
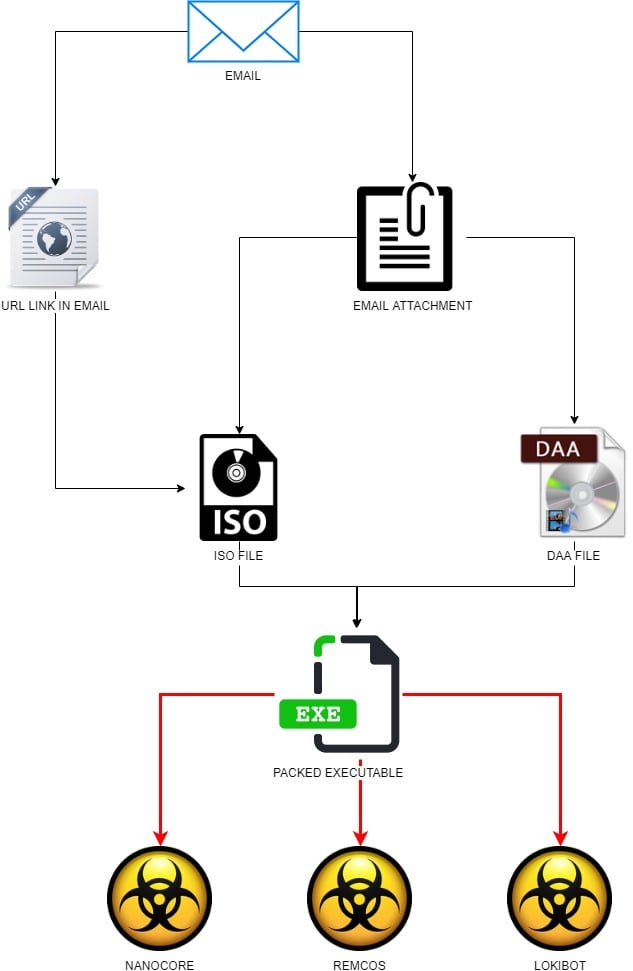
Security researchers analyzing malicious spam campaigns noticed an increase in delivering malware in disk image file formats, .ISO being the most prevalent.
Acting as an archive-like container, a disk image is typically a clone of a physical drive that can be mounted as a virtual disk to access data on it organized with the same file structure as the original.
Cybercriminals have been using this type of file for years but researchers at Trustwave say they observed an increase in malicious ISO this year.
Among the most popular threats delivered this way are remote access tools (NanoCore, Remcos) and LokiBot information stealer.
At 6% of all malicious attachments seen in 2019, the uptick is not spectacular but should be viewed with concern. Most secure email gateways block executable files and a malicious ISO can slip through.
Choosing ISO to deliver malware makes sense since Windows operating system has the ability to mount this file type when double-clicked. This allows scammers to disguise the threat as an innocent file.
In a recent campaign caught by Trustwave, cybercriminals created a fake FedEx shipment email message to trick recipients into downloading a malicious ISO that included an executable.
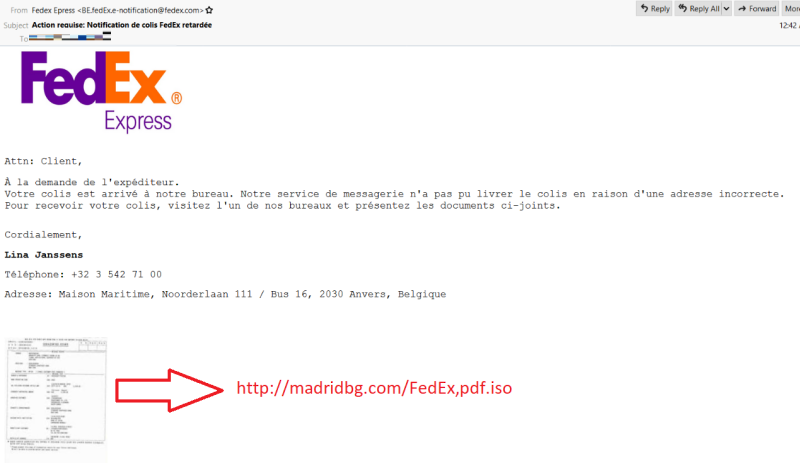
As visible in the image above, the link points to an ISO file that attempts to appear as a PDF. Inside the image was an executable for the NanoCore RAT.
At the time of the discovery, the image was marked malicious by 18 out of 70 antivirus engines on VirusTotal. NanoCore is not a new malware and normally it is easy to detect, yet packed this way lowered its detection.
It is unclear if it was a targeted attack but anyone that had indeed sent a package with FedEx would likely try to read the details in the fake PDF.
"The email was drafted in the French language, hence targeting French speakers. The lure was short and precise suggesting failure to deliver a FedEx parcel due to incorrect address, while guiding the victim to download the attached document from FedEx to update their address" - Trustwave
ISO is not the only image file abused this way. In what appears to be a targeted attack, the cybercriminals sent invoice-themed emails with an attachment in DAA (Direct Access Archive) format.
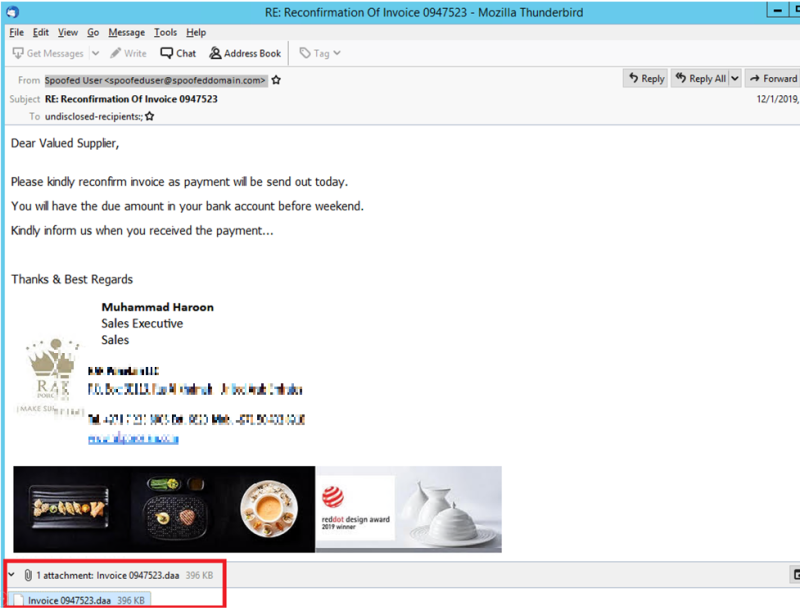
The payload, in this case, was the professional version of another remote access tool called Remcos, known for being used in cybercriminal activities.
Unlike ISO, the DAA type of image needs specialized software to be mounted and get to the files within, indicating that the crooks knew that the recipient had the necessary application installed.
According to Trustwave, the DAA images in this campaign contained a single executable with either .COM or .EXE extension, which the researchers determined to be Remcos RAT v2.5.0 Pro.
Based on observations this year, Trustwave believes that cybercriminals have started to experiment more with disk image archives to conceal their malware in a way that slips past security solutions.
With ISO being more popular and easier to unpack, threat actors tend to turn to it rather than other formats that require proprietary software to mount.
However, Trustwave believes that ISO is used for wider attacks that do not focus on a particular victim. DAA and similar image formats that require additional tools to open are reserved for targeted attacks.
The cloaking provided by disk image formats against antivirus solutions has been analyzed earlier this year by other security researchers that tested malware in tiny VHD files. In an experiment with Agent Tesla info-stealer encased in a 7MB VHD, detection rates were negligible.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now