
Kaspersky has launched a new information hub to help with their open-source stalkerware detection tool named TinyCheck, created in 2019 to help people detect if their devices are being monitored.
Stalkerware is software explicitly created to spy on people via their smartphones by monitoring their whereabouts, communications, photos, browsing history, and more.
These tools exploit vulnerabilities in the security of modern mobile operating systems to run stealthily in the background without raising suspicion on the victim.
The anti-stalkerware TinyCheck tool
Kaspersky's TinyCheck is a program that can quickly identify activity associated with stalkerware in a non-invasive way by running on an external device (Raspberry Pi) and monitoring its outgoing traffic via WiFi.
.png)
The tool doesn’t need to be installed on the device, doesn’t interfere with anything on the mobile OS, and hence doesn’t introduce a risk of the remote abuser realizing a check has been performed.
This is crucially important for the victim's safety, as if the abuser detects any interference, they could escalate their abuse.
Also, since TinyCheck doesn’t need to run on the device itself, it can identify stalkerware presence on any mobile OS, including Android and iOS.
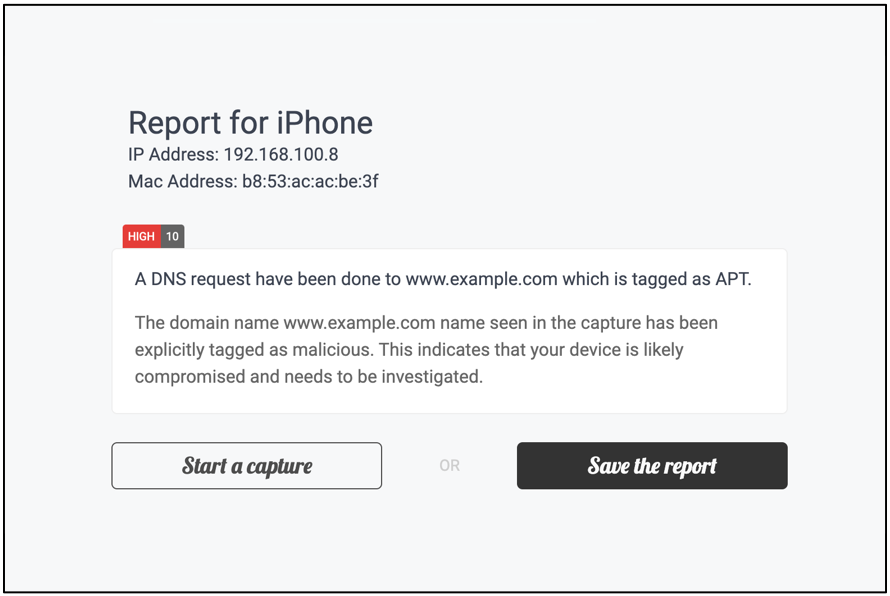
TinyCheck will only look at the signs of abuse, like which servers receive communication from the device and won’t read the contents of the victim’s communications, like SMSs and emails.
Also, as explained in the tool's privacy policy, captured packets, logs, and all the analysis results are kept locally on the device that runs TinyCheck, so nothing reaches Kaspersky or any other remote server.
Because the tool is open-source, its code can be scrutinized (and improved) by anyone, so it can’t hide suspicious functions under the hood.
Finally, regarding what kind of stalkerware tools TinyCheck can identify, the list includes all known commercially available spyware and, in some cases, sophisticated products like Pegasus.
Kaspersky added the ability to detect sophisticated spyware in August 2021, but due to the constant refresh of the servers/domains of these tools, the capability of TinyCheck to detect these infections is limited.
Role of the new online hub
Numerous NGOs have used TinyCheck since its release, but unfortunately, stalkerware victimization is a large-scale global problem that’s getting worse. Unfortunately, the use of stalkerware follows the same trajectory as domestic violence and harassment that go hand in hand with deploying these tools.
Kaspersky launched the new online hub to promote TinyCheck to anyone who suspects they might be cyberstalking victims, explaining how it works in layman's terms and providing easy access to helpful resources.
The portal includes a frequently asked questions section, instructions on using TinyCheck, and a contact form that users can use if they have questions about the tool.
Signs of infection
As stalkerware is designed to remain hidden from the owner of a device, detecting these types of malware can be difficult without a specialized tool.
However, there are certain signs that can be caused by stalkerware, and malware for that matter, which are listed below:
- Fast-draining batteries are caused by possible stalkerware running 24x7 in the background.
- Increased data traffic without changes in your phone's use caused by the stalkerware transmitting data to remote servers.
- GPS or microphone activation indications are shown randomly.
- People know information about the content on your phone, including appointments from your calendar, photos, and your location.
- Unknown sign-in attempts for online accounts you use on your phone.
- The device overheats when it is not being used.
If you spot any of the above in combination with people knowing information about you that it would not normally be known, you should run an anti-stalkerware check, install an AV tool on the device, use a VPN, or even replace your device.
Enabling two-factor authentication is also highly recommended to protect your online accounts. However, if your device is infected with stalkerware, it may allow the abuser access to your 2FA codes as well.
Finally, it is vital to remember that if you’re a person at risk, never leave your device unattended, as these spyware tools are typically installed manually by the perpetrators physically accessing the target’s smartphones.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now