
The Norwegian National Security Authority (NSM) has confirmed that attackers used a zero-day vulnerability in Ivanti's Endpoint Manager Mobile (EPMM) solution to breach a software platform used by 12 ministries in the country.
The Norwegian Security and Service Organization (DSS) said on Monday that the cyberattack did not affect Norway's Prime Minister's Office, the Ministry of Defense, the Ministry of Justice, and the Ministry of Foreign Affairs.
The Norwegian Data Protection Authority (DPA) was also notified about the incident, indicating that the hackers might have gained access to and/or exfiltrated sensitive data from compromised systems, leading to a data breach.
"This vulnerability was unique, and was discovered for the very first time here in Norway. If we had released the information about the vulnerability too early, it could have contributed to it being misused elsewhere in Norway and in the rest of the world," the NSM said.
"The update is now generally available and it is prudent to announce what kind of vulnerability it is, says Sofie Nystrøm, director of the National Security Agency.
The Norwegian National Cyber Security Center (NCSC) also notified all known MobileIron Core customers in Norway about the existence of a security update to address this actively exploited zero-day bug (tracked as CVE-2023-35078).
As a recommendation, the NCSC urged these system owners to install security updates to block incoming attacks as soon as possible.
Actively exploited authentication bypass vulnerability
The CVE-2023-35078 security bug is an authentication bypass vulnerability that impacts all supported versions of Ivanti's Endpoint Manager Mobile (EPMM) mobile device management software (formerly MobileIron Core), as well as unsupported and end-of-life releases.
Successful exploitation allows remote threat actors to access specific API paths without requiring authentication.
"An attacker with access to these API paths can access personally identifiable information (PII) such as names, phone numbers, and other mobile device details for users on a vulnerable system," the U.S. Cybersecurity and Infrastructure Security Agency (CISA) warned in an advisory published on Monday.
"An attacker can also make other configuration changes, including creating an EPMM administrative account that can make further changes to a vulnerable system."
The company has confirmed that the zero-day is being exploited in attacks and also warned customers that it's critical to "immediately take action to ensure you are fully protected.
According to Shodan's Internet exposure scanning platform, more than 2,900 MobileIron user portals are presently exposed online, out of which around three dozen are linked with U.S. local and state government agencies.
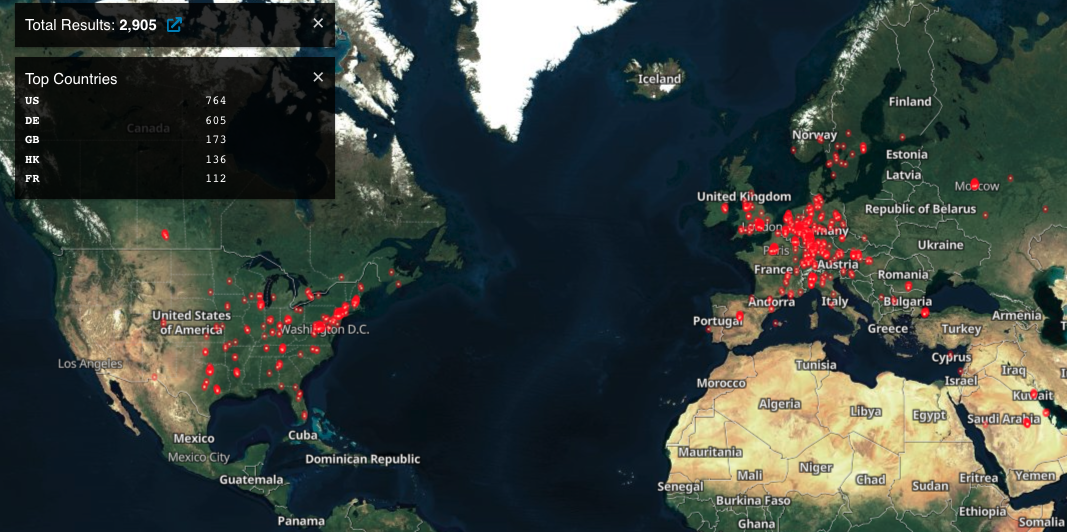
Most of these exposed servers are in the United States, with other notable locations including Germany, the United Kingdom, and Hong Kong.
In light of this, it is crucial for all network administrators to promptly install the latest Ivanti Endpoint Manager Mobile (MobileIron) patches to protect their systems from attacks.
Norway has disclosed other cyberattacks in which Chinese and Russian state hackers targeted its government websites and the country's parliament.
Last year, in June, the NSM said that Russian hacktivists took down multiple Norwegian government websites in DDoS attacks.
In March 2021, the Chinese state-sponsored Hafnium hacking group was linked to another incident in which they breached the systems of Norway's parliament and stole data by exploiting ProxyLogon Microsoft Exchange vulnerabilities.
In another attack from August 2020, multiple Norwegian Parliament email accounts on August were brute-forced. This incident was linked by Norway's Minister of Foreign Affairs in December 2020 to the Russian APT 28 state-sponsored hacking group.


Comments
EndangeredPootisBird - 7 months ago
>This vulnerability was unique, and was discovered for the very first time here in Norway. If we had released the information about the vulnerability too early, it could have contributed to it being misused elsewhere in Norway and in the rest of the world,"
And this is why PoC's should be banned