
Microsoft has released a PowerShell script to automate updating the Windows Recovery Environment (WinRE) partition in order to fix CVE-2024-20666, a vulnerability that allowed for BitLocker encryption bypass.
This security issue was resolved in the KB5034441 security update released earlier this week during this month's Patch Tuesday.
The PowerShell script addresses a known issue causing KB5034441 install failures on Windows 10 systems, which leaves the devices vulnerable to the BitLocker encryption bypass flaw that allows access to encrypted data.
When trying to deploy the security update, users report seeing 0x80070643 errors, saying, "There were some problems installing updates, but we'll try again later. If you keep seeing this and want to search the web or contact support for information, this may help: (0x80070643)."
As Microsoft explains, this happens because instead of displaying a CBS_E_INSUFFICIENT_DISK_SPACE error when the WinRE partition is not large enough, Windows Update incorrectly says the generic "0x80070643 - ERROR_INSTALL_FAILURE" error message instead.
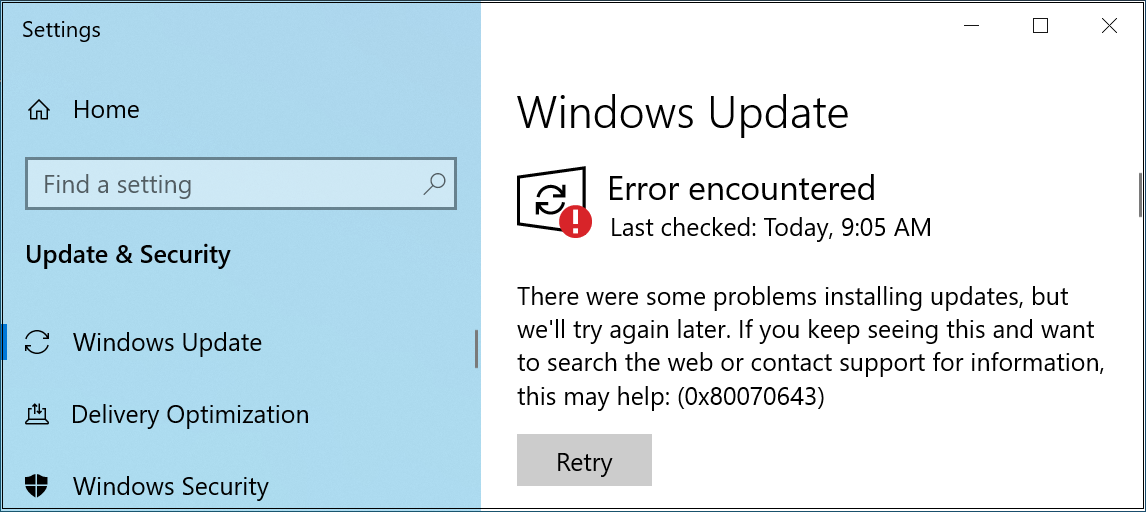
This happens because the WinRE image file (winre.wim) deployed when installing the KB5034441 security update is too large for the recovery partition.
To address the issue, Microsoft advised users to create a larger WinRE partition to have enough room for KB5034441 to install.
Automate BitLocker encryption bypass patching
While you can do this manually using detailed—and quite complex—instructions, the company now also provides a dedicated PowerShell script to help you automate updating the WinRE partition (without having to resize it first) and patching the CVE-2024-20666 BitLocker vulnerability.
"The sample PowerShell script was developed by the Microsoft product team to help automate the updating of WinRE images on supported Windows 10 and Windows 11 devices," Microsoft said.
"Run the script with Administrator credentials in PowerShell on the affected devices. There are two scripts available—which script you should use depends on the version of Windows you are running."
When running the script on your system, it mounts the WinRE image, applies an architecture-specific Safe OS Dynamic Update you have to download from the Windows Update Catalog before running the script, unmounts the image, and then reconfigures WinRE for BitLocker service if the BitLocker TPM protector is present.
From BleepingComputer's tests, you may also have to use Microsoft's Show or Hide Tool to hide the KB5034441 update after running the script, so Windows Update won't keep trying to install the buggy update and display an error.
Patch management company Action1 also released scripts that automate the resizing of the Windows Recovery Environment (WinRE) partition if you prefer to go that route.
If you choose to manually resize the WinRE partition or use Action1's scripts, it's strongly advised to back up your data since there's always the risk of your system's partitions getting damaged when adjusted.
Update: Added details on Action1 scripts.


Comments
johnd0e8 - 1 month ago
What if you removed the recovery partition in your base Windows Server 2022 image? I heard this update still fails even if you no longer have a recovery partition present.
Winston2021 - 1 month ago
Why is there a need to "fix" with a problematic update a vulnerability in BitLocker when my Windows Home system doesn't even have BitLocker capability?
Winston2021 - 1 month ago
And is this inexcusable flaw preventing machines so affected from getting regular virus signature updates?
Sloth - 1 month ago
Do they really expect home users to run a PowerShell script, or even know what PowerShell is?
autechre - 1 month ago
well, its better than the manual method of expanding the partition ;)
Paradroyd - 1 month ago
I can verify that there are machines that I support that don't even have a recovery partition that are getting this error. Absolutely none of them are using, or ever have used BitLocker.
For grins, I created a 2GB recovery partition (which is 4X the original 500MB size) and activated it, and it made absolutely no difference. Even after running disk cleanup and a few other standard procedures.
It sure seems like there's more going on with this than the obvious, and they might have to actually address the update itself rather than these hacky "fixes" to the filesystem(s).
Paradroyd - 1 month ago
I should add that there are some other machines that I manage that had active recovery partitions, and expanding the partitions on those did fix the problem. It just seems to not make any difference if you didn't already have an active recovery partition and you're getting the error.
I should also add that these are all Windows 10 enterprise, volume licensed machines using a KMS with no (other) obvious issues.
Mountaineer - 1 month ago
I've used Powershell before, but I couldn't figure out how to get the script from the web page to the shell.
Highlighting, then copy / paste didn't seem to be an option.
Can someone please tell me how to do this?
autechre - 1 month ago
highlight, copy & paste the script text into notepad, save as whateverfilenameyoulike.ps1
then, open an admin powershell window and "run" the .ps1 file. provided you've copied and pasted the whole thing, there should be no errors.
Chewie316 - 2 days ago
I have followed your instructions but when I run the script I am a bit confused with what to put for the packagePath <Required>
Not sure why MS needs to make this so hard to fix why not just make an update to fix this. Anyway I won't keep ranting but if you could let me know about the PackagePath I would be very greatful.
aldfort - 1 month ago
I updated an older backup laptop yesterday and it did not even attempt the install of KB5034441 Also my main PC with 3 failed installs is now reporting "Up to Date" rather than the failed install message.
cyberwolfe - 1 month ago
Yeah. Let's trust Microsoft to fix what they broke.
That last line within the script has a spelling mistake, yet Microsoft is suggesting people to execute this?
No thank you.
jonkloske - 1 month ago
We just hit the same issue on a fresh install of Server 2022 Datacenter.
FilledWithHate - 1 month ago
One of the massive issues with "KB5028997: Instructions to manually resize your partition to install the WinRE update" and the reason so many Windows users ran into issues with it is that the instructions only work if your recovery partition is AFTER (i.e. "to the right of") the Windows partition.
The instructions explain how to remove 250-MB of space from the RIGHT side of your Windows partition, and then in effect replace your 500-MB recovery partition with a 750-MB recovery partition, using the freed space. This is great, if your recovery partition is indeed on the RIGHT side. But...
If your drive has a 500-MB (or simply a too-small) recovery partition on the LEFT side of the Windows partition, you're screwed. Again, their instructions simply shrink the Windows partition on the RIGHT SIDE. This would leave you with 500 MB of empty space on the left side of the Windows partition, and 250 MB of empty space on the right side. I think the problem here is pretty clear.
Some real mental giants over there in Redmond. And, really, we know where else.
Bob_Who - 1 month ago
I just have to say that after wasting lots of time on the M$ site that arriving here today is such a wonderful relief and a breath of fresh air. The comments above are just an instant cure to M$ lethargy and half baked instruction. Thanks for bleeping intelligently with insight and humor!!!
Chewie316 - 2 days ago
Can anyone provide info on what should be used for PackagePath when running script.
I am confused with what I am suppose to use and can't seem to find an answer.