
Compromising an employee's email account can be profitable for BEC scammers and for distributing malware, but being able to gain access to an email domain's administrator account is a jackpot. For this reason, it is important to be aware of phishing scams that are not targeting an organization's users, but rather their administrators.
Phishers targeting admins are becoming more popular due to the greater range of attacks than can be conducted through an admin account. With admin credentials, attackers can potentially create new accounts under an organizations domain, send mail as other users, and read others user's email.
To gain access to an administrator's account, phishers have started creating campaigns that are disguised as Office 365 admin alerts. These alerts will typically be about an time-sensitive issues that requires an admins immediate attention such as an issue with the mail service or unauthorized access being discovered
Office 365 Admin phishing emails
An example of a fake alert found by BleepingComputer is one that states an organization's Office 365 licenses have expired. The mail then proceeds to tell the user to login to the Office 365 Admin Center in order to check their payment information.
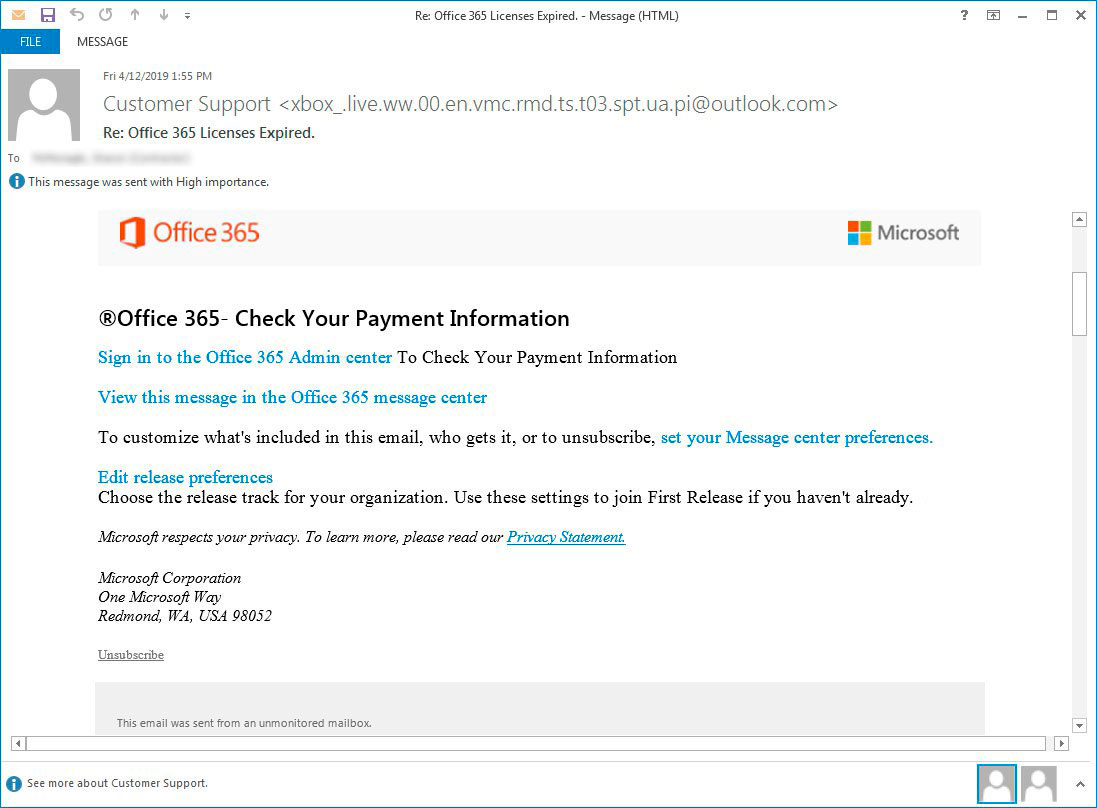
Another phishing email shared with us by Michael Gillespie pretends to be from Office 365 that is alerting the admin that someone has gained access to one of their user's email accounts. It then prompts the admin to "Investigate" the issue by logging in.
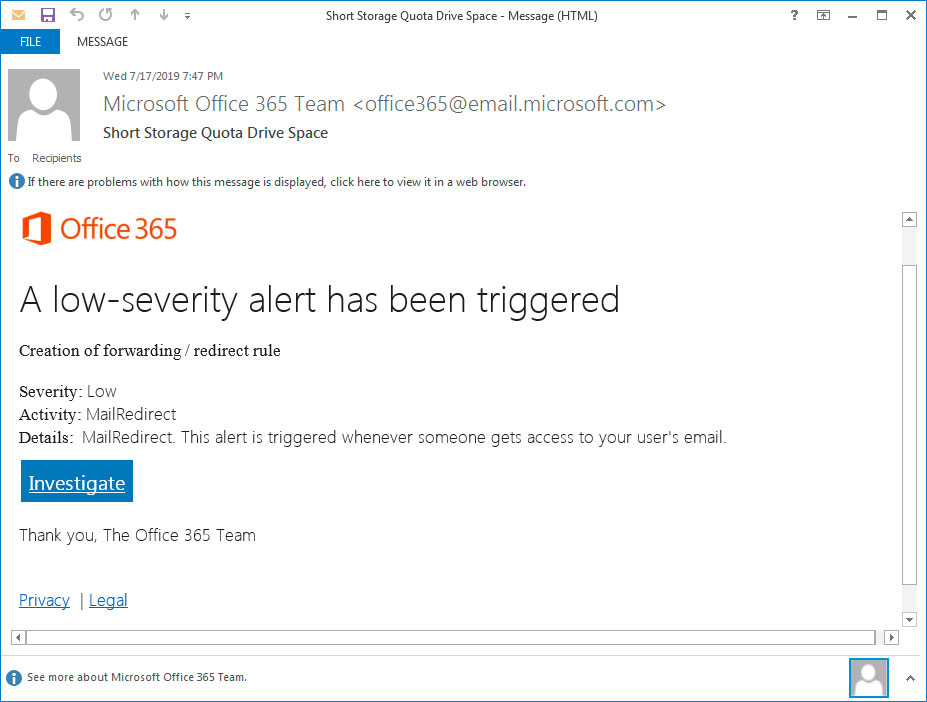
As expected, when you click on the the links in these emails you will be brought to a phishing landing page that prompts you to enter your Microsoft login credentials.
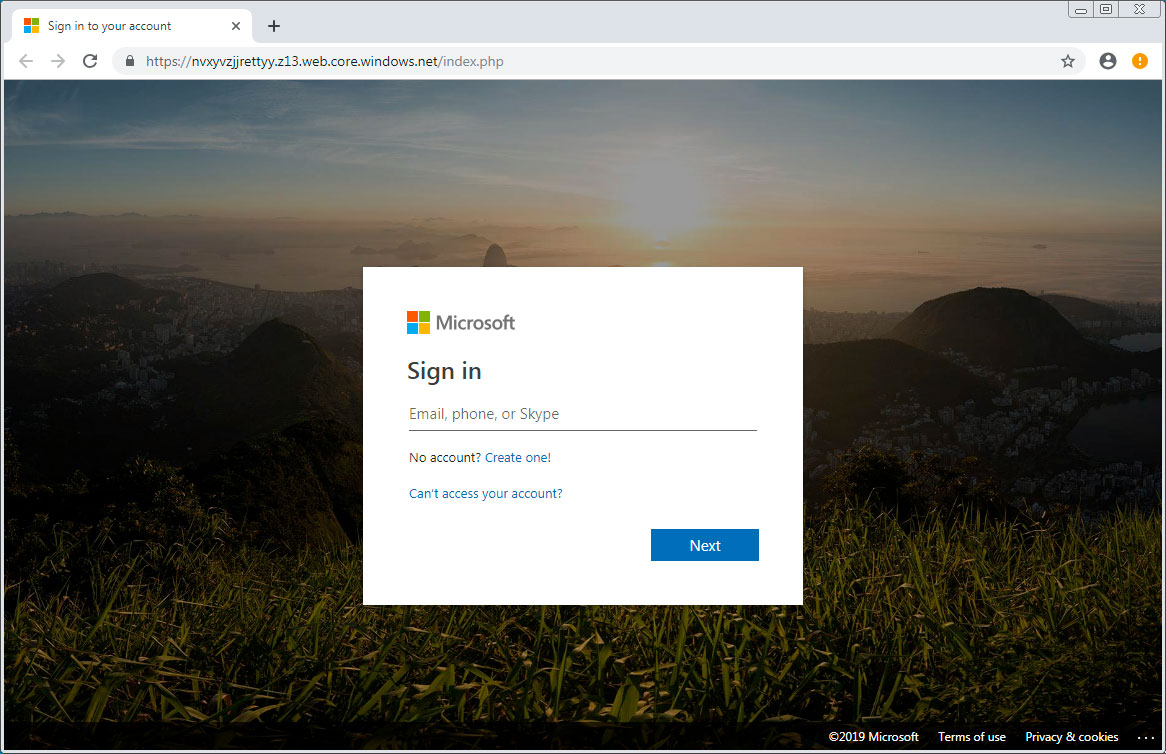
For example, the "Investigate" link in the email above will lead to a fake Microsoft login page hosted on the windows.net domain on Azure. Using Azure and a windows.net domain adds further legitimacy to the login.
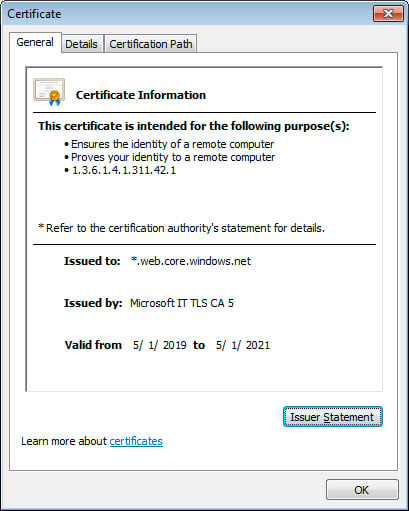
To make it more convincing, phishing pages hosted on Azure are secured using a certificate from Microsoft as shown below.
As you can imagine, if an admin falls for this scam and enters their credentials in the page they will be stolen by the attackers. Unless that account has some sort of 2-factor authentication enabled on it, the attacker would be able to gain access to the Office 365 admin portal.
Nobody falls for these scams, right?
You may be saying to yourself that no self-respecting admin would fall for these scams and I can hazard a guess that most do not.
Unfortunately, many network and mail admins are not properly trained to be IT Admins and were simply thrust into this position because the company couldn't afford a dedicated IT admin and nobody better was available.
For example, when I was a consultant, I regularly saw small law firms, accounting offices, and medical practices where the office manager or a partner was thrust into the admin role.
It's these types of admins that do not have adequate IT support and administration experience who can fall for these types of phishing scams.


Comments
jblyon - 4 years ago
I have a rule to delete any incoming emails that contain web.core.windows.net. For a while it forwarded flagged emails to admins for approval. 100% of emails received were phishing (or worse) so the rule just got set to dump the email. Unless you have some specific need to receive emails containing that string I highly recommend redirecting them to quarantine at a minimum.