
Malware operators have been increasingly abusing the Google Ads platform to spread malware to unsuspecting users searching for popular software products.
Among the products impersonated in these campaigns include Grammarly, MSI Afterburner, Slack, Dashlane, Malwarebytes, Audacity, μTorrent, OBS, Ring, AnyDesk, Libre Office, Teamviewer, Thunderbird, and Brave.
The threat actors the clone official websites of the above projects and distribute trojanized versions of the software when users click the download button.
Some of the malware delivered to victim systems this way include variants of Raccoon Stealer, a custom version of the Vidar Stealer, and the IcedID malware loader.
BleepingComputer has recently reported on such campaigns, helping to reveal a massive typosquatting campaign that used over 200 domains impersonating software projects. Another example is a campaign using fake MSI Afterburner portals to infect users with the RedLine stealer.
However, one missing detail was how users were exposed to these websites, a piece of information that has now become known.
Two reports from Guardio Labs and Trend Micro explain that these malicious websites are promoted to a broader audience via Google Ad campaigns.
Google Ads abuse
The Google Ads platform helps advertisers promote pages on Google Search, placing them high in the list of results as advertisements, often above the official website of the project.
This means that users looking for legitimate software on a browser without an active ad blocker will see promotion first and are likely to click on it because it looks very similar to the actual search result.
If Google detects that the landing site is malicious, the campaign is blocked, and the ads are removed, so threat actors need to employ a trick in that step to bypass Google’s automated checks.
According to Guardio and Trend Micro, the trick is to take the victims clicking on the ad to an irrelevant but benign site created by the threat actor and then redirect them to a malicious site impersonating the software project.
.png)
“The moment those “disguised” sites are being visited by targeted visitors the server immediately redirects them to the rogue site and from there to the malicious payload,” explains Guardio Labs in the report.
“Those rogue sites are practically invisible to visitors not reaching from the real promotional flow showing up as benign, unrelated sites to crawlers, bots, occasional visitors, and of course for Google’s policy enforcers” - Guardio Labs
The payload, which comes in ZIP or MSI form, is downloaded from reputable file-sharing and code-hosting services such as GitHub, Dropbox, or Discord’s CDN. This ensures that any anti-virus programs running on the victim’s machine won’t object to the download.
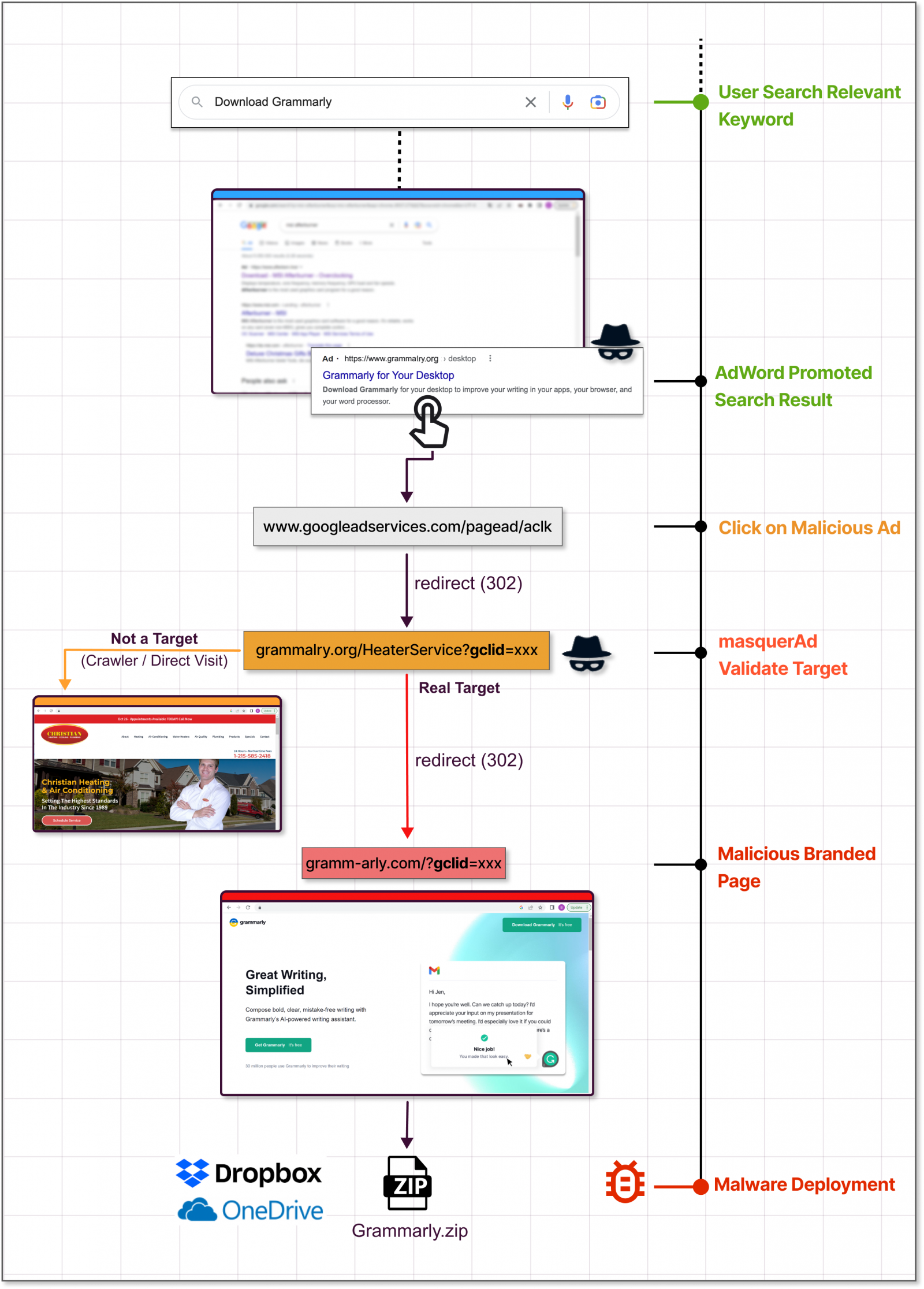
Guardio Labs says that in a campaign they observed in November, the threat actor lured users with a trojanized version of Grammarly that delivered Raccoon Stealer.
The malware was bundled with the legitimate software. Users would get what they downloaded and the malware would install silently.
Trend Micro’s report, which focuses on an IcedID campaign, says the threat actors abuse the Keitaro Traffic Direction System to detect if the website visitor is a researcher or a valid victim before the redirection happens. Abusing this TDS has been seen since 2019.
Avoid harmful downloads
Promoted search results can be tricky as they carry all the signs of legitimacy. The FBI has recently issued a warning about this type of ad campaign, urging internet users to be very cautious.
One good way to block these campaigns is to activate an ad-blocker on your web browser, which filters out promoted results from Google Search.
Another precaution would be to scroll down until you see the official domain of the software project you’re looking for. If unsure, the official domain is listed on the software’s Wikipedia page.
If you visit the website of a particular software project frequently to source updates, it’s better to bookmark the URL and use that for direct access.
A common sign that the installer you’re about to download might be malicious is an abnormal file size.
Another clear giveaway of foul play is the domain of the download site, which may resemble the official one but has swapped characters in the name or a single wrong letter, known as “typosquatting.”


Comments
edmoncu - 1 year ago
i have a colleague that got redirected to a malware-weaponized version of notepad++ when he searched for it because of this impersonation sites showing as ad on top of google's search result.
Mahhn - 1 year ago
Kinda disappointed the Elephant isn't being pointed out - google for running adds for malicious actors willingly. This year - TWICE - scammers ran adds on google impersonating our FI - we also run adds on goog, but since the criminals paid more, goog put their adds above ours. Google does not care if company X is advertising with them and company B, says hey - list me as company X and I will give you more money - and they do. Goog sells add space to ANYONE that will pay them - that is a bigger issue than malicious websites - goog is the enabler and profiting from it - so they do not care.
edmoncu - 1 year ago
Correct Mahhn, Google highlights ads more than its actual function by intentionally skewing first search results with ads (or affiliate links), regardless if it is fake or whether it hosts weaponized malware. This is an intentional deception from Google to lure people into forcibly clicking affiliate links/malicious ads with fake software containing trojans.
Mahhn - 1 year ago
Also, we requested to goog they take down the impersonation adds, they refused! We ended up contacting the site's host, who did respond immediately.
verdy_p - 1 year ago
I don't understand why google is promoting and is so proud about its "IA" and making searches "relevant", but is still unable to use it to check the contents of its advertizers (even if they are paying some pennies to Google for their "campaign"). This should be a clear violation of GoogleAds service and forcing an immediate termination (including not reimbursing their prepayments made, and all other campaigns they initiated).
And even if the content was legit when the ad campaign was initiated, it should be monitored each time there's any change in the redirects or any change of their hosting domains). Detected spoofed domains is relatively zeasy by moderately trained humans, but should be extremely easy for the Google AI that can perform faster many more checks than a single user could do almost instantly.
So Google has an active complicity, it does not check its advertizers, as logn as they pay some pennies. That's clearly unfair business, and even anticompetitive: Google once agains should be condamned by justice, which could even take down the GoogleAds network for some time (Google wuold then have to prove that it effectively enforces a strong policy for all its advertizers, including advertizers using partner nertworks, and all CDNs with wich it should be forced to cooperate and react promptly)
beefsteak - 1 year ago
Well , I rather be a privater (linus tech tips words about adbloker users) , and use an adblock , than be an english man and have computer full of virus and trojans. Go on google give as more of yours "brilant" manifest 3. Should you be fixing your licky advert services first.
taurolyon - 1 year ago
I remember when Google removed "Don't be evil" from their business model. Seems they're living up to their new business model.
edmoncu - 1 year ago
"I remember when Google removed "Don't be evil" from their business model. Seems they're living up to their new business model."
youtube especially is becoming a new haven for these threat actors by faking as content creators and not helping them combat these impersonators.
edmoncu - 1 year ago
this is where the value of ad-blocking really matters. we cannot trust even the ads to provide legitimate messaging. not just it removes the annoyance of excessive and aggressive revenue promotion, it also prevents you from getting malware because of this loophole.