A previously unknown cybercrime syndicate named 'Bigpanzi' has been making significant money by infecting Android TV and eCos set-top boxes worldwide since at least 2015.
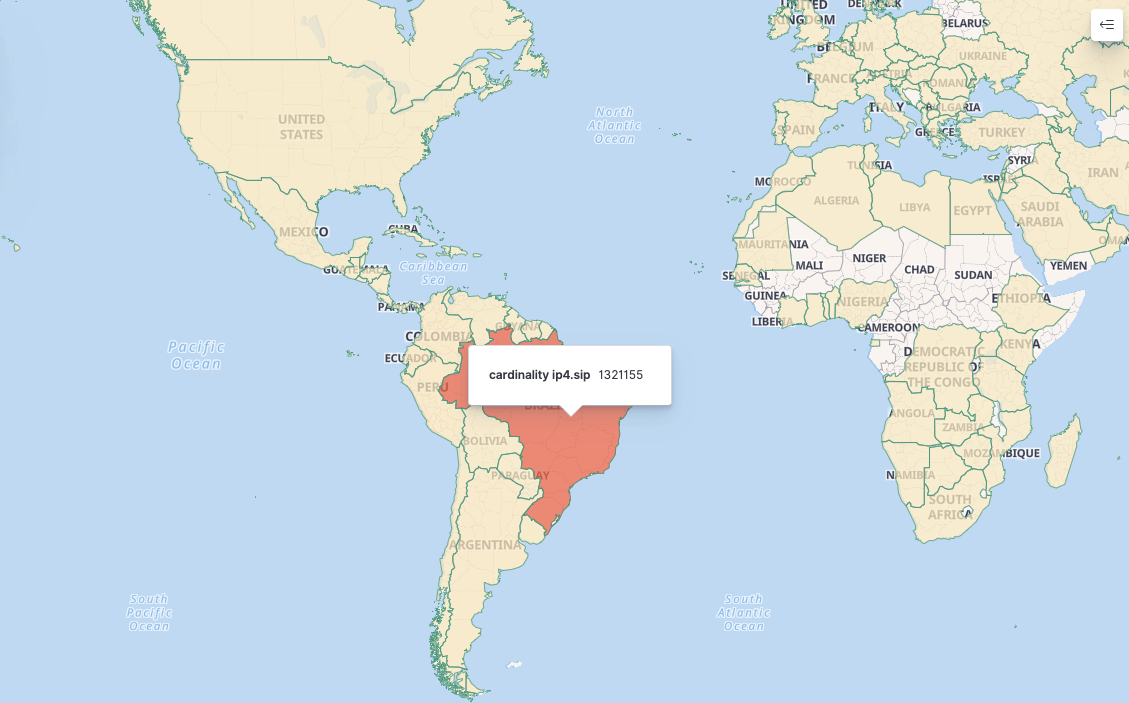
Beijing-based Qianxin Xlabs reports that the threat group controls a large-scale botnet of approximately 170,000 daily active bots. However, the researchers have seen 1.3 million unique IP addresses associated with the botnet since August, most in Brazil.
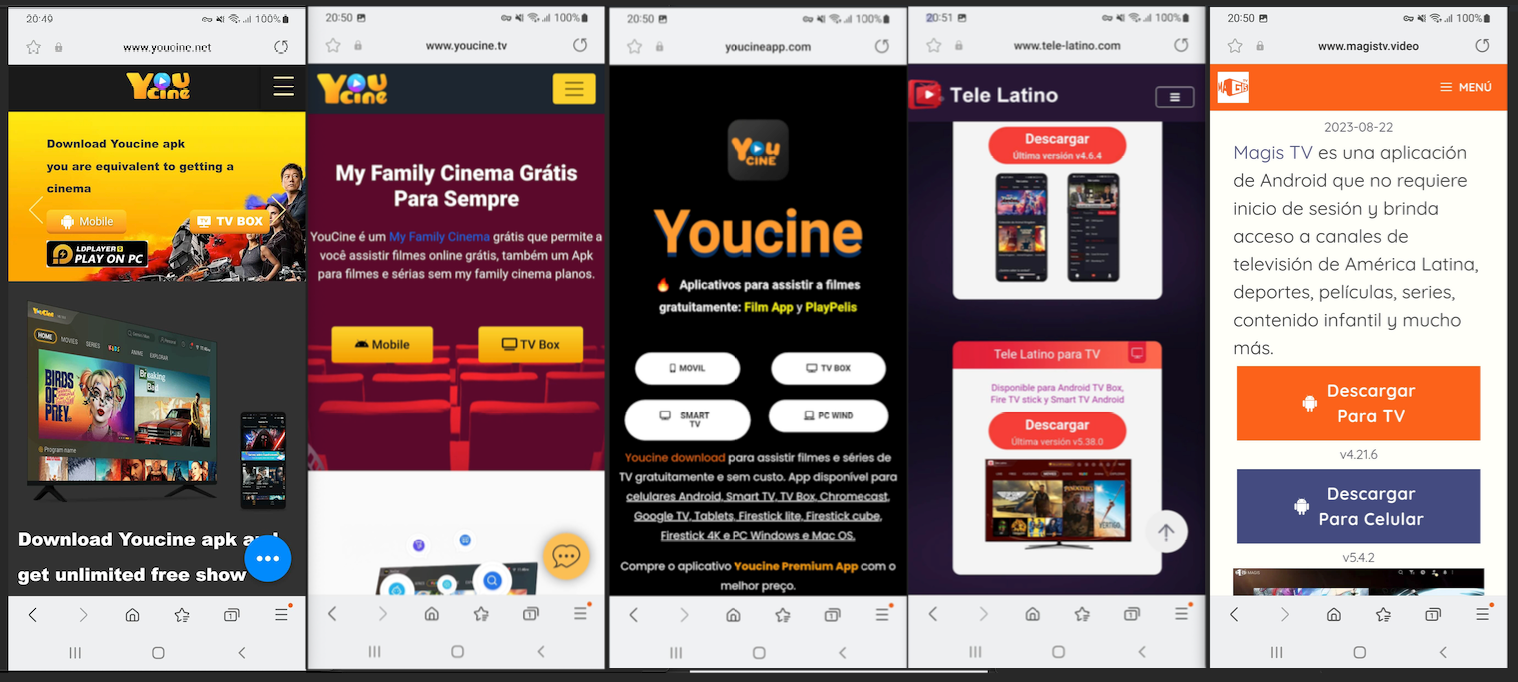
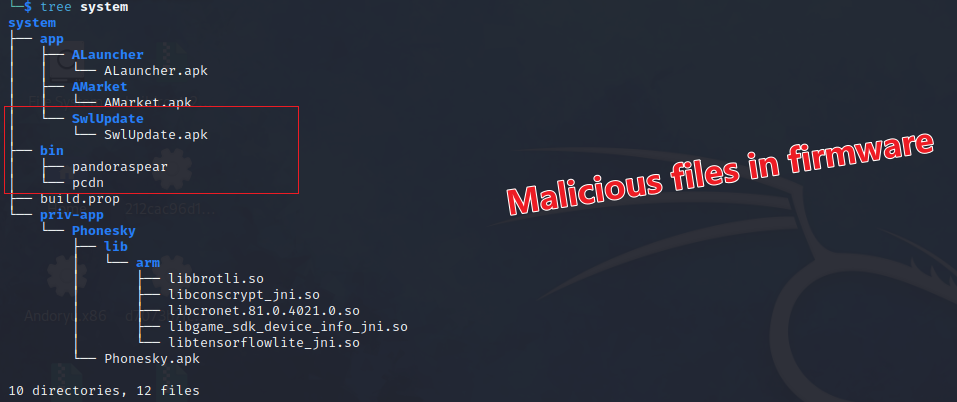
Bigpanzi infects the devices via firmware updates or backdoored apps the users are tricked into installing themselves, as highlighted in a September 2023 report by Dr. Web.
Source: Xlabs
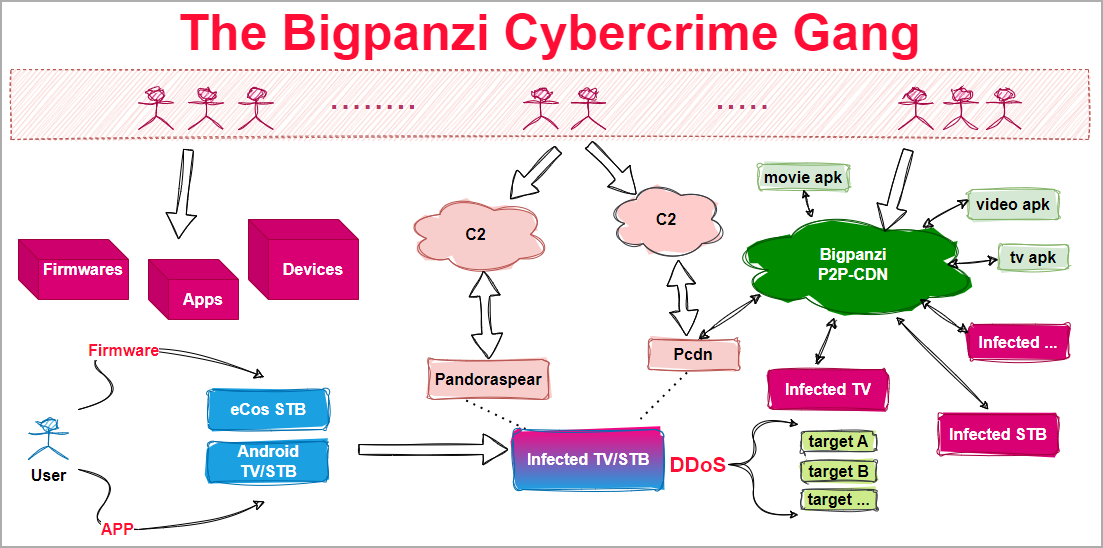
The cybercriminals monetize these infections by turning the devices into nodes for illegal media streaming platforms, traffic proxying networks, distributed denial of service (DDoS) swarms, and OTT content provision.
Source: Xlabs
Bigpanzi's custom malware
Xlabs' report focuses on 'pandoraspear' and 'pcdn,' two malware tools used by Bigpanzi in their operations.
Source: Xlabs
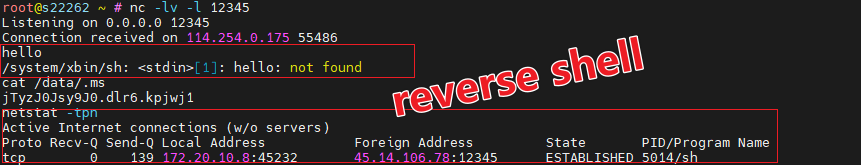
Pandoraspear acts as a backdoor trojan, hijacking DNS settings, establishing command and control (C2) communication, and executing commands received from the C2 server.
The malware supports a variety of commands that allow it to manipulate DNS settings, initiate DDoS attacks, update itself, create reverse shells, manage its communication with the C2, and execute arbitrary OS commands.
Source: Xlabs
Pandoraspear uses sophisticated techniques like modified UPX shell, dynamic linking, OLLVM compilation, and anti-debugging mechanisms to evade detection.
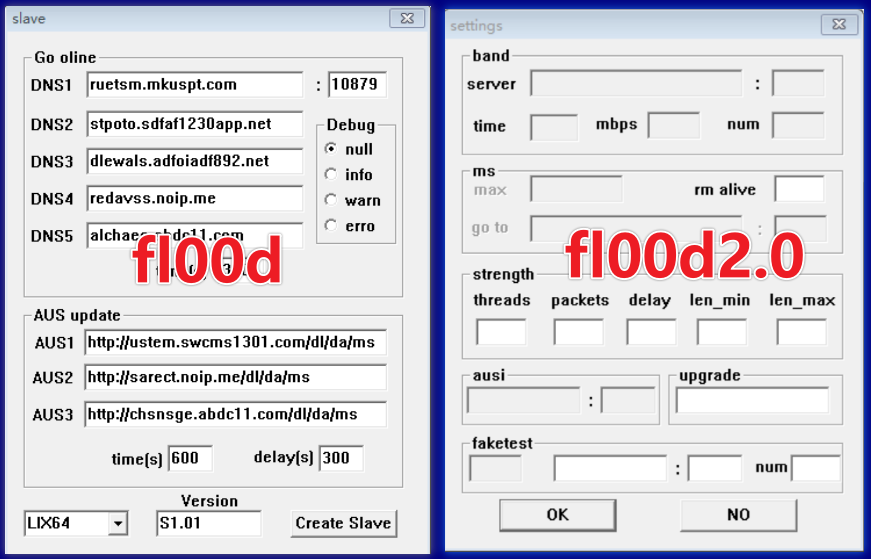
Pcdn is used to build a peer-to-peer (P2P) Content Distribution Network (CDN) on infected devices and possesses DDoS capabilities to weaponize devices.
Source: Xlabs
Scale of operations
Xlabs gained insight into the botnet's scale after hijacking two C2 domains used by the attackers and conducting a seven-day observation.
The analysts report that the Bigpanzi botnet has 170,000 daily bots at peak times and has observed over 1.3 million distinct IPs since August.
Source: Xlabs
However, due to the compromised TV boxes not being simultaneously active at all times and the cybersecurity analysts' visibility limitations, it is considered inevitable that the botnet's size is larger.
"Over the past eight years, Bigpanzi has been operating covertly, silently amassing wealth from the shadows," reads the Xlabs report.
"With the progression of their operations, there has been a significant proliferation of samples, domain names, and IP addresses."
"In the face of such a large and intricate network, our findings represent just the tip of the iceberg in terms of what Bigpanzi encompasses."
Artifacts in the analyzed pcdn sample have led the Chinese researchers to a suspicious YouTube channel controlled by a company.
However, the Xlabs report has not disclosed any attribution details yet, presumably reserving those for the applicable law enforcement authorities.
Update 1/19 - A Google spokesperson has sent BleepingComputer the following comment regarding the above:
These devices found to be infected appear to be Android Open Source Project (AOSP) devices, which means that anyone can download and modify the code.
Android TV is Google's operating system for smart TVs and streaming devices. It is proprietary, which means that only Google and its licensed partners can modify the code.
If a device isn't Play Protect certified, Google doesn’t have a record of security and compatibility test results. Play Protect certified Android devices undergo extensive testing to ensure quality and user safety.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now