
Microsoft says North Korean hacking groups have breached multiple Russian government and defense targets since the start of the year.
As the company claims in a report published today on threats from East Asia, the threat actors are taking advantage of Russia's focus on the invasion of Ukraine to harvest intelligence from compromised Russian systems.
"Multiple North Korean threat actors have recently targeted the Russian government and defense industry – likely for intelligence collection – while simultaneously providing material support for Russia in its war on Ukraine," said Clint Watts, the head of Microsoft's Digital Threat Analysis Center.
Microsoft is yet to provide further details regarding these attacks, such as what Russian organizations were breached, but the company's report does provide insight into when some of the attacks occurred.
One Russian aerospace research entity and Russian diplomatic accounts were all hacked this March, according to Redmond.
"In March 2023, Ruby Sleet compromised an aerospace research institute in Russia. Additionally, Onyx Sleet (PLUTONIUM) compromised a device belonging to a university in Russia in early March," the Microsoft Threat Intelligence team said.
"Separately, an attacker account attributed to Opal Sleet (OSMIUM) sent phishing emails to accounts belonging to Russian diplomatic government entities during the same month."
North Korean cyberattacks orchestrated by threat groups tracked as Ruby Sleet (aka CERIUM) and Diamond Sleet (aka ZINC and Lazarus) have also extended their scope to include arms manufacturers in various nations, which notably include Germany and Israel.
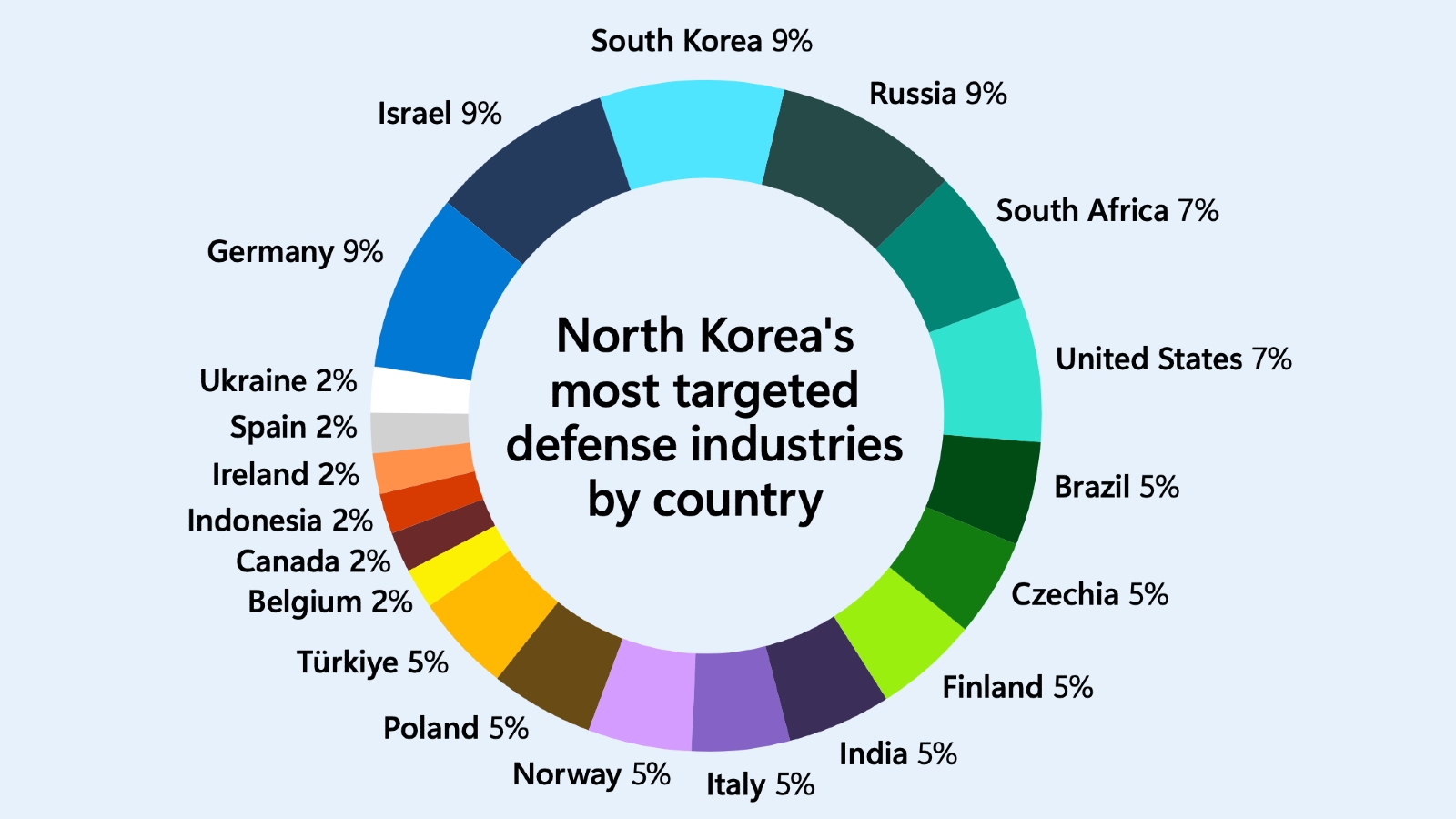
Defense firms in Brazil, Czechia, Finland, Italy, Norway, and Poland have also been subject to these intrusions, all as part of a coordinated endeavor to enhance the country's military capabilities.
"From November 2022 to January 2023, Microsoft observed a second instance of targeting overlaps, with Ruby Sleet and Diamond Sleet compromising defense firms," Microsoft said.
"Since January 2023, Diamond Sleet has also compromised defense companies in Brazil, Czechia, Finland, Italy, Norway, and Poland."
Microsoft's report follows one published by SentinelLabs last month linking the APT37 North Korean state-backed hacking group to the breach of Russian missile maker NPO Mashinostroyeniya.
The company is sanctioned by the U.S. Department of Treasury's Office of Foreign Assets Control (OFAC) for its role in the Russian invasion of Ukraine.
While the attackers' goal was unclear, SentinelLabs highlighted that the group's cyber-espionage efforts have focused on stealing data from the networks of compromised organizations.
The OpenCarrot backdoor deployed by APT37 on the systems of the Russian defense entity was previously linked to another North Korean threat group, the Lazarus Group.


Comments
h_b_s - 5 months ago
Also in the news, Kim Jong Un reportedly set to visit Putin in Russia: https://www.bbc.com/news/world-asia-66713476
And North Korea reportedly launches its first ballistic missile sub: https://www.bbc.com/news/world-asia-66747891 which looks remarkably like a Soviet era Delta class: https://upload.wikimedia.org/wikipedia/commons/thumb/8/83/Submarine_Delta_IV_class.jpg/1920px-Submarine_Delta_IV_class.jpg
Experts suggest it's probably not a functional weapons platform given the failures in its missile test launch programs. For historical perspective, the first generation US or Soviet ballistic missile submarines weren't effective weapons platforms either. Regardless of its ability to launch its primary weapons, it's probably easily found by modern sensors and likely a maintenance nightmare resulting it being more often in port than at sea.
It's really par for the course that NK is eavesdropping on Russia. Even allied nations spy on each other. It takes on a more weighty circumstance North Korea's team could use anything they discover as leverage with Putin's administration to gain favorable negotiating terms on top of Putin growing more desperate for weapons and economic assistance since the West turned soundly against him over his war of conquest.
Also, there's an element of potential sabotage with the timing of Microsoft's announcement coming on the heels of the potential meeting between Russia and NK. Possibly coincidental, possibly not.