
Hackers are exploiting a server-side request forgery (SSRF) vulnerability in Ivanti Connect Secure, Policy Secure, and ZTA gateways to deploy the new DSLog backdoor on vulnerable devices.
The vulnerability, tracked as CVE-2024-21893, was disclosed as an actively exploited zero-day on January 31, 2024, with Ivanti sharing security updates and mitigation advice.
The flaw impacts the SAML component of the mentioned products and allows attackers to bypass authentication and access restricted resources on Ivanti gateways running versions 9.x and 22.x.
The updates that fix the problem are Ivanti Connect Secure versions 9.1R14.4, 9.1R17.2, 9.1R18.3, 22.4R2.2, 22.5R1.1 and 22.5R2.2, Ivanti Policy Secure version 22.5R1.1, and ZTA version 22.6R1.3.
On February 5, 2024, threat monitoring service Shadowserver reported seeing multiple attackers attempting to leverage the flaw, some using proof-of-concept (PoC) exploits previously published by Rapid7, with the success rate being unknown at the time.
A new report by Orange Cyberdefense confirms the successful exploitation of CVE-2024-21893 to install a new backdoor named DSLog that allows the threat actors to execute commands on compromised Ivanti servers remotely.
Orange says they first spotted this new backdoor on February 3, 2024, after analyzing a compromised appliance that had implemented the Ivanti-proposed XML mitigation (blocking all API endpoints) but hadn't applied the patch.
The DSLog backdoor
By examining the compromised Invanti device's logs, Orange researchers found a backdoor had been injected into the appliance's code base by issuing SAML authentication requests containing encoded commands.
These commands executed operations like outputting system information to a publicly accessible file (index2.txt), indicating that the attackers aimed to perform internal reconnaissance and confirm their root access.
Subsequent SAML requests showed attempts to secure read/write filesystem permissions on the breached device, detect modifications to a legitimate logging script (DSLog.pm), and injecting the backdoor if the string indicating the modification is missing.
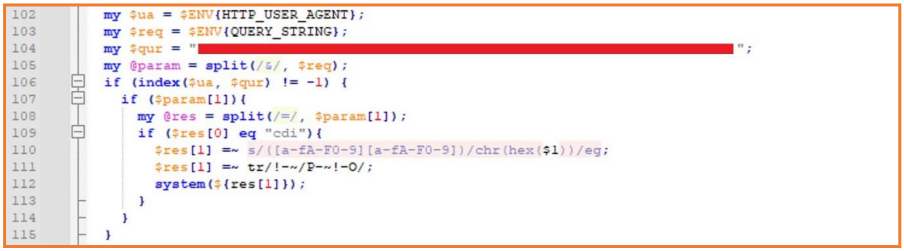
The backdoor is inserted into the DSLog file, responsible for logging various types of authenticated web requests and system logs.
The attackers employed a unique SHA256 hash per appliance as an API key, requiring this hash in the HTTP User-Agent header for command execution. Orange explains that no hash can be used to contact the same backdoor on another device.
The backdoor's main functionality is to execute commands as root. Orange says the DSLog backdoor can run "any commands" on the breached device received via HTTP requests by the attackers, with the command included in a query parameter named 'cdi.'
The HTTP requests carry the specific SHA256 hash that matches the contacted device, which doubles as a key to authenticate the request to the backdoor.
The researchers note that because the webshell does not return status/code when attempting to contact it, it is particularly stealthy.
Orange was also unable to determine the scheme used for the SHA256 hash calculation and noted that '.access' logs were wiped on multiple compromised appliances to hide the attackers' activities.
Despite that, the researchers uncovered nearly 700 compromised Ivanti servers by looking at other artifacts, such as the 'index' text files in the 'hxxp://{ip}/dana-na/imgs/' directory.
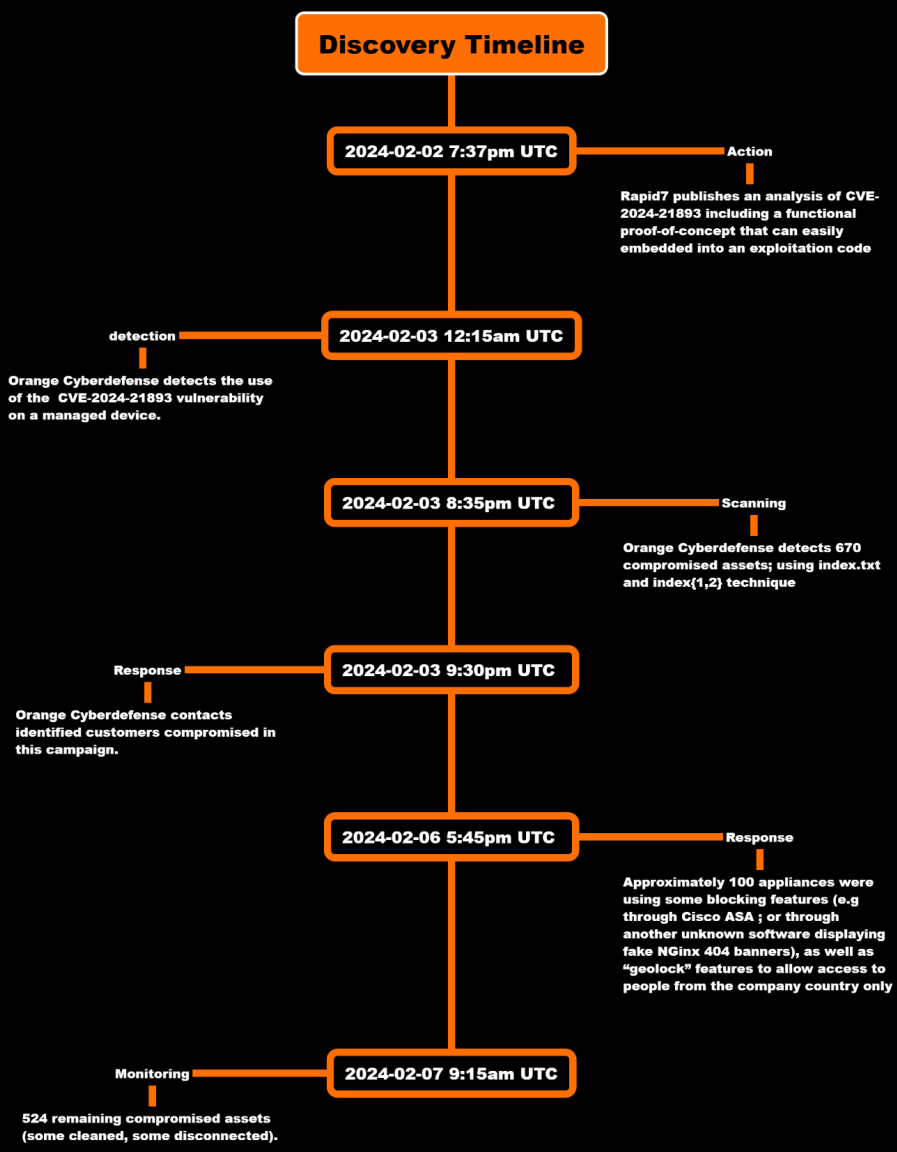
Roughly 20% of these endpoints were already affected by earlier campaigns, while others were vulnerable only due to the lack of additional patches or mitigations.
It is recommended to follow the latest recommendations by Ivanti to mitigate all threats targeting the vendor's products leveraging this SSRF or any of the other recently disclosed vulnerabilities impacting Ivanti devices.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now