GandCrab operators changed the ransomware business from the ground up, establishing a model that is embraced and continued by other cybercriminals.
Instead of keeping the operation private, limited to a small circle of experienced cybercriminals, they opened the doors to newcomers, advertised, built a relationship with customers and affiliates, and communicated with victims and researchers to stay on top of the game.
Shaping a new breed of cybercriminals
For many GandCrab partners, this was the first experience with ransomware and some grew to develop their own business. By following the same principles, some threat actors have reached new levels of financial success.
New ransomware collectives have formed, seeking affiliates to spread malware like Nemty and JSworm. REvil/Sodinokibi is the RaaS that appears to have filled GandCrab's shoes, promoted by respected veterans on underground forums, such as Lalartu a former GandCrab affiliate.
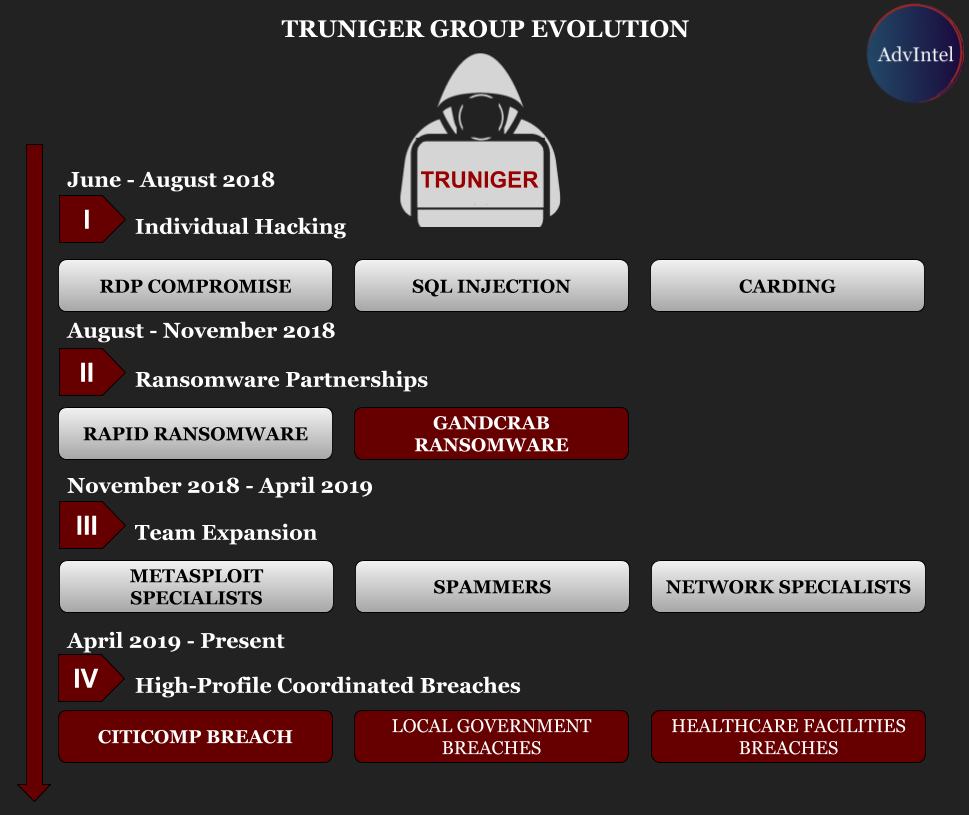
Another player involved in the ransomware business is "truniger." Currently a team of more than 10 individuals, the actor started in the summer of 2018 as a one-man show.
Initially, they were interested in credit card fraud but money started coming in when they switched to intrusions via a remote connection (RDP brute forcing and exploits).
Yelisey Boguslavskiy, director of security research at Advanced Intelligence (AdvIntel), says that in June 2018 'truniger' partnered with Rapid ransomware operators and by August they had encrypted data on over 1,800 systems.
This feat did not go unnoticed by the GandCrab team, who added 'truniger' to their affiliate program.
"After several months with GandCrab, truniger began building a ransomware collective similar to the one they saw established by their teacher. Through the next several months, the team massively expanded, hiring technical support for ransomware operations."
Help needed, attractive salary
In November 2018, the threat actor started to look for penetration testers (for moving stealthily through compromised networks), programmers, system administrators, spammers, and specialists in spear phishing.
They offered a monthly salary and sweetened the proposition as the business made more money and needed better-skilled personnel. In November, a penetration tester working for 'truniger' was promised a salary of up to $4,000.
In December someone focused privilege escalation within corporate networks would get at least $5,000. A Metasploit expert proficient in obtaining domain control access was promised at least $10,000 in March 2019.
Tools of the trade
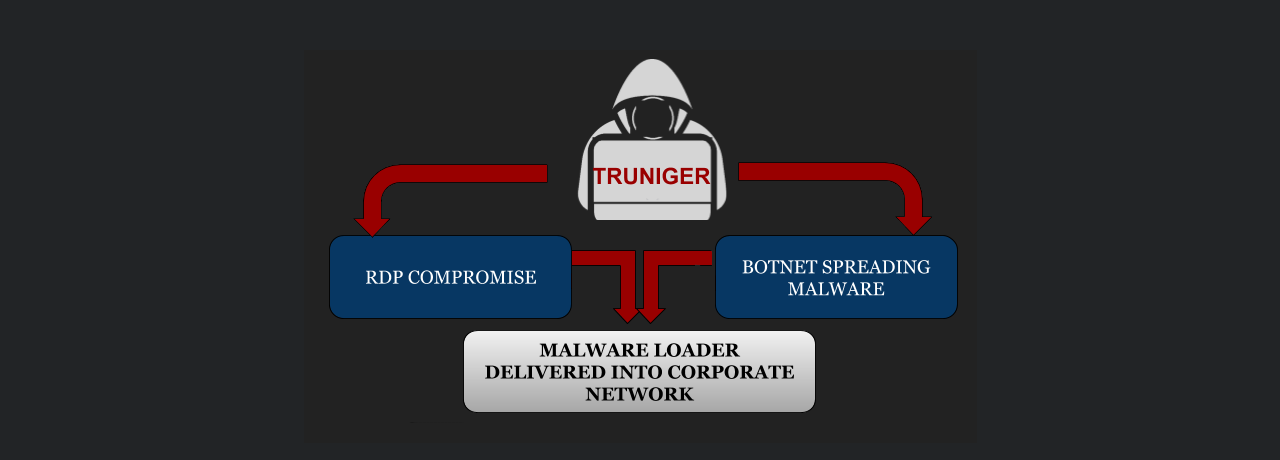
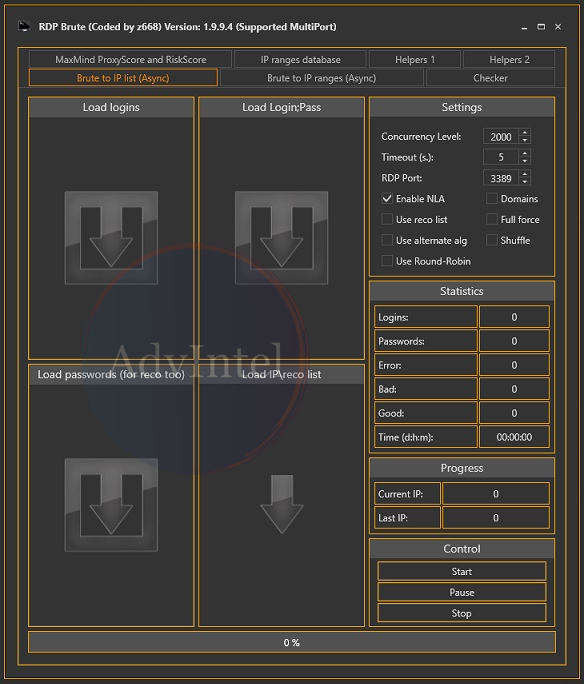
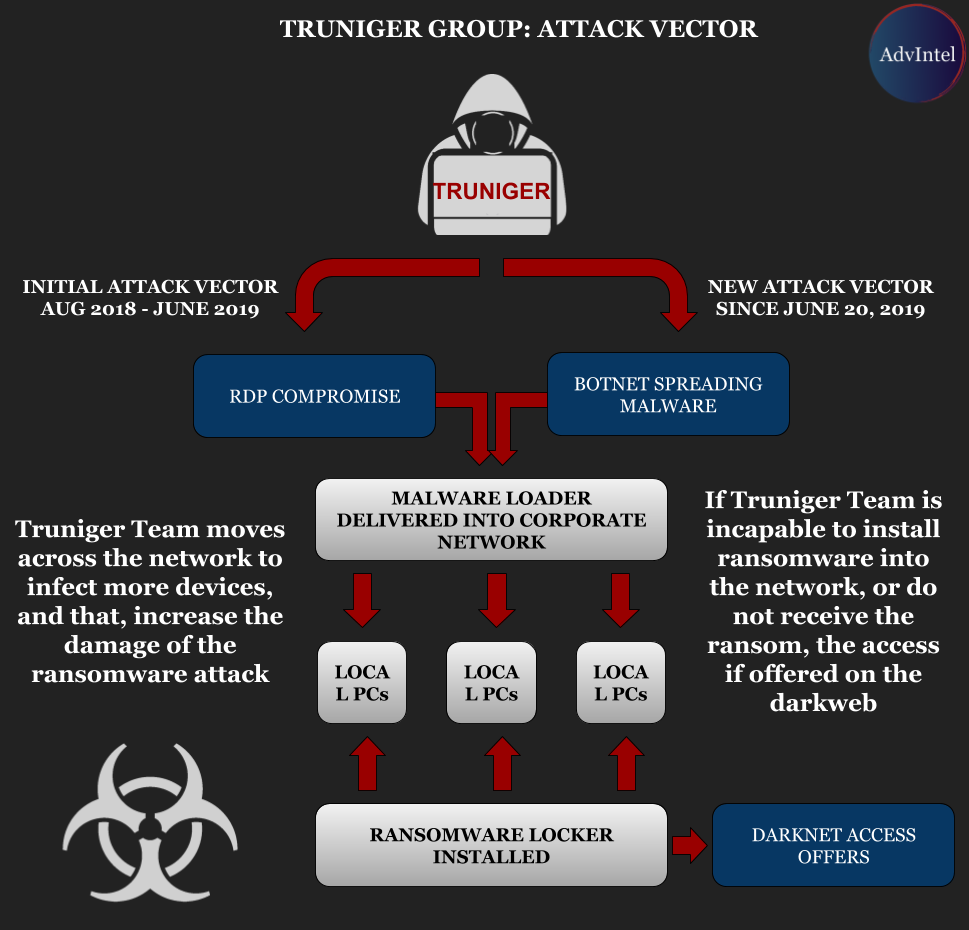
According to Boguslavskiy, this actor learned the tactics for ransomware distribution from GandCrab operators. They use RDP brute forcing to get into networks and rely on a custom tool for the job, called RDP Brute and developed by someone using the alias 'z668.'
RDP Brute is used during the initial engagement system. Once a stable foothold was established and the network assessed to make sure that as many computers as possible can be infected, the actor executes the file-encrypting malware on the victim's systems.
In a report published today, Boguslavskiy says that in June 2019 'truniger' announced a change in their attack vector, from RDP compromise to botnet.
'truniger' relies on the 'mimikatz' post-exploitation tool to extract passwords from a Windows system's memory and in a private chat they described part of their tactics:
"We have a loader, first we deliver the loader [via targeted email phishing] and then upload the bot, and then, by using the bot we upload all the meta and move further within the network. ... We are currently focusing on dedicated servers [and compromised RDPs] .... [we are] interested in macro and Dynamic Data Exchange (DDE) for our purposes."
The loader mentioned in the conversation is Amadey, quite popular on some underground forums for the low detection rate.
Despite a simple interface, Amadey provides a lot of information to the botnet administrator, who can see where victims are located, the operating system they use, the antivirus solution installed, and the time and date they were online.

Although strong evidence of a connection with REvil/Sodinokibi is lacking at the moment, AdvIntel's researcher says that there are clues suggesting that 'truniger' cooperates with the operators of this ransomware family on some level, possibly distribution.
The group keeps a secret which file-encrypting malware they're distributing, but it is certain that it is not one they developed. Some details disclosed in a previous report from AdvIntel indicates that they may be spreading REvil/Sodinokibi, given that a team member named -TMT-, specialized in corporate access, was introduced to this ransomware group by Lalartu.
Keeping the audience engaged
It seems that 'truniger' knows how to keep their business humming and gain some reputation points from fellow cybercriminals. While the group is all for making money, occasionally they share for free data collected from their hacking endeavors.
Nothing of significant importance is released, though. Boguslavskiy note in the post today that the group shared at the end of April data from German IT company CityComp, provider of IT infrastructure for various companies.
They credited an unnamed group for the hack that aimed to get a ransom for not leaking the files. The victim did not pay and the dump became public. High-profile users on the forum assessed that the files were of little value, though.
Media outlets announced the breach a few days after 'truniger' had dumped the files, reporting that the theft included data from big-name companies like Oracle, SAP, BT, Porsche, Toshiba, Volkswagen, and Airbus. CityComp confirmed the blackmail attempt in a statement.
The incident was attributed to a group calling themselves Team Snatch but in private conversations 'truniger' gave details saying that the "data was kept on a server, after a while, we just leaked them because they became redundant."
This was not the only instance when the group leaked details collected from their victims. On May 23, they published 13GB of insurance checks, bank transfer information and personally identifiable details of Italian citizens. The source was an Italian insurance company.
They also set up an auction, for full access with admin privileges on the network of a city's administration in Italy. The starting price was 1 bitcoin ($8,000), with a step-up of 0.2 bitcoin, and a blitz sale at 5 bitcoins; and someone paid.
"There are more than 200 machines, servers, and workstations in the network, more than 10 class-C subnetworks, subnetworks for VoIP," the announcement read.
In a more recent advertisement from July 17, 'truniger' offered access to a KIA dealership in Canada for $3,000. Having limited privileges and not being able to deploy malware on the network is the reason 'truniger' makes offers like this.
These operations and the quick rise of the group are clearly the result of GandCrab's influence. It's not just the business model that matters in achieving success; social interaction with fellow cybercriminals, potential employees and partners are also part of the game.
head image source: AdvIntel


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now