
A new APT hacking group named 'AtlasCross' targets organizations with phishing lures impersonating the American Red Cross to deliver backdoor malware.
Cybersecurity firm NSFocus identified two previously undocumented trojans, DangerAds and AtlasAgent, associated with attacks by the new APT group.
NSFocus reports that the AtlasCross hackers are sophisticated and evasive, preventing the researchers from determining their origin.
"After an in-depth study of the attack process, NSFOCUS Security Labs found that this APT attacker is quite different from known attacker characteristics in terms of execution flow, attack technology stack, attack tools, implementation details, attack objectives, behavior tendency and other main attribution indicators," explains NSFocus.
"The technical level and cautious attitude shown by this attacker during this activity are also worthy of attention."
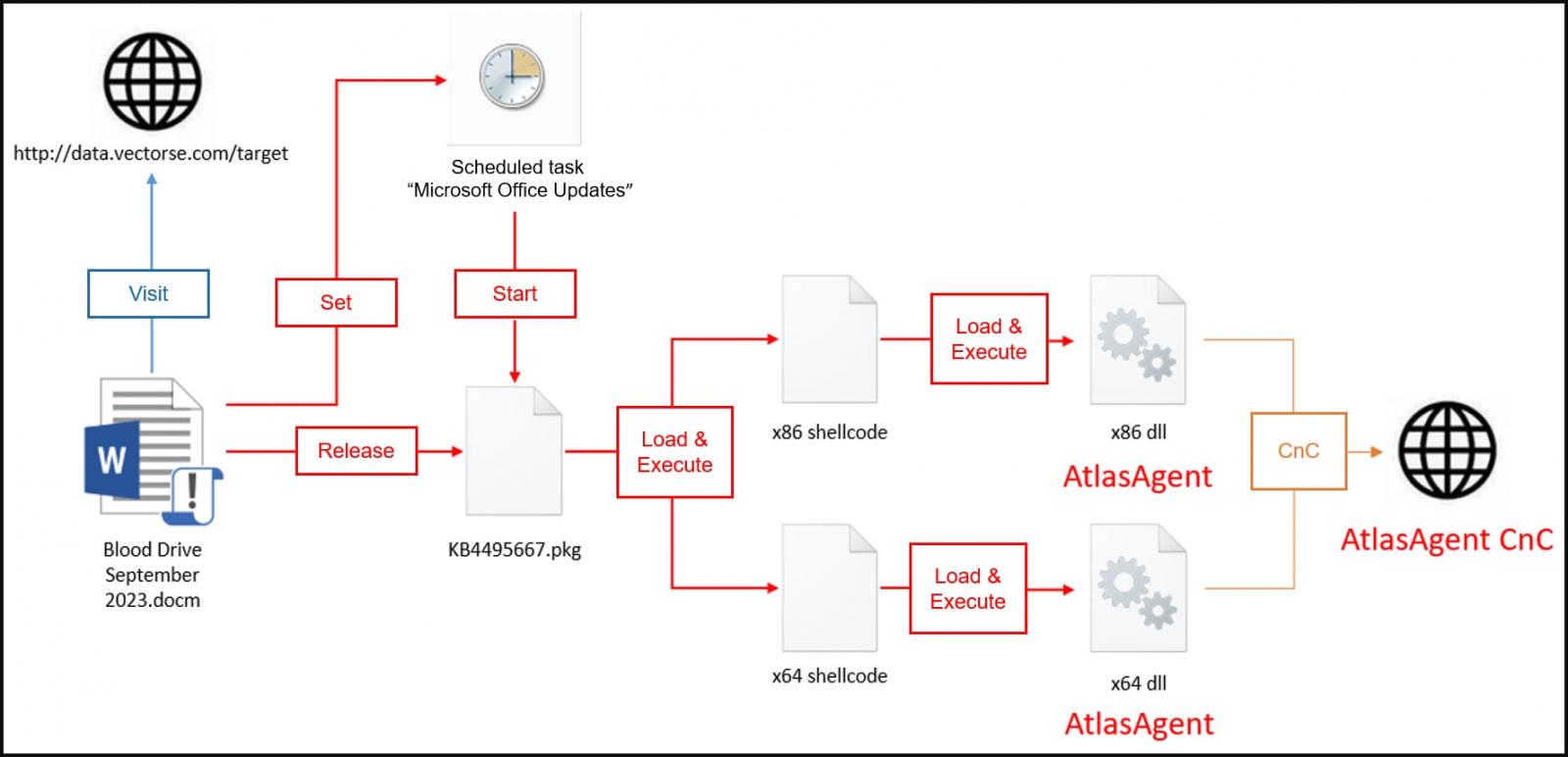
AtlasCross attack chain
AtlassCross attacks begin with a phishing message pretending to be from the American Red Cross, requesting the recipient to participate in a "September 2023 Blood Drive."
These emails contain a macro-enabled Word document (.docm) attachment that urges the victim to click "Enable Content" to view the hidden content.
However, doing so will trigger malicious macros that infect the Windows device with the DangerAds and AtlasAgent malware.

The macros first extracts a ZIP archive on the Windows device to drop a file named KB4495667.pkg, which is the DangerAds system profiler and malware loader. A scheduled task named "Microsoft Office Updates" is created to launch DangerAds daily for three days.
DangerAds functions as a loader, assessing the host environment and running built-in shellcode if specific strings are found in the system's username or domain name, an example of AtlasCross's narrow targeting scope.
Eventually, DangerAds loads x64.dll, which is the AtlasAgent trojan, the final payload delivered in the attack.
AtlasAgent details
AtlasAgent is a custom C++ trojan and its core functions include extracting host and process details, preventing the launch of multiple programs, executing additional shellcode on the compromised machine, and downloading files from the attacker's C2 servers.
Upon first launch, the malware sends information to the attacker's servers, including local computer name, network adapter information, local IP address, network card info, OS system architecture and version, and a running process list.
The attacker's servers will then respond with commands for AtlasAgent to execute, which can be done using new threads or within one of the existing processes, making it harder for security tools to detect and stop.
Moreover, AtlasAgent supports the following commands:
- Obtain computer system information
- Reverse Shell
- Obtain data from CnC and store it in the specified file
- Debugging field
- Pause the program for a period of time using the Sleep function
- Obtain process information
- Inject shellcode into a new thread of the specified process
- Parameter function is to be implemented.
- Run shellcode directly; or create a thread to run shellcode in this process
- Break out of circulation
- Inject shellcode or command into a thread in the specified process
- Create a mutex
- Exit cycle
While NSFocus' report is the first detailing the new hacking group, AtlasCross remains a largely unknown threat that operates on unclear motives and obscure targeting scope.
The threat actor's selective targeting, custom-made trojans, and malware loaders, combined with a preference for discreet infection methods over efficiency, have allowed them to operate undetected for an undefined duration.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now