
A Chinese APT hacking group known as 'Evasive Panda' is linked to a mysterious attack that distributed the MsgBot malware as part of an automatic update for the Tencent QQ messaging app.
Evasive Panda is a cyberespionage group active since at least 2012 that has previously targeted organizations and individuals in mainland China, Hong Kong, Macao, Nigeria, and various countries in Southeast and East Asia.
The threat actor's latest campaign was discovered by security researchers of ESET in January 2022, who report seeing signs that the operation began back in 2020.
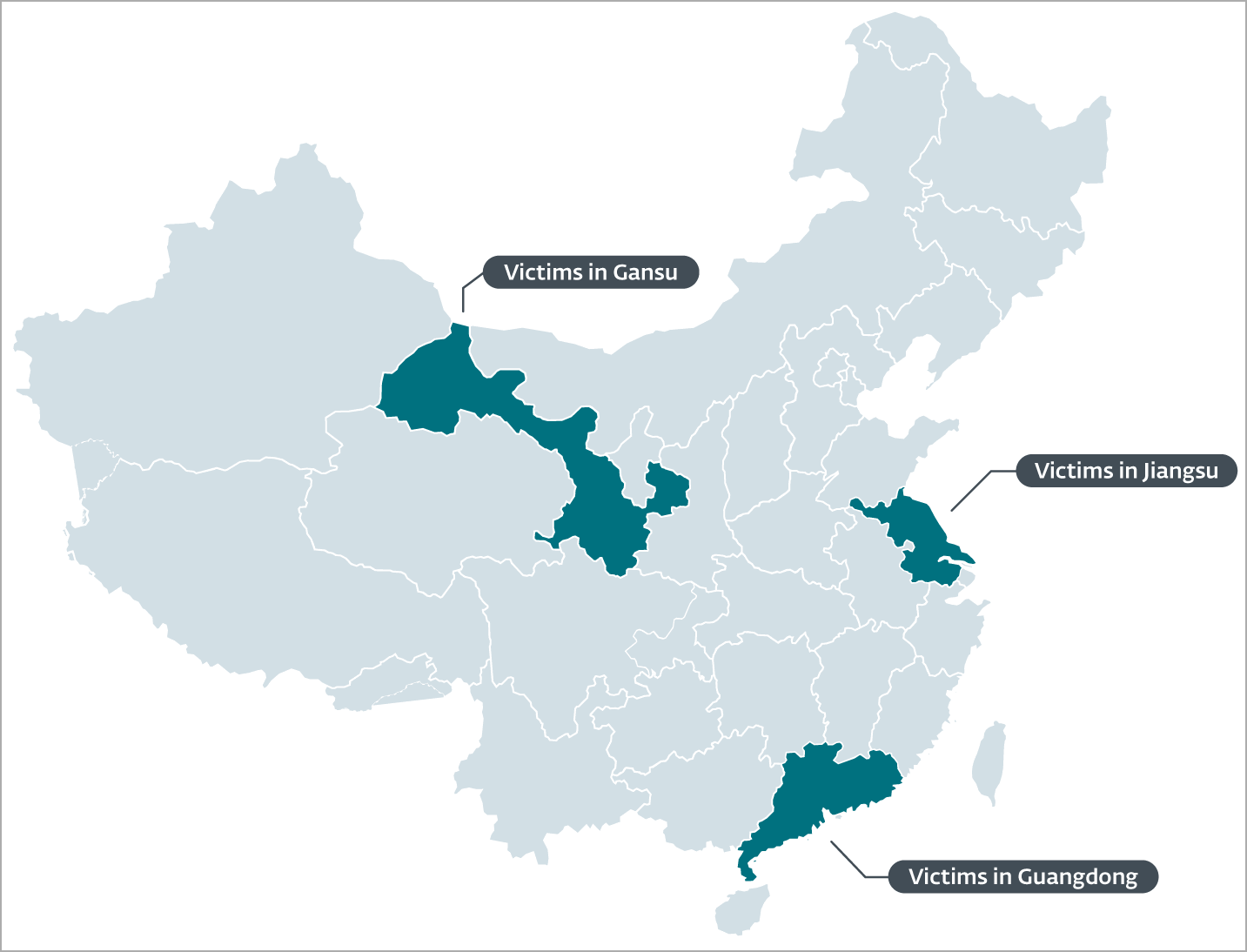
Most of the campaign's victims are members of an international NGO (non-governmental organization) and are located in the provinces of Gansu, Guangdong, and Jiangsu, indicating a rather specific and focused targeting.
Supply chain or AITM?
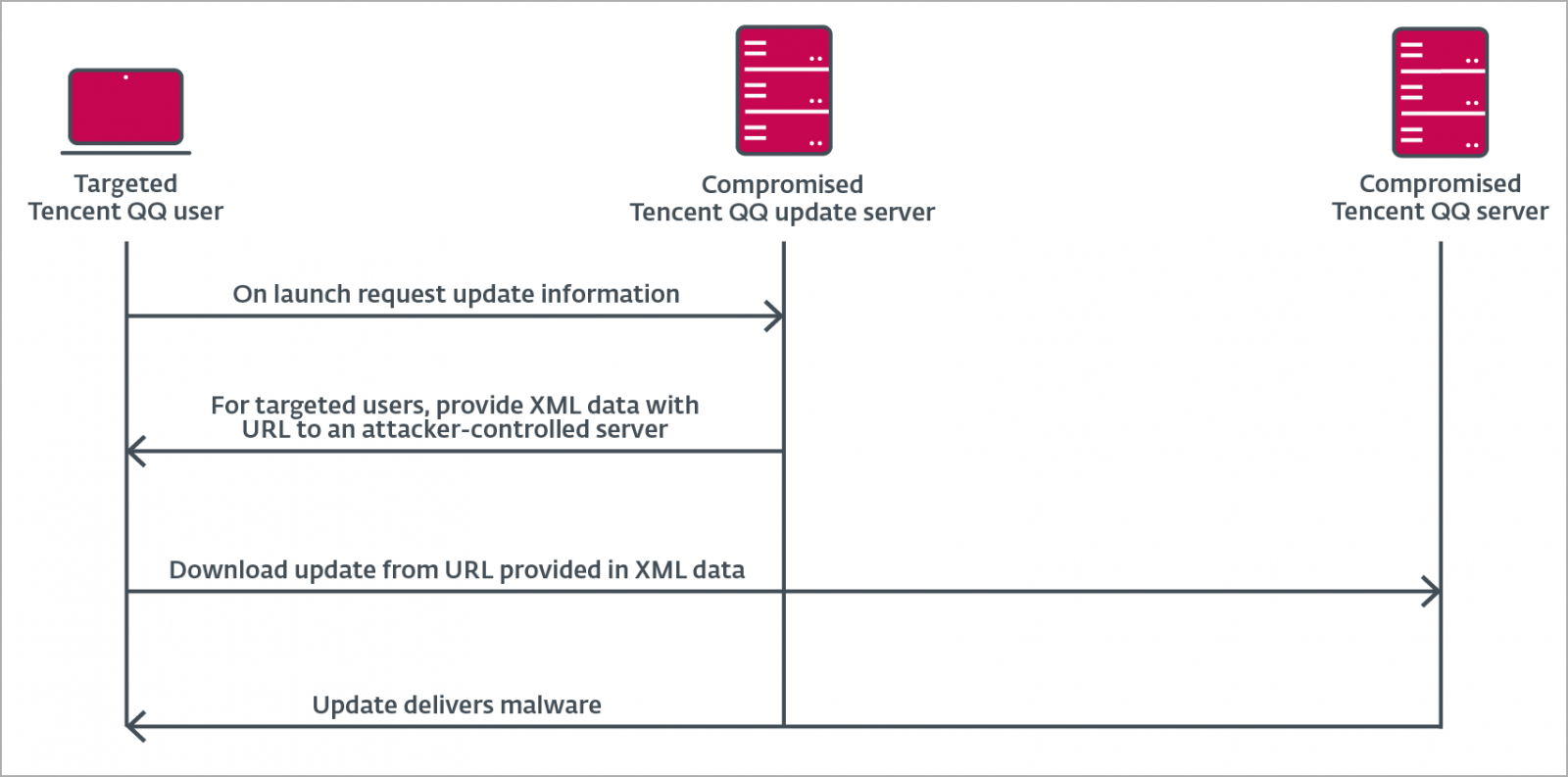
ESET reports that the malicious MsgBot malware payload was delivered to victims as a Tencent QQ software update from legitimate URLs and IP addresses belonging to the software developer.
This means there can be two possible scenarios for the attack - a supply chain attack or an adversary-in-the-middle (AITM) attack.
In the first scenario, Evasive Panda would have to breach into Tencent QQ's update distribution servers to trojanize the 'QQUrlMgr.exe' file delivered to victims under the guise of a legitimate software update.
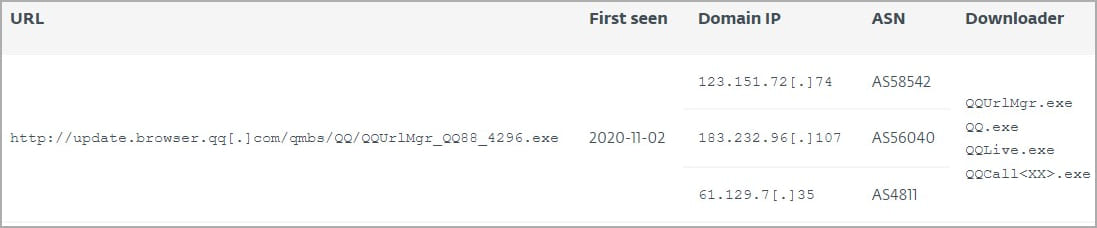
ESET noticed that the trojanized versions of the updater file fetch the malware from a hardcoded URL (“update.browser.qq[.]com”) and use a hardcoded decryption key that matches the correct MD5 hash provided by the server. However, the legitimacy of this URL has yet to be validated, and Tencent did not respond to ESET's question.
Also, the analysts could not retrieve a sample of the XML update data from the server, which would reveal the malware delivery mechanism.
In an AiTM scenario, ESET noticed some striking similarities with past campaigns employing this tactic, including one of the LuoYu APT that Kaspersky highlighted in a 2022 report.
That older campaign employed' WinDealer' malware that generated random IP addresses from China Telecom to perform AITM or attacker-on-the-side interception. Those IPs appear to be on the same ranges as those that delivered the MgBot malware in the Evasive Panda campaign.
While both scenarios are plausible based on the observed coincidences and the possible explanations, ESET could not find evidence that points to a clear direction, and many questions remain unanswered.
BleepingComputer contacted both ESET and Tencent with further questions about the attack.
The MgBot malware
The MgBot payload delivered in this campaign is a C++ Windows backdoor that Evasive Panda has been using since the beginning of its operations in 2012.
ESET reports that the malware's installer, backdoor, functionality, and execution chain have remained largely unchanged since Malwarebytes analyzed them in 2020.
MgBot uses a modular architecture to extend its functionality, receiving DLL plugins from the C2 that perform specialized functions, including:
- Keylogging on specific Tencent apps
- Stealing files from hard drives and USB pen drives
- Capturing text copied to the clipboard
- Capturing input and output audio streams
- Stealing credentials from Outlook and Foxmail email clients
- Stealing credentials from Chrome, Opera, Firefox, Foxmail, QQBrowser, FileZilla, WinSCP, and more
- Stealing the content of the Tencent QQ database that stores the user's message history
- Stealing information from Tencent WeChat
- Stealing cookies from Firefox, Chrome, and Edge
In conclusion, the Evasive Panda APT was found targeting users in China, aiming to steal data mostly from Chinese apps, leveraging an unclear method to perform a supply chain attack on Tencent QQ software.
This is a characteristic example of the group's high-level capabilities that go beyond standard infection methods like social engineering, phishing, SEO poisoning, etc., and calls for greater vigilance from potential targets.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now