
Japanese game developer Ateam has proven that a simple Google Drive configuration mistake can result in the potential but unlikely exposure of sensitive information for nearly one million people over a period of six years and eight months.
The Japanese firm is a mobile games and content creator, encompassing Ateam Entertainment, which has multiple games on Google Play like War of Legions, Dark Summoner, Hatsune Miku – Tap Wonder, and tools like Memory Clear | Game Boost Master, and Good Night's Sleep Alarm.
Earlier this month, Ateam informed users of its apps and services, employees, and business partners that on November 21, 2023, it discovered that it had incorrectly set a Google Drive cloud storage instance to "Anyone on the internet with the link can view" since March 2017.
The insecurely configured Google Drive instance contained 1,369 files with personal information on Ateam customers, Ateam business partners, former and current employees, and even interns and people who applied for a position at the company.
Ateam has confirmed that 935,779 individuals had their data exposed, with 98.9% being customers. For Ateam Entertainment specifically, 735,710 people have been exposed.
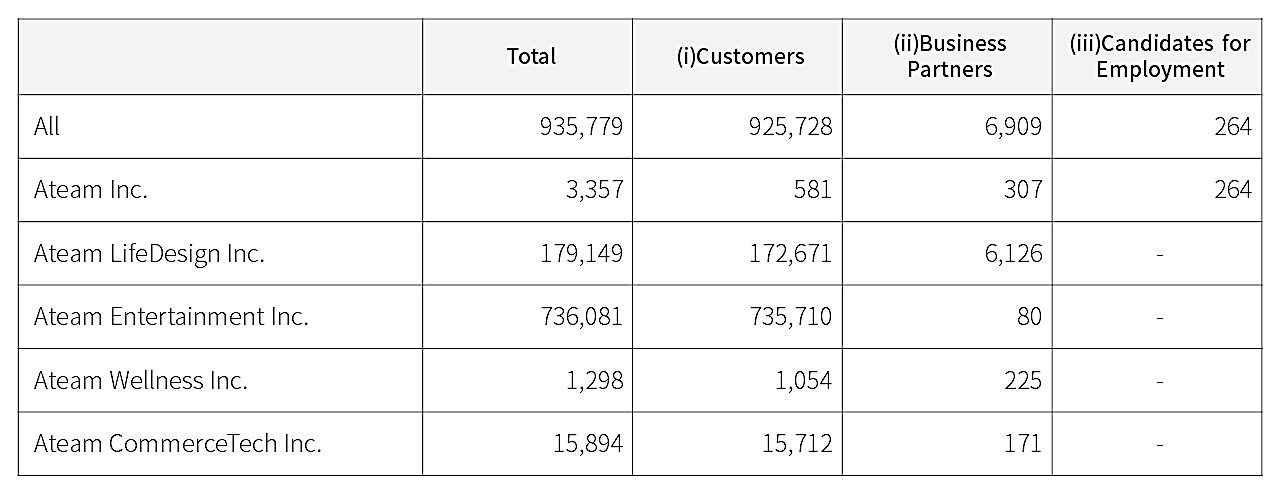
The data exposed by this misconfiguration varies depending on the type of relationship each individual had with the company and may include the following:
- Full names
- Email addresses
- Phone numbers
- Customer management numbers
- Terminal (device) identification numbers
The company says it has seen no concrete evidence of threat actors having stolen the exposed information but urges people to remain vigilant for unsolicited and suspicious communications.
Secure your cloud services
Setting Google Drive to "Anyone with the link can view" makes it viewable only to those with the exact URL, typically reserved for collaboration between people working with non-sensitive data.
If an employee, or someone else with the link, mistakenly exposed it publicly, it could get indexed by search engines and become broadly accessible.
While it's unlikely that anyone found an exposed Google Drive URL on their own, this notification demonstrates a need for companies to properly secure their cloud services to prevent data from being mistakenly exposed.
It is very common for threat actors and researchers to find exposed cloud services, such as databases and storage buckets, and download the data contained in them.
While researchers usually responsibly disclose the exposed data, if threat actors find it, it can lead to bigger problems as they use it to extort companies or sell it to other hackers to use in their own attacks.
In 2017, security researcher Chris Vickery found misconfigured Amazon S3 buckets exposing databases containing 1.8 billion social and forum posts made by users worldwide.
Ten days later, the same researcher discovered another misconfigured S3 bucket that exposed what appeared to be classified information from INSCOM.
While those breaches were responsibly disclosed, other cloud service misconfigurations have led to the data being leaked or sold on hacker forums.
Misconfigured Amazon S3 buckets have become a big enough problem that researchers have released tools that scan for exposed buckets.
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has also released guidance for companies on how to properly secure cloud services.


Comments
Eddiehsyr - 2 months ago
Somebody needs to tell these people about a category of security service known as an "API based CASB".
h_b_s - 2 months ago
I hesitate to draw conclusions from my own college experience because it may not be entirely typical. However, if it is then the majority of programmers coming out of coding boot camps, junior colleges and undergraduate programs aren't taught secure coding practices. Even basic programming logic was optional in some programs - it should be a hard requirement for all of them. Programmers aren't learning the basic skills to write secure systems, nor do the hordes of self taught coders have the skills. The tools they use are usually designed for convenience rather than having well thought out secured defaults. That's before it gets to the point where management may have de-prioritized security and privacy in service of greed over selling that data. Long winded way to say that the computer industry is almost universally ill equipped to deal with the modern computing landscape.
GT500 - 2 months ago
Misconfigured Google Drive, misconfigured Amazon bucket, misconfigured FTP... I mean, what's next? Misconfigured AI spilling all your company secrets?
XSp - 2 months ago
"Android game dev’s Google Drive misconfig highlights cloud security risks"
more like
"Android game dev’s Google Drive misconfig highlights complete incompetence when it comes to basic security measures from the game dev"