
The Egregor ransomware gang has hit game developer Crytek in a confirmed ransomware attack and leaked what they claim are files stolen from Ubisoft's network.
Ubisoft and Crytek are both well-known game developers with corporate headquarters in France and Germany, respectively.
This week, the Egregor ransomware game posted archives containing unencrypted files, stating that they were stolen from Ubisoft and Crytek in unrelated attacks.
While it has not been confirmed if the attack against Ubisoft is legitimate, BleepingComputer has confirmed that Crytek suffered a ransomware attack.
If you have first-hand information about this or other unreported cyberattacks, you can confidentially contact us on Signal at +16469613731 or on Wire at @lawrenceabrams-bc.
Crytek hit by confirmed ransomware attack
This week, sources told BleepingComputer that Crytek had suffered an attack at the hands of the Egregor ransomware operators.
While we were not told how many devices were encrypted, we were told that files were encrypted and renamed to include the '.CRYTEK' extension. For example, a file named test.jpg would have been encrypted and renamed to test.jpg.CRYTEK.
In addition to encrypting the devices, the Egregor gang claims to have stolen unencrypted files from Crytek and leaked a 380MB archive on their data leak site.
This leaked data includes files related to WarFace, Crytek's canceled Arena of Fate MOBA game, and their network operations.
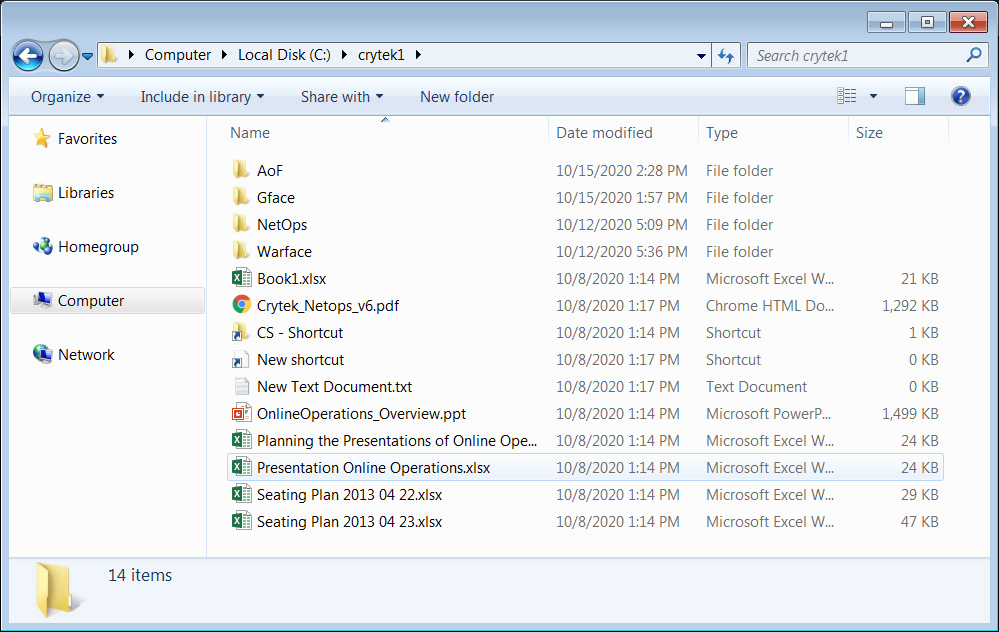
BleepingComputer does not know when the attack took place,and our emails to Crytek have not been answered.
Ubisoft's Watchdogs Legion source code allegedly stolen
Egregor ransomware also claimed to have breached Ubisoft's network and stolen unencrypted data, including the source code for the upcoming Watch Dogs: Legion game.
As part of this leak, Egregor has posted a 20MB archive containing game assets the ransomware gang says are part of Ubisoft's Watch Dogs game.
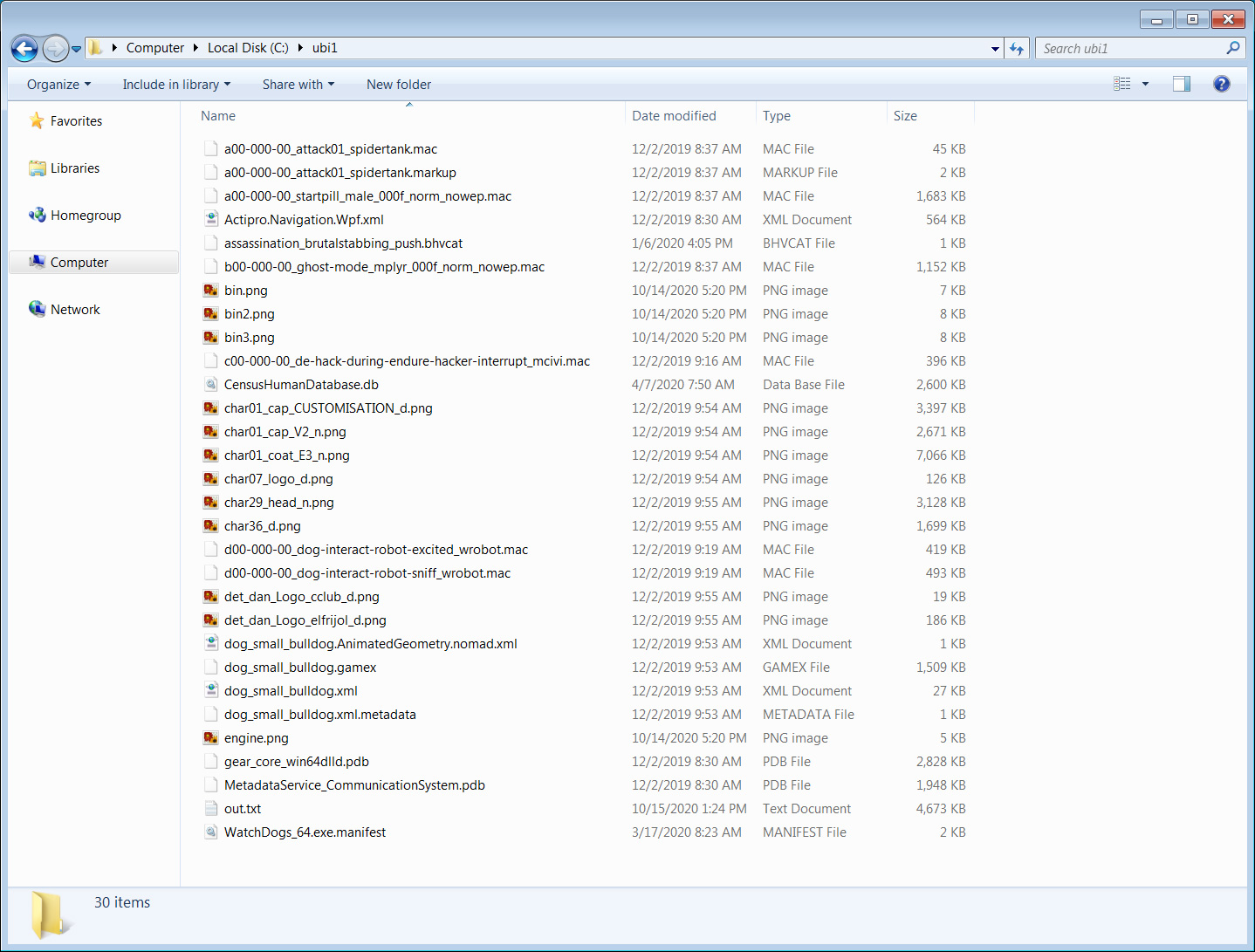
None of these game assets, though, prove that they were actually stolen from Ubisoft, and could easily have been obtained elsewhere.
Security researcher MalwareHunterTeam has told BleepingComputer that they have been trying to warn Ubisoft for almost a year that their employees have fallen victim to phishing attacks, but never received a response.
Our emails to Ubisoft remain unanswered as well.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now