
Malware researchers have discovered a new file-encrypting malware they dubbed DoppelPaymer that has been making victims since at least mid-June, asking hundreds of thousands of US dollars in ransom.
The ransomware strain has at least eight variants that extended their feature set gradually, with the earliest one dating since April.
Victims in the public service sector
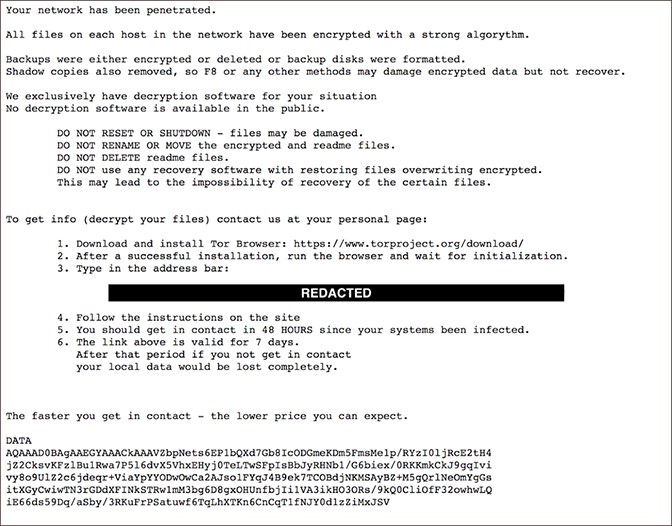
DoppelPaymer takes its name from BitPaymer, with which it shares more than large portions of code. There are three confirmed victims of this ransomware strain, which priced its decryption keys between 2 BTC and 100 BTC, say researchers from CrowdStrike.
Bitcoin price in late April was around $5,150 and kept rising ever since, with lows well above the $7,000 mark and peaking above $12,000 in late June and early July.
One of the victims is the City of Edcouch, Texas, which was left with a ransom note demanding 8 BTC to decrypt the data on the affected computers.
It is unclear when the Edcouch administration was attacked, but city officials said that the amount converted to about $40,000. This makes it likely that the compromise happened in early May or before when bitcoin price stooped below $5,500.
Another victim was the Chilean Ministry of Agriculture, the researchers said in a report last week. The country's Computer Security Incident Response Team (CSIRT) confirmed on July 1 that a ransomware attack hit servers from a public service connected to the Ministry of Agriculture.
Parallel extortion activity
CrowdStrike researchers observed some striking similarities between DoppelPaymer's payment portal and the original one for BitPaymer. One striking hint linking the two ransomware threats is the "Bit paymer" title at the top of the page but they're similar all over.
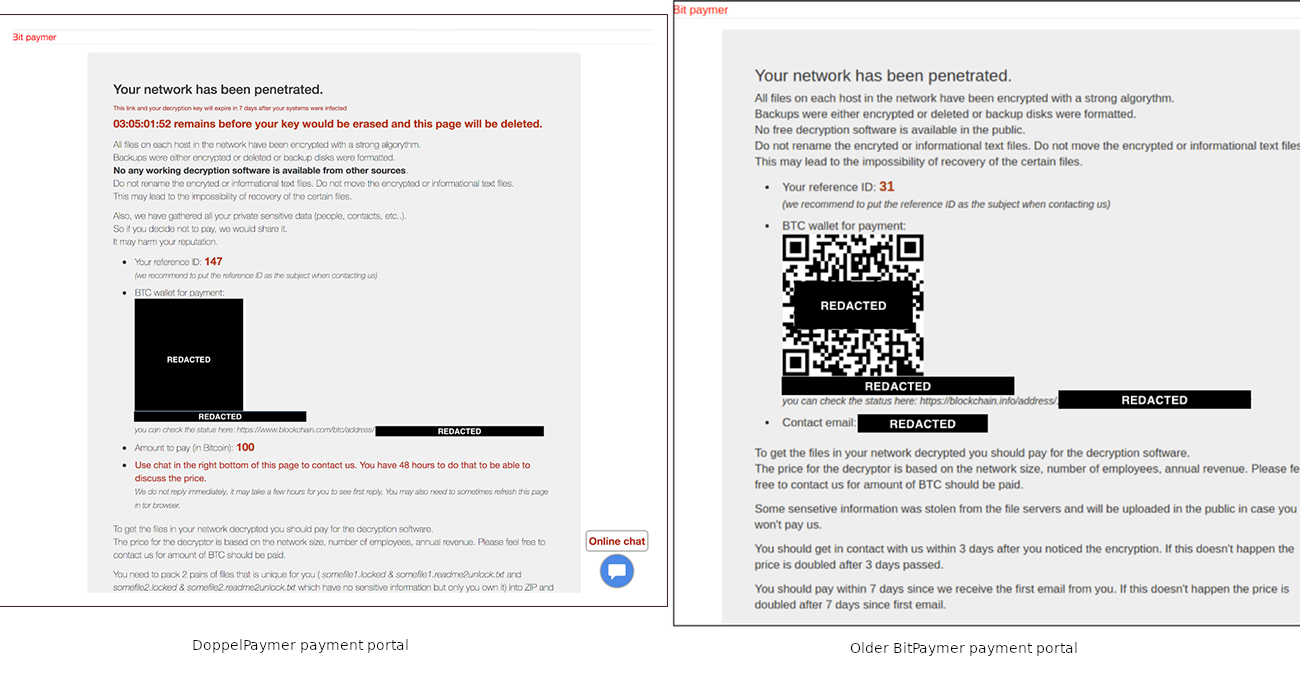
Another clue pointing to a connection between the two pieces of malware is that they "share significant amounts of code." However, they have different encryption schemes.
Where DoppelPaymer combines 2048-bit RSA keys with 256-bit AES, the latest BitPaymer versions use 4096-bit RSA with the same specification for symmetric encryption.
Also, there is standard AES encryption padding (PKCS#7) in DoppelPaymer while BitPaymer uses random bytes specified in a field called 'TAIL.'
By analyzing differences and similarities between the two, Brett Stone-Gross, Sergei Frankoff and Bex Hartley of CrowdStrike's research and threat intel team believe that the new ransomware strain may be the work of a BitPaymer group member that started their own ransomware business.
"Both BitPaymer and DoppelPaymer continue to be operated in parallel and new victims of both ransomware families have been identified in June and July 2019. The parallel operations, coupled with the significant code overlap between BitPaymer and DoppelPaymer, indicate not only a fork of the BitPaymer code base, but an entirely separate operation." - CrowdStrike
The new ransomware includes modifications that make it superior to BitPaymer, such as threaded encryption process for a quicker operation.
The operators of BitPaymer are the same individuals behind the Dridex banking trojan, collectively known as the INDRIK SPIDER. They are former affiliates of the cybercriminal gang calling itself "The Business Club."
The group is responsible for using the GameOver Zeus botnet (disrupted in 2014), believed to have infected over one million computers, and causing damages in excess of $100 million from business and financial institutions across the world.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now