-
Top Secret US Army and NSA Files Left Exposed Online on Amazon S3 Server
Ten days after an Amazon S3 server exposed data from the US Army's CENTCOM and PACOM divisions, security researchers have identified another S3 server instance that leaked files from INSCOM, a joint US Army and NSA agency tasked with conducting intelligence, security, and information operations.
- November 28, 2017
- 01:27 PM
 2
2
-
Bad Rabbit Ransomware Outbreak Also Used NSA Exploit
Two days after the Bad Rabbit ransomware outbreak has wreaked havoc in Russia and Ukraine, security researchers are still unearthing details regarding the malware's modus operandi.
- October 26, 2017
- 07:40 PM
 1
1
-
Researchers Find a Way to Disable Much-Hated Intel ME Component Courtesy of the NSA
Researchers from Positive Technologies — a provider of enterprise security solutions — have found a way to disable the Intel Management Engine (ME), a much-hated component of Intel CPUs.
- August 28, 2017
- 06:37 PM
 1
1
-
Russian Cyberspies Are Using NSA Tools to Target European Hotels
After the US government has spent probably millions of dollars developing hacking tools, Russian hackers are now using them to spy on guests across hotels in Europe and the Middle East.
- August 11, 2017
- 11:17 AM
 0
0
-
Exploit Derived From ETERNALSYNERGY Upgraded to Target Newer Windows Versions
Thai security researcher Worawit Wang has put together an exploit based on ETERNALSYNERGY that can also target newer versions of the Windows operating system.
- July 17, 2017
- 11:55 AM
 0
0
-
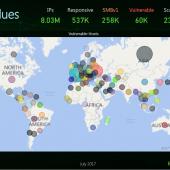
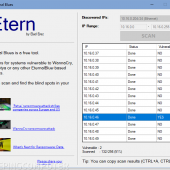
App Finds More Than 50,000 Computers Vulnerable to ETERNALBLUE Exploit
The developer of a tool named Eternal Blues that scans for computers vulnerable to the NSA's ETERNALBLUE exploit has published statistics gathered from the app's usage.
- July 13, 2017
- 06:30 PM
 0
0
-
"Eternal Blues" Tool Tests Computers Against NSA's ETERNALBLUE Exploit
Security researcher Elad Erez has created a tool named Eternal Blues that system administrators can use to test if computers on their network are vulnerable to exploitation via NSA's ETERNALBLUE exploit.
- June 30, 2017
- 03:56 PM
 5
5
-
Shadow Brokers Threaten to Expose Identity of Former NSA Hacker
The Shadow Brokers have published a new message today, gloating about the damage caused by the NotPetya ransomware, and threatening to expose the real-life identity of an alleged NSA employee, who they say has been mocking the group on Twitter.
- June 28, 2017
- 02:23 PM
 0
0
-
NSA Malware Used to Infect Windows PCs with Cryptocurrency Miner
Windows computers are being targeted with a new cryptocurrency miner that uses an NSA hacking tool to infect users' PCs. Detected under the generic name of Trojan.BtcMine.1259, this trojan was first spotted last week by Russian antivirus vendor Dr.Web.
- June 20, 2017
- 03:53 PM
 1
1
-
Microsoft Issues Windows XP Security Updates for Previously Ignored NSA Hacking Tools
In two blog posts today, Microsoft announced it issued new security patches for Windows XP users to protect them against "potential nation-state activity" that could cause "destructive cyber attacks" similar to the WannaCry outbreak that hit users last month.
- June 13, 2017
- 04:50 PM
 6
6
-
Researcher Wants to Protect Whistleblowers Against Hidden Printer Dots
Gabor Szathmari, a security researcher for CryptoAUSTRALIA, is working on a method of improving the security of leaked documents by removing hidden dots left behind by laser printers, which are usually used to watermark documents and track down leakers.
- June 09, 2017
- 05:20 AM
 7
7
-
US Charges NSA Contractor Over Leak of Russia Hacking Report
The US Department of Justice (DOJ) has filed official charges against a 25-year-old woman, Reality Leigh Winner, of Augusta, Georgia, for leaking classified material to the press.
- June 06, 2017
- 06:50 AM
 2
2
-
Security Researchers Are Gathering Funds to Buy Future Shadow Brokers Exploits
A group of security researchers have set up a Patreon page to raise funds necessary to buy their way into the first batch of monthly exploit the Shadow Brokers promised on Tuesday.
- May 31, 2017
- 02:00 PM
 0
0
-
The Shadow Brokers Announce Details About Upcoming Monthly Dump Service
In a message posted online early this morning, the Shadow Brokers — the cyber-espionage group believed to have stolen hacking tools from the NSA — announced new details about their upcoming "monthly dump service."
- May 30, 2017
- 04:45 AM
 0
0
-
Security Firm Releases Windows XP Patch for NSA Exploit ESTEEMAUDIT
Cyber-security firm enSilo has released a patch for Windows XP and Windows Server 2003 that will protect against attacks via ESTEEMAUDIT, a hacking tool dumped online by the Shadow Brokers last month, and allegedly developed by the NSA.
- May 25, 2017
- 09:27 AM
 0
0
-
New Shadow Brokers Message Teases Data From Nuke Programs, Windows 10 Exploits
Today, the Shadow Brokers have published a new message teasing new exploits for people who register for a new membership program the group has announced for next month, June 2017.
- May 16, 2017
- 05:30 AM
 2
2
-
Microsoft Exec Blames WannaCry Ransomware on NSA Vulnerability Hoarding Program
Microsoft's Chief Legal Officer Brad Smith has penned a blog post today, accusing the NSA of stockpiling exploits, failing to protect its hacking tools, and indirectly causing the WannaCry ransomware outbreak.
- May 14, 2017
- 09:00 PM
 3
3
-
Over 36,000 Computers Infected with NSA's DoublePulsar Malware
DOUBLEPULSAR, one of the NSA hacking tools leaked last Friday by the Shadow Brokers, has been used in the wild by ordinary hackers, who infected over 36,000 computers across the world.
- April 21, 2017
- 05:10 PM
 3
3
-
AES-NI Ransomware Dev Claims He's Using Shadow Brokers Exploits
The developer of the AES-NI ransomware claims that the recent "success" he's been enjoying is due to the NSA exploits leaked last week by the Shadow Brokers group.
- April 21, 2017
- 06:10 AM
 1
1
-
Microsoft Says It Already Patched Most of the Shadow Brokers Exploits
Earlier today, Microsoft concluded an investigation which it started yesterday after a mysterious group of hackers known as The Shadow Brokers dumped a trove of Windows exploits online, as part of a plan started last year and aimed at ousting the Equation Group cyber-espionage group as the NSA.
- April 15, 2017
- 12:50 PM
 1
1