
GitHub is now automatically blocking the leak of sensitive information like API keys and access tokens for all public code repositories.
Today's announcement comes after the company introduced push protection in beta more than one year ago, in April 2022.
This feature proactively prevents leaks by scanning for secrets before 'git push' operations are accepted, and it works with 69 token types (API keys, private keys, secret keys, authentication tokens, access tokens, management certificates, credentials, and more) detectable with a low "false positive" detection rate.
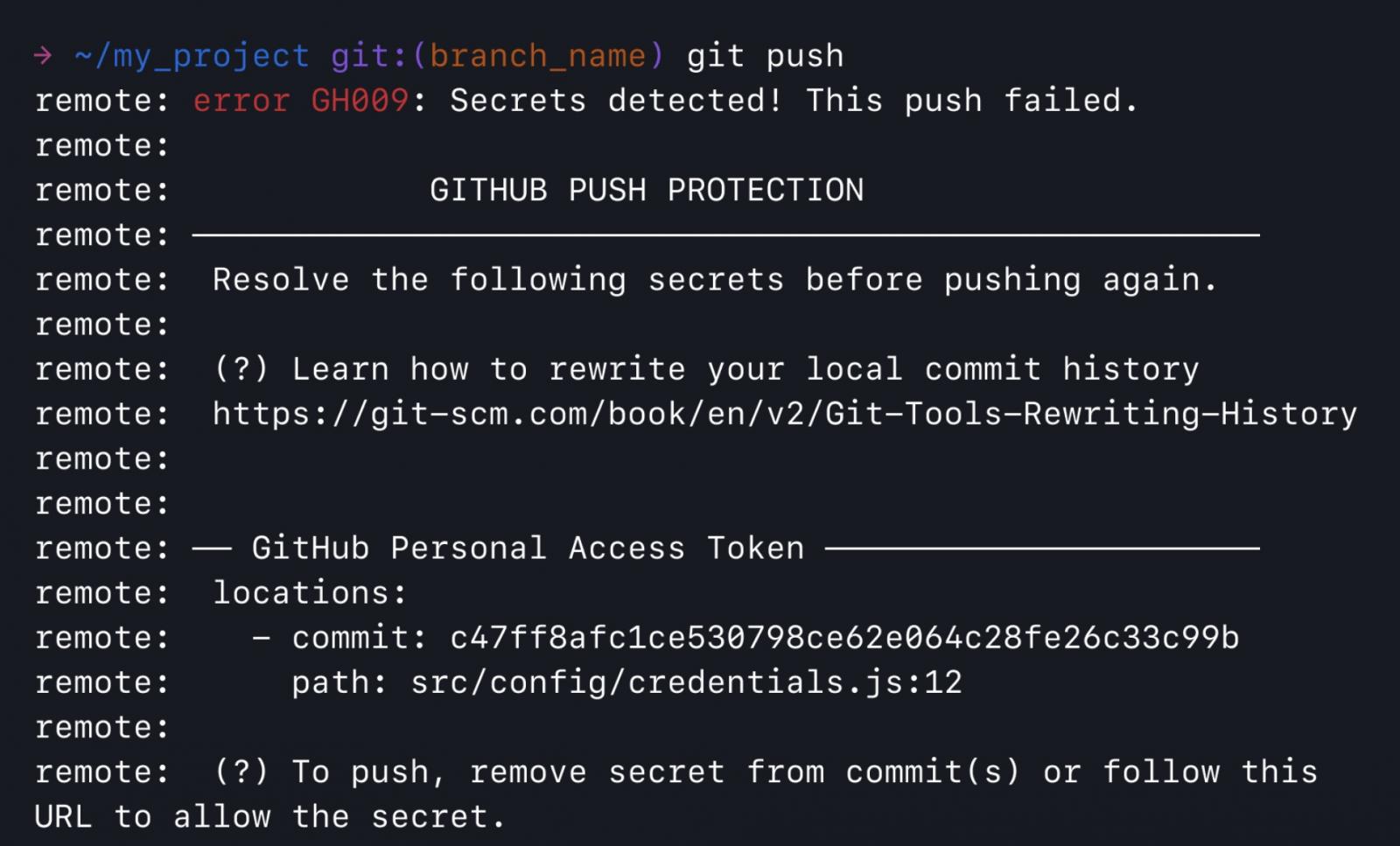
"If you are pushing a commit containing a secret, a push protection prompt will appear with information on the secret type, location, and how to remediate the exposure," GitHub said today.
"Push protection only blocks secrets with low false positive rates, so when a commit is blocked, you know it's worth investigating."
Since its beta release, software developers who enabled it successfully averted around 17,000 accidental exposures of sensitive information, saving more than 95,000 hours that would've been spent revoking, rotating, and remediating compromised secrets, according to GitHub.
While before today, this feature could only be enabled for private repositories by organizations with a GitHub Advanced Security license, GitHub has now also made it generally available on all public repos.
"Today, push protection is generally available for private repositories with a GitHub Advanced Security (GHAS) license," the company said.
"In addition, to help developers and maintainers across open source proactively secure their code, GitHub is making push protection free for all public repositories."
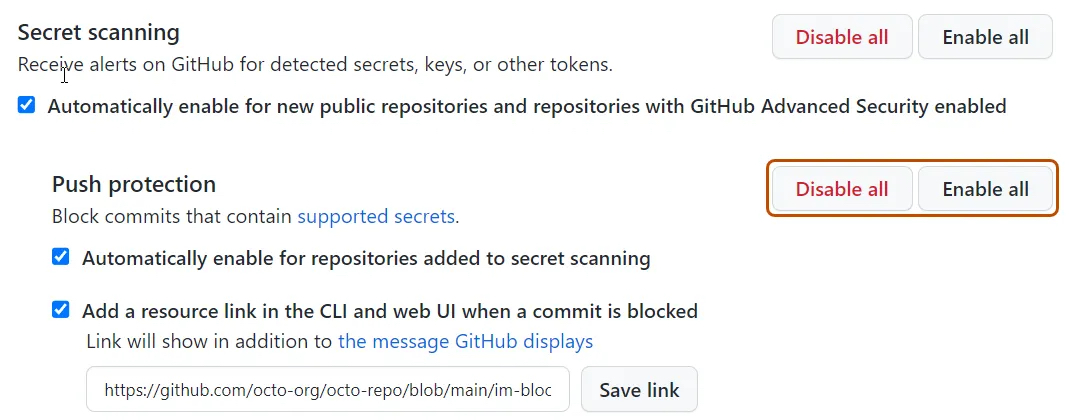
How to enable secret scanning push protection
Organizations with GitHub Advanced Security can enable the secret scanning push protection feature at both repository and organization levels via the API or with just one click from the user interface.
The detailed procedure for enabling push protection for your organization requires you to:
- On GitHub.com, navigate to the main page of the organization.
- Under your organization name, click Settings.
- In the "Security" section of the sidebar, click Code security and analysis.
- Under "Configure code security and analysis," find "GitHub Advanced Security."
- Under "Secret scanning," click Enable all next to "Push protection."
- Optionally, click "Automatically enable for private repositories added to secret scanning."
It can also be enabled for single repositories by toggling it from each repo's Settings > Security & analysis > GitHub Advanced Security dialog.
More details on using push protection from the command line or allowing some secrets to be pushed are available on GitHub's documentation site.
Exposed credentials and secrets have led to high-impact breaches in recent years, as BleepingComputer has previously reported [1, 2, 3].
Therefore, enabling push protection for private repositories or for free on public repositories to ensure that code pushes are automatically blocked if they contain any secrets is a simple way to defend against accidental leaks with potentially massive impacts.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now