canadian banks, the second includes U.S. banks, and the third targets 70 institutions worldwide, excluding North America.
Apart from phishing kits for banks, the templates include phishing pages for online services like Spotify, postal delivery services like DHL, and regional telecommunication service providers.
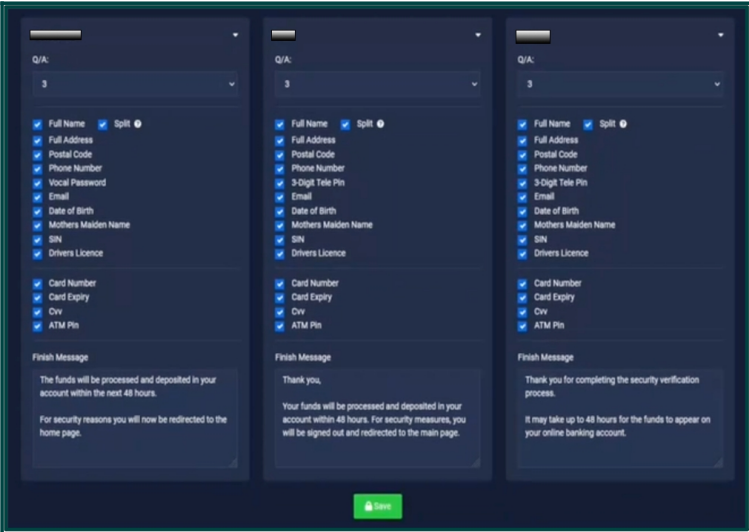
Cybercriminals buying access to the LabHost panel are given multiple installation options to craft custom attacks quickly.
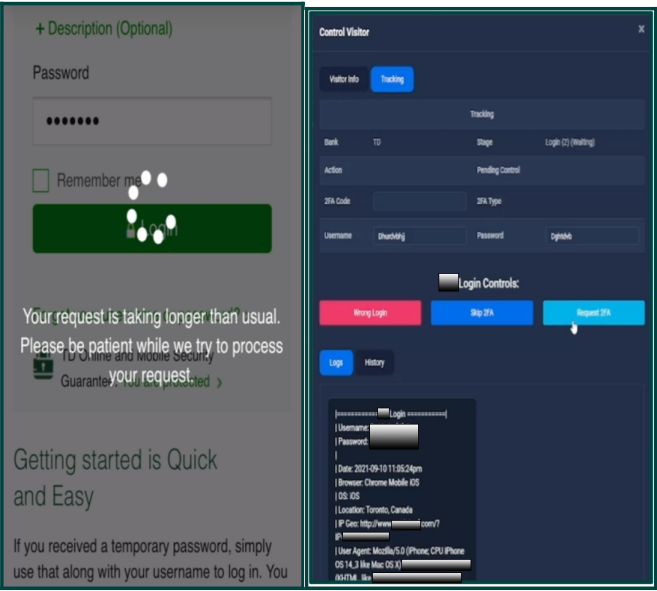
LabHost enables attackers to steal 2FA protection on targeted accounts by linking the phishing process to 'LabRat,' a real-time phishing management tool that lets cybercriminals monitor and control an active phishing attack.
"All scam kits available from LabHost work alongside a real-time campaign management tool named LabRat. LabRat allows the phisher to control and monitor their active attacks," explains Fortra.
"This functionality is leveraged in man-in-the-middle style attacks to obtain two-factor authentication codes, authenticate valid credentials, and bypass additional security checks."
In addition to the above, when LabHost relaunched following the October disruption, it introduced a new SMS spamming tool named 'LabSend,' which embeds links to LabHost phishing pages on SMS messages.
"The LabSend tool can coordinate an automated smishing campaign across multiple SIDs, randomizing portions of text messages to evade detection of cataloged malicious spam messages," reads Fortra's report.
"After sending an SMS lure, LabSend will auto reply to victims' responses using customizable message templates."
Phishing-as-a-Service platforms make cybercrime more easily accessible for unskilled hackers, significantly expanding the pool of threat actors and impacting cybersecurity on a broader scale.
Other notable PhaaS platforms researchers have warned about recently are 'Greatness' and 'Robin Banks,' both launched in mid-2022, featuring MFA bypassing, custom phishing kits, and admin panels.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now