
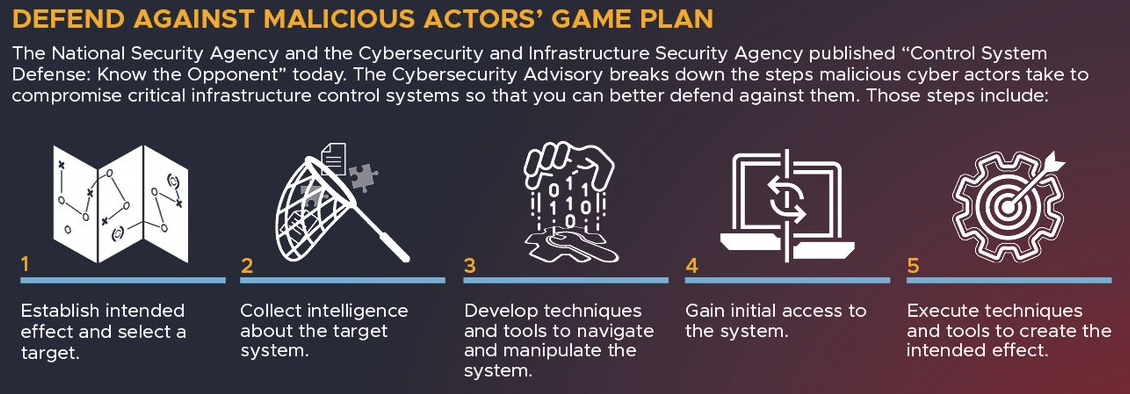
The National Security Agency (NSA) and CISA have issued guidance on how to secure operational technology (OT) and industrial control systems (ICSs) part of U.S. critical infrastructure.
The joint advisory shares info on all the steps used by malicious actors to compromise IT-enabled OT and ICS assets which provide a larger attack surface and highlights measures security professionals can take to defend against them.
"Cyber actors, including advanced persistent threat (APT) groups, have targeted OT/ICS systems in recent years to achieve political gains, economic advantages, and possibly to execute destructive effects. Recently, they've developed tools for scanning, compromising, and controlling targeted OT devices," the NSA said.
The advisory also "notes the increasing threats to OT and ICS assets that operate, control, and monitor day-to-day critical infrastructure and industrial processes. OT/ICS designs are publicly available, as are a wealth of tools to exploit IT and OT systems."
In today's advisory [PDF], you can find detailed information on how to block threat actors' attacks at every step, including attempts to collect intelligence, gain initial access, or deploy and execute malicious tools in compromised critical infrastructure systems.
Mitigation measures
However, some defenders may be unable to implement some of the recommended security strategies that could help mitigate many common tactics used to target critical infrastructure control systems.
For them, NSA and CISA provide some security best practices to counter adversaries' tactics, techniques and procedures (TTPs):
- Limit exposure of system information: Operational and system information and configuration data are crucial elements of critical infrastructure operations. The importance of keeping such data confidential cannot be overstated.
- Identify and secure remote access points: Owner/operators must maintain detailed knowledge of all installed systems, including which remote access points are—or could be—operating in the control system network. Creating a full "connectivity inventory" is a critical step in securing access to the system.
- Restrict tools and scripts: Limit access to network and control system application tools and scripts to legitimate users performing legitimate tasks on the control system. Removing the tools and scripts entirely and patching embedded control system components for exploitable vulnerabilities is often not feasible. Thus, carefully apply access and use limitations to particularly vulnerable processes and components to limit the threat.
- Conduct regular security audits: Such an audit aims to identify and document system vulnerabilities, practices, and procedures that should be eliminated to improve the cyber defensive posture and ultimately prevent malicious cyber actors from being able to cause their intended effects.
- Implement a dynamic network environment: A little change can go a long way to disrupt previously obtained access by a malicious actor.
"It is vital for OT/ICS defenders to anticipate the TTPs of cyber actors combining IT expertise with engineering know-how," the two federal agencies added.
"Defenders can employ the mitigations listed in this advisory to limit unauthorized access, lock down tools and data flows, and deny malicious actors from achieving their desired effects."
Broader government effort to secure U.S. critical infrastructure
Today's advisory builds on previous guidance from 2021 for stopping malicious attacks targeting OT control systems and from 2020 on how to defend Internet-exposed OT assets.
It also comes after several initiatives spearheaded by the Biden administration recently to boost and upgrade critical infrastructure security.
For instance, in July 2021, a national security memorandum instructed CISA and NIST to develop cybersecurity performance goals and guidance for critical infrastructure owners and operators to help strengthen the security of U.S. critical infrastructure.
In April, Five Eyes cybersecurity authorities also warned critical infrastructure defenders worldwide of an increased risk that Russia-backed hacking groups could target organizations within and outside Ukraine's borders.
At the time, network defenders were advised to prioritize patching actively exploited security flaws, provide end-users with training, enforce multi-factor authentication, and secure and monitor remote desktop protocol (RDP) assets.
In January, the FBI, CISA, and NSA issued a similar joint advisory, exposing multiple Russian threat groups (including APT29, APT28, and the Sandworm Team) targeting US critical infrastructure organizations.


Comments
lonegull - 1 year ago
The same critical infrastructure the NSA and FBI have hacked and backdoored since 9/11, in addition to hoarding zero-days for the same purposes. We can't secure the nation when vulnerabilities are being kept secret, when the Government is backdooring infrastructure and networks undermining the very effort they now push.