
The National Security Agency (NSA) and cybersecurity partner agencies issued an advisory today recommending system administrators to use PowerShell to prevent and detect malicious activity on Windows machines.
PowerShell is frequently used in cyberattacks, leveraged mostly in the post-exploitation stage, but the security capabilities embedded in Microsoft’s automation and configuration tool can also benefit defenders in their forensics efforts, improve incident response, and to automate repetitive tasks.
The NSA and cyber security centres in the U.S. (CISA), New Zealand (NZ NCSC), and the U.K. (NCSC-UK) have created a set of recommendations for using PowerShell to mitigate cyber threats instead of removing or disabling it, which would lower defensive capabilities.
“Blocking PowerShell hinders defensive capabilities that current versions of PowerShell can provide, and prevents components of the Windows operating system from running properly. Recent versions of PowerShell with improved capabilities and options can assist defenders in countering abuse of PowerShell”
Lower risk for abuse
Reducing the risk of threat actors abusing PowerShell requires leveraging capabilities in the framework such as PowerShell remoting, which does not expose plain-text credentials when executing commands remotely on Windows hosts.
Administrators should be aware that enabling this feature on private networks automatically adds a new rule in Windows Firewall that permits all connections.
Customizing Windows Firewall to allow connections only from trusted endpoints and networks helps reduce an attacker’s chance for successful lateral movement.
For remote connections, the agencies advise using the Secure Shell protocol (SSH), supported in PowerShell 7, to add the convenience and security of public-key authentication:
- remote connections don’t need HTTPS with SSL certificates
- no need for Trusted Hosts, as required when remoting over WinRM outside a domain
- secure remote management over SSH without a password for all commands and connections
- PowerShell remoting between Windows and Linux hosts
Another recommendation is to reduce PowerShell operations with the help of AppLocker or Windows Defender Application Control (WDAC) to set the tool to function in Constrained Language Mode (CLM), thus denying operations outside the policies defined by the administrator.
“Proper configuration of WDAC or AppLocker on Windows 10+ helps to prevent a malicious actor from gaining full control over a PowerShell session and the host”
Detecting malicious PowerShell use
Recording PowerShell activity and monitoring the logs are two recommendations that could help administrators find signs of potential abuse.
The NSA and its partners propose turning on features like Deep Script Block Logging (DSBL), Module Logging, and Over-the-Shoulder transcription (OTS).
The first two enable building a comprehensive database of logs that can be used to look for suspicious or malicious PowerShell activity, including hidden action and the commands and scripts used in the process.
With OTS, administrators get records of every PowerShell input or output, which could help determine an attacker’s intentions in the environment.
Administrators can use the table below to check the features that various PowerShell versions provide to help enable better defenses on their environment:
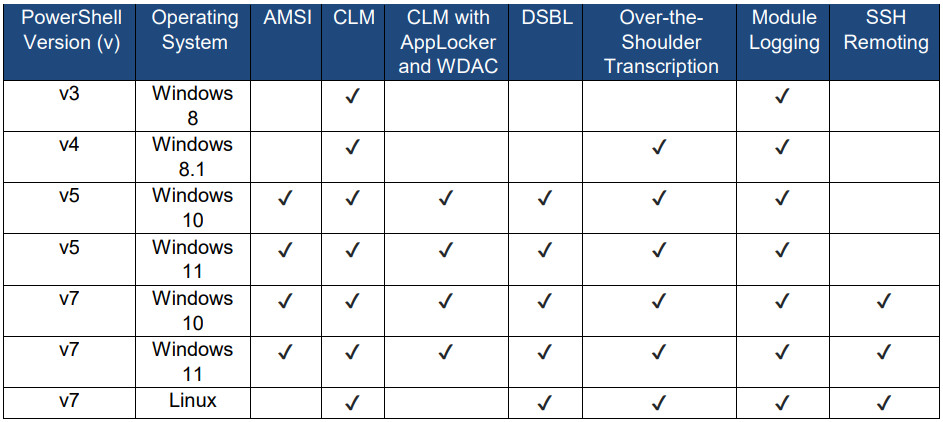
The document the NSA released today states that “PowerShell is essential to secure the Windows operating system,” particularly the newer versions that dealt away with previous limitations.
When properly configured and managed, PowerShell can be a reliable tool for system maintenance, forensics, automation, and security.
The full document, titled “Keeping PowerShell: Security Measures to Use and Embrace” is available here [PDF].


Comments
U_Swimf - 1 year ago
Nice. What version of Powershell comes with Windows by default? Is it 2?
Thanks but the last thing ppl want is to follow the CIA... Talk about sketchy.
Maybe they should make a github page. Oh wait....
h_b_s - 1 year ago
"Nice. What version of Powershell comes with Windows by default? Is it 2?
Thanks but the last thing ppl want is to follow the CIA... Talk about sketchy.
Maybe they should make a github page. Oh wait...."
Don't be dense. The NSA isn't the CIA. The NSA is tasked with defense as well as offensive electronic intelligence operations. Only idiots throw the baby out with the bathwater.
Learn a thing or two about what they're talking about before you spout off next time - like actually reading the article.
U_Swimf - 1 year ago
NSA, CIA, doesn't matter. Tomatos tomatoes
fairlane32 - 1 year ago
Would something like Deep Freeze be better to utilize? Back in the day I remember trying to use AppLocker and it was a nightmare, trying to figure out the blacklist/allowlist mentality.
U_Swimf - 1 year ago
https://man7.org/linux/man-pages/man8/fsfreeze.8.html
Freeze sometimes referred to by a kernel control group like mentioned here: https://www.kernel.org/doc/html/latest/admin-guide/cgroup-v1/freezer-subsystem.html
Read about cgroups and namespaces to learn more about the above.