
Google announced today new cybersecurity defense controls that will allow security teams to thwart social engineering attacks like phishing targeting Workspace users and prevent account takeover attempts.
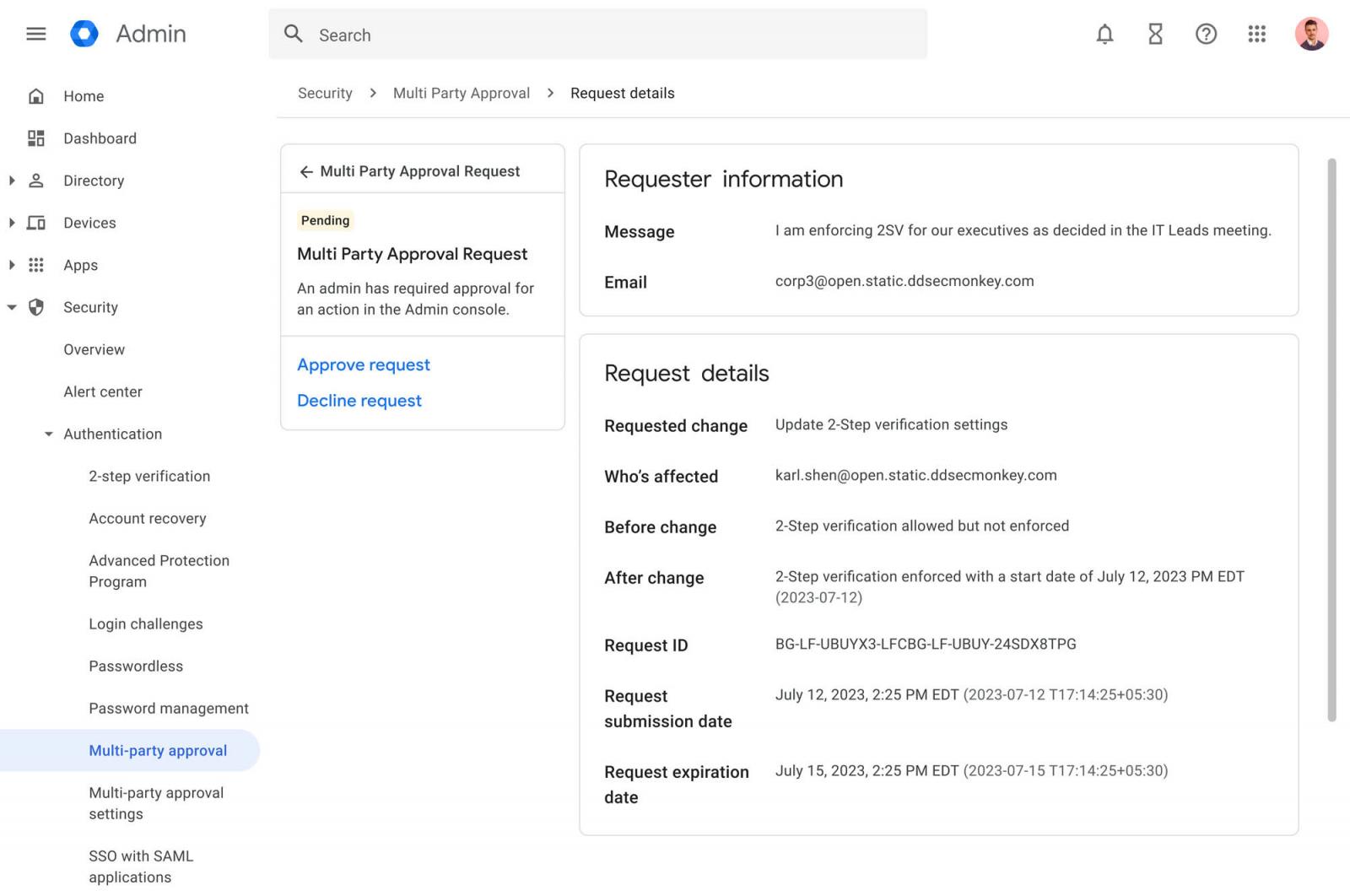
Prominently among these new capabilities is the ability to add an additional layer of protection that requires sensitive Google Workspace actions to be signed off by two admins.
After multi-party approval is enabled and configured on a workspace, admins must have at least one other admin confirm critical changes.
"Once it's been implemented, when an admin initiates a highly sensitive action like a 2SV settings change, any other admin can approve," Google Workspace Director of Product Management Andy Wen told BleepingComputer.
"With this initial framework release, we currently are supporting just 2SV settings change and expanding this capability to other actions based on admin feedback."
The company plans to preview multi-party approval for sensitive Google Workspace actions in the upcoming months.
Starting later this year, the company also plans to require mandatory 2-Step Verification (2SV), also known as two-factor authentication (2FA), for specific enterprise administrators.
"Compromised administrator accounts can have an outsized impact, and 2SV can result in a 50% decrease in accounts being compromised," Google's Yulie Kwon Kim and Andy Wen said.
"Starting later this year, in a phased approach, select administrator accounts of our resellers and largest enterprise customers will be required to add 2SV to their accounts to strengthen their security."
Google is also expanding its AI-powered Gmail defenses to cover more sensitive email actions, including message filtering and forwarding. This capability is now available in preview.
Lastly, Google Workspace now has an expedited pathway for exporting logs to Chronicle, Google's cloud-based Security Operations Suite. This will allow security teams and admins to export Workspace logs quicker to further improve threat response time.
"Social engineering attacks, such as phishing, are one of the most common entry points for data breaches," Kim and Wen said.
"Threat defense controls in Workspace help customers prevent, detect, and respond to social engineering and other identity-based attacks before they emerge.
Earlier this month, the company announced that it would soon make it easier to remove explicit personal images and personally identifiable information from search results using a privacy-focused tool announced in May 2022 that rolled out in September.
Google also explained how Android malware can slip into the Google Play Store with the help of a tactic known as versioning that enables malicious actors to evade the store's review process and security controls.


Comments
ZeroYourHero - 6 months ago
It's called TPI, which stands for "Two Person Integrity." The US military has employed this policy for many decades to handle sensitive materials.