
A distributor for the Sodinokibi Ransomware is hacking into WordPress sites and injecting JavaScript that displays a fake Q & A forum post over the content of the original site. This fake post contains an "answer" from the site's "admin" that contains a link to the ransomware installer.
As security software and people become more aware of the methods that are used to distribute ransomware and malware, affiliates need to come up with craftier methods to infect their victims.
Such is the case with a new distribution method that overlays a fake Questions and Answers forum on top of the content of a hacked site. This fake forum post will contain information related to the content of the page that the user is visiting, so it appears that the answer and link offered by the admin is legitimate.
In reality, though, the downloaded file will infect the user with the Sodinokibi, or REvil, Ransomware.
How the fake Questions and Answers overlay attack works
BleepingComputer was first alerted to this new attack method by Aura, who has seen multiple victims become infected via this method. Below we will provide a general overview of how this attack works and the process used to install the Sodinokibi, or REvil, Ransomware.
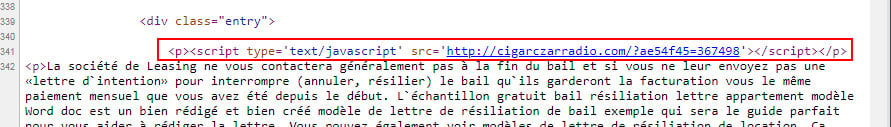
Similar to the older EITest Chrome HoeflerText Font Update attack, the affiliate is hacking into sites so that it injects a JavaScript script into the HTML as shown below. The injected URL will be active to all visitors, but will only contain data if the user is visiting for the first time or has not been to the site in a certain amount of time.
When someone visits the site for the first time, the script will cause a fake French Questions and Answers forum post to display over the content as shown below.
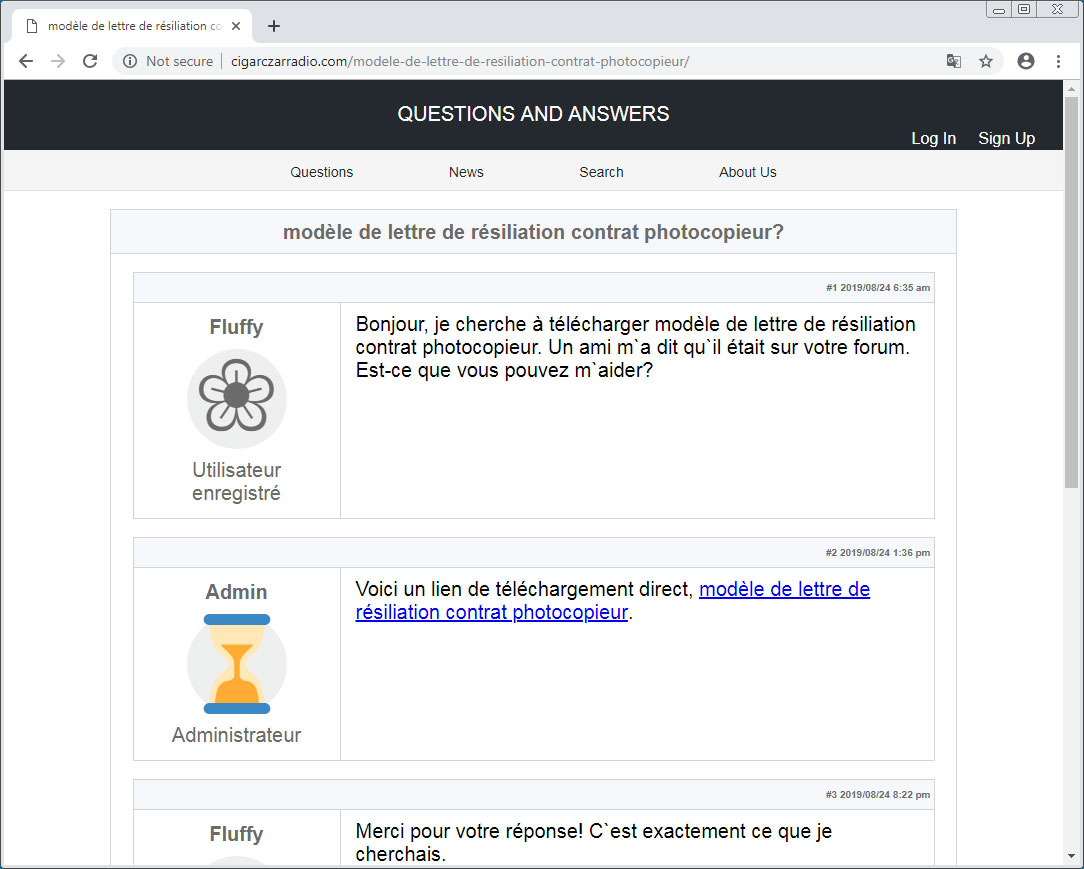
To the user, the above looks like the normal site as the content of the fake forum post is related to the content of the hacked page, but in reality is just an overlay created by the script.
If a user refreshes the page again, the script will not fire and the normal page will be shown as seen in the demonstration video at the end of the article.
If a user does not refresh the page, though, it will appear as if another visitor posted a question in French to the site about a "termination contract" for a photocopier model.
"Hello, I am looking to download letter of termination contract photocopier model. A friend told me he was on your forum. Can you help me?"
In response to the question, a fake answer will be provided by the Admin that provides a direct link to the sought after contract.
"Here is a direct download link, model letter of termination contract photocopier."
When a user clicks on the link, a zip file will be downloaded from a random hacked site under the attackers control. In this particular example, the file will be named "modèle_de_lettre_de_résiliation_contrat_photocopieur.zip" and when opened will contain a JScript file with the same name.
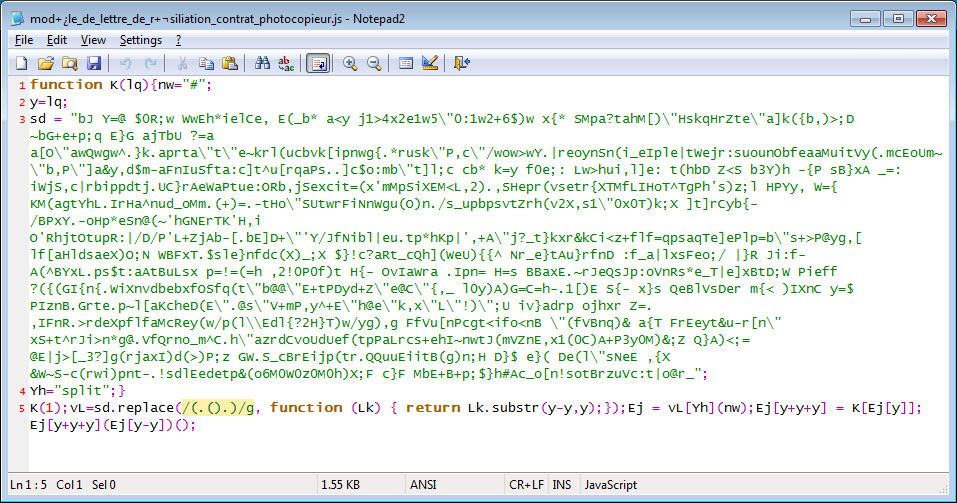
This JScript file contains obfuscated code that will connect to a remote server, which will respond with a large blob of data.
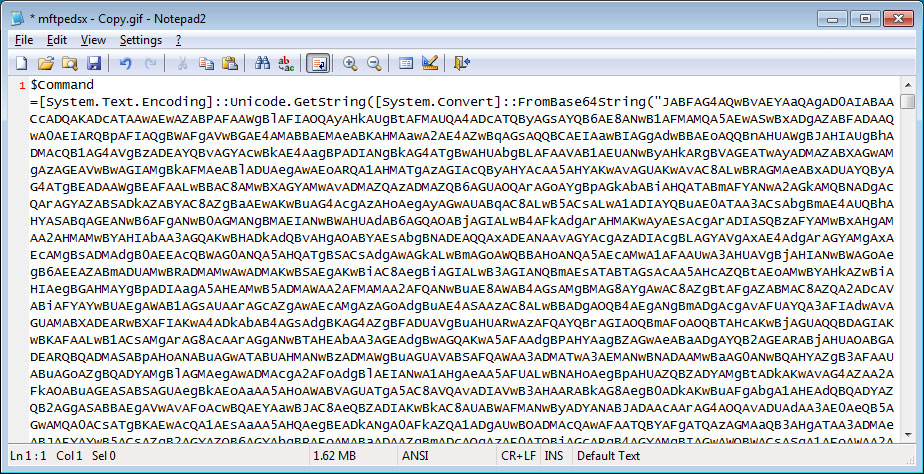
This data will be decrypted, which can take quite a while, and then saved as a GIF file in the %UserProfile% folder. This file contains an slightly obfuscated PowerShell command, which will be cleaned by up by using the ReadAllText.Replace function to remove any ~ characters from it.
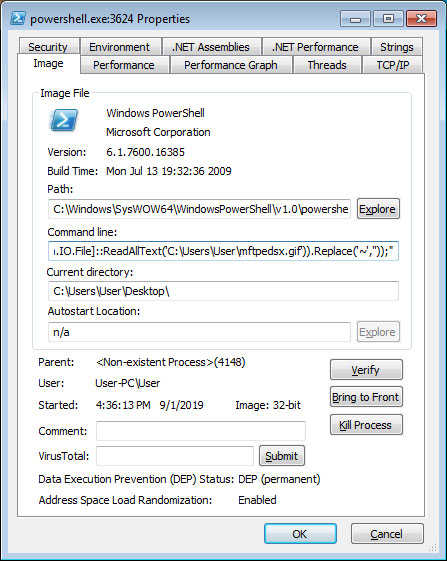
This will result in a clean PowerShell command, which will then be used to execute the Sodinokibi DLL in order to encrypt a computer.
During the encryption process, the attackers will clear the victim's Shadow Volume Copies using the following PowerShell command:
Get-WmiObject Win32_Shadowcopy | ForEach-Object {$_.Delete();}
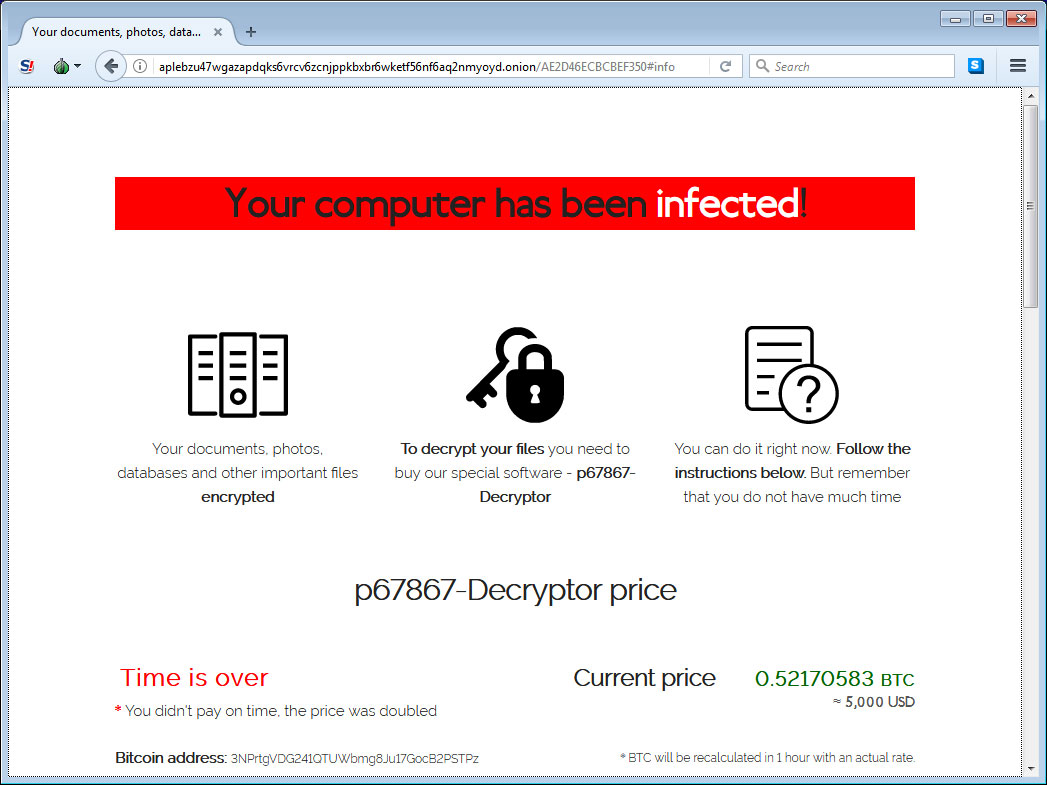
When done, the victim's files will be encrypted and a ransom note will lead them to a Tor payment site that contains information on how to purchase a decryptor.
To protect yourself from an attack like this, be sure to have some sort of security software installed with real-time protection and never execute files that end with the .js extension.
For those who wish to see how this fake Forum overlay works, BleepingComputer has created a video demonstration as shown below.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now