
CISA, the NSA, and MS-ISAC warned today in a joint advisory that attackers are increasingly using legitimate remote monitoring and management (RMM) software for malicious purposes.
More worryingly, CISA discovered malicious activity within the networks of multiple federal civilian executive branch (FCEB) agencies using the EINSTEIN intrusion detection system after the release of a Silent Push report in mid-October 2022.
This activity was linked to the "widespread, financially motivated phishing campaign" reported by Silent Push and was detected on "many other FCEB networks" after first being spotted on a single FCEB network in mid-September 2022.
The attackers behind this campaign began sending help desk-themed phishing emails to federal staff's government and personal email addresses since at least mid-June 2022.
"The authoring organizations assess that since at least June 2022, cyber criminal actors have sent help desk-themed phishing emails to FCEB federal staff's personal, and government email addresses," the advisory reads.
"The emails either contain a link to a 'first-stage' malicious domain or prompt the recipients to call the cybercriminals, who then try to convince the recipients to visit the first-stage malicious domain."
Callback phishing attacks like the ones targeting FCEB staff in this campaign have seen a massive 625% growth since Q1 2021 and have also been adopted by ransomware gangs.
These groups include ones that split from the Conti cybercrime operation, such as the Silent Ransom Group, Quantum (now Dagon Locker), and Royal.
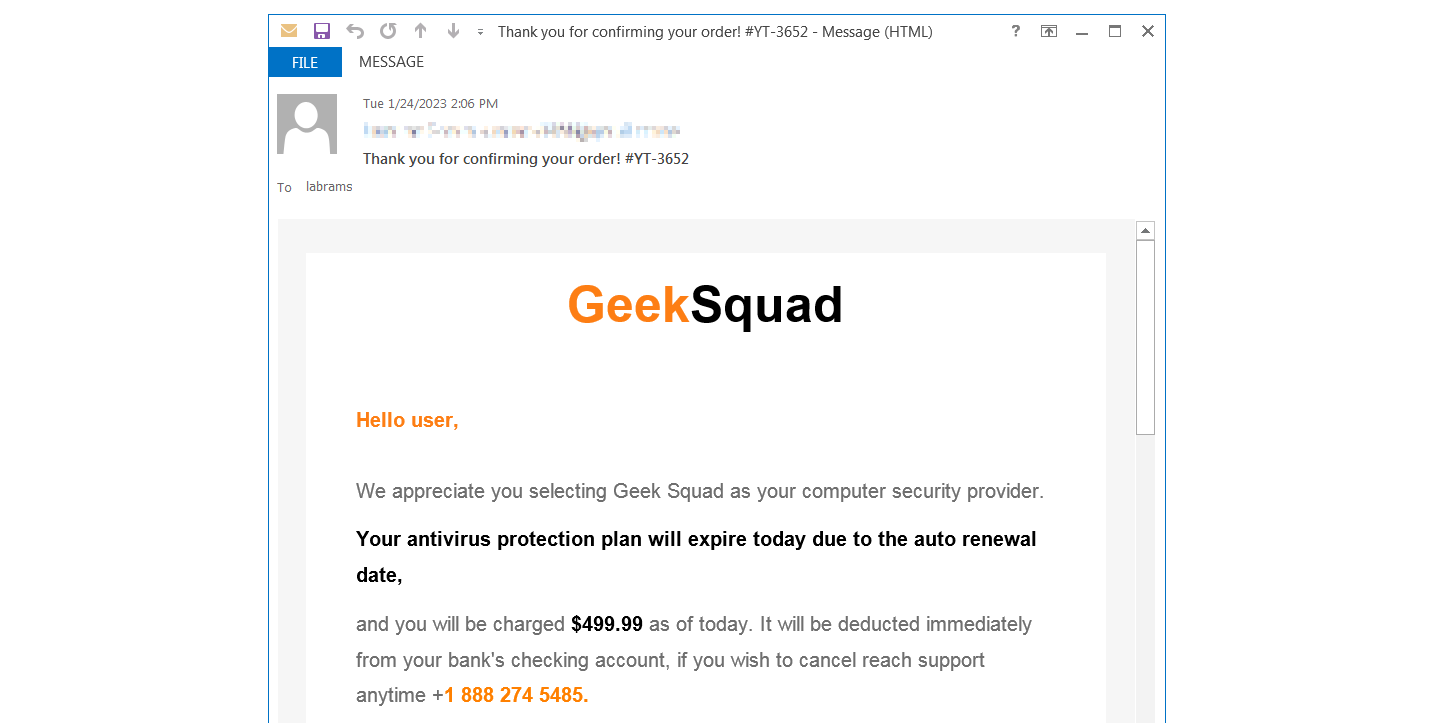
Unlike normal phishing emails, callback phishing attacks do not include a link to a threat actor's website. Instead, they use lures, such as high-priced subscription renewals, to convince a target to call a listed phone number.
When a target calls the number, they will be told to open a website to download the software required to refund the renewal price.
When the emails embedded malicious links instead, the phishing domains used were designed to impersonate high-profile brands, including Microsoft, Amazon, and Paypal.
Clicking the embedded links would open the default web browser and automatically download malware designed to connect to a second-stage domain to download portable versions of AnyDesk and ScreenConnect that connect to the attackers' RMM server.
The use of portable remote desktop software executables allows malicious actors to gain access to the targets' systems as a local user without requiring admin permissions or a complete software installation, thus bypassing software controls and challenging common risk management assumptions.
FCEB networks breach linked to refund scammers
Once they managed to take a foothold on their targets' devices, the threat actors used their access to try and trick victims into logging into their bank accounts so that they could initiate refund scams.
"Although this specific activity appears to be financially motivated and targets individuals, the access could lead to additional malicious activity against the recipient's organization—from both other cybercriminals and APT actors," the advisory says.
"Malicious cyber actors could leverage these same techniques to target National Security Systems (NSS), Department of Defense (DoD), and Defense Industrial Base (DIB) networks and use legitimate RMM software on both work and home devices and accounts," the NSA added.
Defenders are encouraged by CISA, NSA, and MS-ISAC to use indicators of compromise shared with the advisory to detect potential exploitation or compromise.
First-stage domain names used in the campaign follow naming patterns commonly utilized in IT help/support-themed social engineering scams: myhelpcare[.]online. myhelpcare[.]cc, hservice[.]live, gscare[.]live, nhelpcare[.]info, deskcareme[.]live, nhelpcare[.]cc, win03[.]xyz, win01[.]xyz, 247secure[.]us.
Another active domain in this campaign seen by BleepingComputer is winbackup01[.]xyz.
CISA encourages network defenders to review the advisory for indicators of compromise, best practices, and recommended mitigations, which highlights the threat of additional types of malicious activity using RMM, including its use as a backdoor for persistence and/or command and control (C2). — CISA
They also provided a list of measures designed to help mitigate such risks and ensure that networks are secure from incoming attack attempts.
To protect against potential security breaches, companies and organizations should audit installed remote access tools and identify authorized RMM software.
The use of application controls to prevent the execution of unauthorized RMM software and only utilizing authorized RMM software over approved remote access solutions, such as VPN or VDI, is also recommended, as is blocking both inbound and outbound connections on standard RMM ports and protocols.
To further enhance security, organizations should implement training programs and phishing exercises to raise awareness among their employees about the risks linked to phishing and spearphishing emails.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now