
Microsoft says that a group of Iranian-backed state hackers are targeting high-profile employees of research organizations and universities across Europe and the United States in spearphishing attacks pushing new backdoor malware.
The attackers, a subgroup of the notorious APT35 Iranian cyberespionage group (also known as Charming Kitten and Phosphorus) linked to the Islamic Revolutionary Guard Corps (IRGC), sent custom-tailored and difficult-to-detect phishing emails via previously compromised accounts while masquerading as various high-profile individuals, including journalists at reputable news outlets.
"Since November 2023, Microsoft has observed a distinct subset of Mint Sandstorm (PHOSPHORUS) targeting high-profile individuals working on Middle Eastern affairs at universities and research organizations in Belgium, France, Gaza, Israel, the United Kingdom, and the United States," Microsoft said.
"In this campaign, Mint Sandstorm used bespoke phishing lures in an attempt to socially engineer targets into downloading malicious files. In a handful of cases, Microsoft observed new post-intrusion tradecraft including the use of a new, custom backdoor called MediaPl."
The MediaPl malware uses encrypted communication channels to exchange information with its command-and-control (C2) server and is designed to masquerade as Windows Media Player to evade detection.
Communications between MediaPl and its C2 server use AES CBC encryption and Base64 encoding, and the variant discovered on compromised devices comes with the ability to auto-terminate, temporarily halt, retry C2 communications, and execute C2 commands using the _popen function.
A second PowerShell-based backdoor malware known as MischiefTut helps drop additional malicious tools and provides reconnaissance capabilities, allowing the threat actors to run commands on the hacked systems and send the output to attacker-controlled servers.
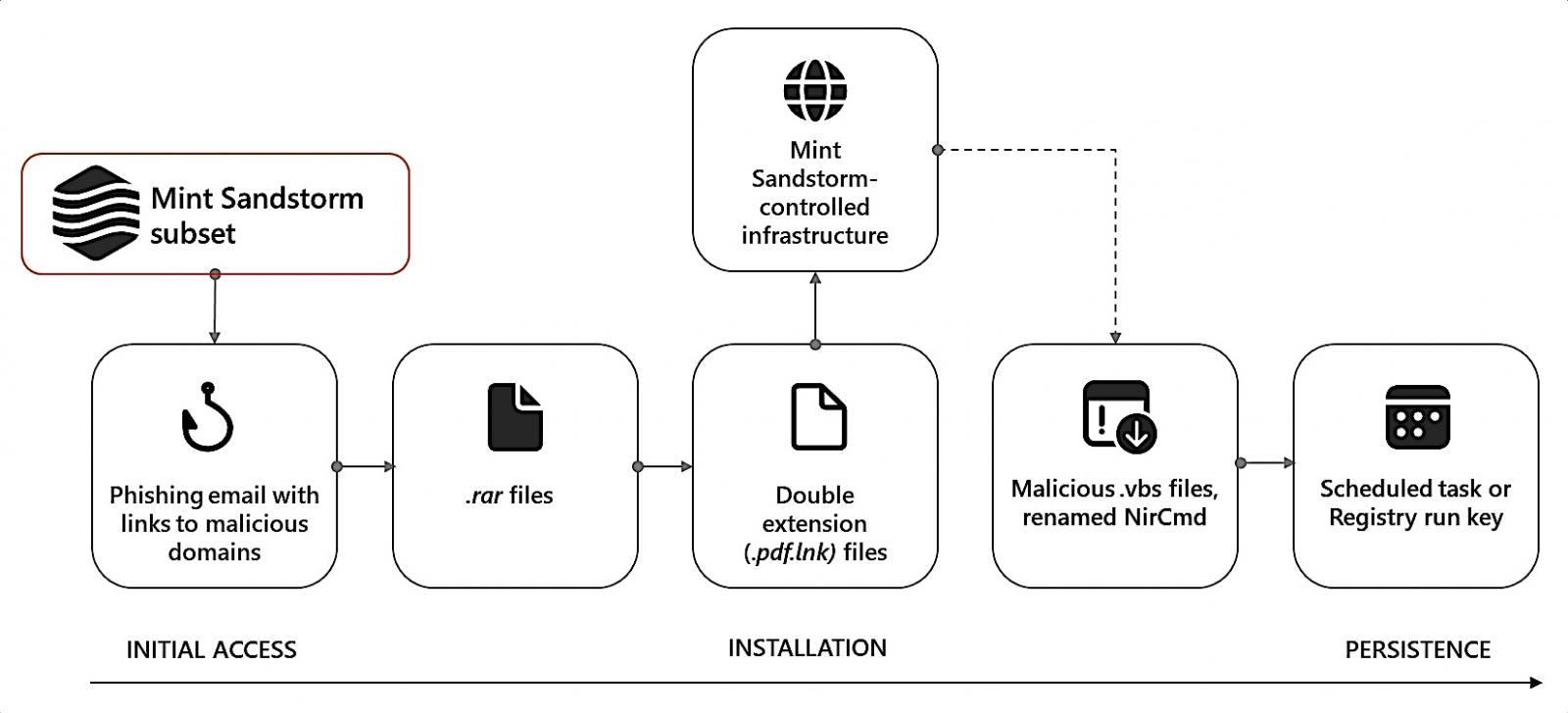
This APT35 subset focuses on attacking and stealing sensitive data from the breached systems of high-value targets. It is known for previously targeting researchers, professors, journalists, and other individuals with knowledge of security and policy issues aligning with Iranian interests.
"These individuals, who work with or who have the potential to influence the intelligence and policy communities, are attractive targets for adversaries seeking to collect intelligence for the states that sponsor their activity, such as the Islamic Republic of Iran," Microsoft said.
"Based on the identities of the targets observed in this campaign and the use of lures related to the Israel-Hamas war, it's possible this campaign is an attempt to gather perspectives on events related to the war from individuals across the ideological spectrum."
Between March 2021 and June 2022, APT35 backdoored at least 34 companies with previously unknown Sponsor malware in a campaign that targeted government and healthcare organizations, as well as firms in the financial services, engineering, manufacturing, technology, law, telecommunications, and other industry sectors.
The Iranian hacking group also used never-before-seen NokNok malware in attacks against macOS systems, another backdoor designed to collect, encrypt, and exfiltrate data from compromised Macs.
Another Iranian threat group tracked as APT33 (aka Refined Kitten or Holmium) breached defense organizations in extensive password spray attacks targeting thousands of orgs worldwide since February 2023 and was also recently seen attempting to breach defense contractors with new FalseFont malware.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now