Windows Forensics: Have I been Hacked?
Lawrence Abrams
- February 17, 2004
- Read 450,888 times
Table of Contents
- Introduction
- Why would someone want to hack me?
- Creating your Computer Forensics Tool belt
- How can I tell if I have been hacked?
- Looking for further suspicious activity
- What if a tool states another program is running but I cant find it!!!?!?
- Other Hacks? And are they detectable?
-
Conclusion
One of the top questions I see on forums is "How do I know if I have been hacked?". When something strange occurs on a computer such as programs shutting down on their own, your mouse moving by itself, or your CD constantly opening and closing on its own, the first thing that people think is that they have been hacked. In the vast majority of cases there is a non-malicious explanation for these problems such as faulty hardware or problematic software, but it is better to be safe than sorry for not investigating deeper. Unfortunately, the vast majority of computer users have no idea how to go about determining if their computer is hacked. It is for these people, that I am writing this tutorial.
Before we continue, it is important to go over some basic information. In current times, the word hacker is more commonly known as someone who breaks into other's computers, websites, or software without permission. The original definition is actually someone who likes to understand the internal workings of software, hardware, or an electrical device in order to modify it for their own purposes. For this article, we will continue to use the word hacker to describe someone who has broken into a computer in order to avoid confusion.
It should also be noted that in many of the cases that people think they are hacked, they are instead infected with malware such as Spyware, Scareware, or Trojans. Therefore, it is suggested that you first use an anti-virus program or anti-spyware program to check for computer infections before proceeding with the rest of this tutorial. If you need help check to see if your computer is infected, feel free to create a virus removal log and post it in our forums to be checked by a trained helper. A guide on how to do this can be found here:
Preparation Guide For Use Before Using Malware Removal Tools and Requesting Help
In this tutorial I will show you how to determine if your Windows computer is hacked and how you can go about cleaning up the files that may have been left behind. This tutorial will also cover the common hack methods and how to detect them. There are more invasive hacking methods that this guide will not go over in great length due to their infrequent use. In my experience, though, most of the hacks that are done in mass, especially by the script kiddies, will be detectable by the methods outlined below.
As this is an advanced topic, some of the information discussed in this tutorial may difficult for beginning computer users. If you are having trouble understanding some of the points in the tutorial, feel free to ask in the forums and someone can provide answers to your questions.
Why would someone want to hack me?
Many people think that the main reason someone is hacking their computer is to get back at them for some personal reason. In reality, the majority of hacks are perpetrated by those who do not care who you are, but just want to use your computer's resources for illegal purposes. These hacks are typically performed by programs or scripts that automate the process of hacking a computer for the hacker. When these hacking programs are run they scan large portions of the Internet for computers that have a particular software or Windows vulnerability. When the program detects a vulnerable program it will automatically exploit it and open a backdoor so that the hacker can remotely access it.
Once the hacker has remote access to your computer he can install whatever they want, transfer files, and look at your data. From my experience the most common reasons that a computer is hacked are:
-
Setup a FTP or Web Server to distribute copyrighted material. These types of servers are called Pubstros.
-
Setup an IRC client/bot that is used to DDOS other computers, flood IRC users, scan/hack other computers, and to distribute copyrighted material as a File Server.
-
Use your computer to scan others or hack into other computers. This gives a hacker a greater degree of anonymity as they will be using your computer to perform the illegal actions.
- Install ransomware on your computer that encrypts your files and then prompts you to pay a ransom in order to decrypt them.
Regardless of the reason, once a person starts using your computer without your permission it is imperative to find them quickly as you will have to deal with the ramifications of their actions while they are connected to it.
Creating your Computer Forensics Tool belt
The first thing you need to do before inspecting your computer is to create a Computer Forensics Tool Belt. This tool belt consists of a variety of freeware utilities that you can use throughout this guide to examine the activity on your computer. The tools we recommend are:
Process Explorer - This program will list all open processes and delineate between the parent processes and the processes that are spawned by the parent. This is a very useful program for seeing what programs are running on your computer and how they were launched.
Process Monitor - This program provides a real time display of all process, Windows Registry, and file activity on your computer. This is useful when you are concerned that a hacker may be currently connected to your computer and you wish to get a general idea as to what they are doing. This program can very quickly display a lot of information. Therefore, please play around with this program and setup filter to get a general feel on how it works.
Show Hidden - This is a tool written by BleepingComputer.com that will list all hidden folders, and files if you wish, on your computer. As many hackers hide their tools and files in a hidden folder, this tool will make it easier to find hidden folders that appear suspicious.
TCPView - TCPView is the real work horse for detecting if you have been hacked. This program will list all the programs on your computer that are connected to a remote computer or are waiting for a connection. The program will also list all the IP addresses that are connected and even perform reverse DNS on them so that you can get useful information on who is connected.
TreeSize Free - This program will scan your drive and easily show the folders on your hard drives that are using the most space. If you are concerned that your server was hacked to distribute copyrighted programs and videos, you can use this tool to search for large folders that you can then investigate.
Wireshark - Wireshark is a network sniffing tool that allows you to see the data that is flowing through your network. If you are concerned you are hacked, you can install and use Wireshark to look at the raw TCP/IP packets to see if any nefarious activity is taking place. This is an advanced tool and will not be covered by this tutorial.
Before continuing with the rest of the tutorial, I suggest that you download each of these programs and become familiar with them. Once you play with them a little you should start to understand how they work and how best to use them.
How can I tell if I have been hacked?
When your computer is hacked and being accessed remotely, it is doing so over a TCP/IP network. This allows us to use tools such as TCPView to quickly spot these network connections and terminate them if necessary. Further more, the hacker knows that at some point their point-of-entry will be locked again. With this in mind, the hacker will usually install a backdoor that runs on your computer so that they will be able to get back in even if you patch your computer's security holes. The only time a hacker does not leave something behind, is if they are hacking your computer for specific information or an item. The vast majority of hacks, though, are thankfully not targeted at a particular person or item and your computer was just unlucky to be connected to the Internet at the wrong time.
When you are hacked, hackers may also install RATs, or Remote Access Trojans, and other backdoors that allow the hacker to control your computer remotely. These programs listen on TCP or UDP connections and either connect to an IRC (Internet Relay Chat) channel where they can then be controlled by an operator or act as a backdoor for the hacker. The good news is that these types of programs must use your network to make connections, which opens a path that is easily noticeable using a tool like TCPView.
To see what programs are running or are listening on TCP or UDP ports on your computer, you should run TCPView. Once you start TCPView it will display a list of all the programs on your computer that are connected to the network. This is shown in the image below.
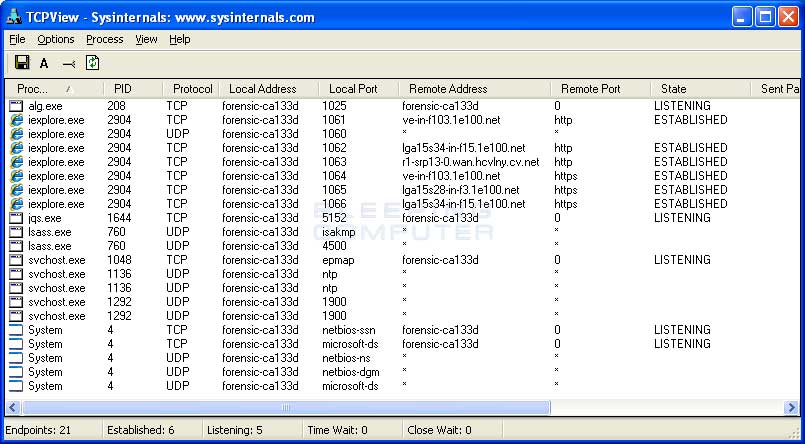
As you can see in the image above, TCPView will display all the programs on your computer that are currently connected to a remote computer over the network or listening for incoming connections. The program is broken up into 5 columns that provide useful information. These columns are:
Process: This column displays the name of the program that is connected to the remote device or is waiting for an incoming connection.
PID: This column shows the process ID for the particular program.
Protocol: This column displays whether the particular row is using TCP or UDP.
Local Address: This column shows the hostname or IP address of the local computer's connection..
Local Port: This column will show the port number being used by the local connection. If the port number corresponds to a standard service, it will show the service name instead.
Remote Address: This is the IP address or hostname remote device the particular program is connected to.
Remote Port: This column will show the port number being used by the remote connection. If the port number corresponds to a standard service, it will show the service name instead.
State: This column shows the state of the program's connection. These states are:
Established - A connection that is established means that there are is an active connection between your computer and the remote computer.
Close Wait - The remote connection has closed the connection. This entry will eventually time out and be removed from the TCPView list.
Time Wait - Your computer has closed the connection. This entry will eventually time out and be removed from the TCPView list.
Listening - This state means that the program is listening for an incoming connection from a remote computer. The port that it is listening on can be found in the local address column.
With the above information you can determine if a connection or a listening program is legitimate. To see if traffic is legitimate you can look up the remote addresses at a site like http://www.dnsstuff.com/. If the remote address looks like a known company or one that makes sense that you would be connected to, then you can reasonably be assured that the particular connection is legitimate. On the other hand, if the IP address shows its to a location in another country that you should not be connected to, then you may have more cause to be concerned. It should be noted that when analyzing connections from web browsers, that you may be legitimately connected to servers all over the world.
You should also examine the programs listed in TCPView. If you see one that you are unsure of, right-click on it and select Process Properties. This will open a small dialog that shows information about the program. If the company information is legitimate, then you can move on. If not, then you may want to investigate further by scanning it with http://www.virustotal.com/ or seeing who it is connected to. It should be noted that there are many programs that legitimately will be waiting for connections or are connected to remote locations. For example, web browsers, messaging programs, and Windows system files are routinely listening or connected to remote devices. Common Windows files that you should not be concerned about are svchost.exe, wininit.exe, services.exe, lsass.exe, and some processes labeled as System Processes.
Let's now use a fictitious examine of a computer hacked with a Pubstro. TCPView on this type of computer may show something like:
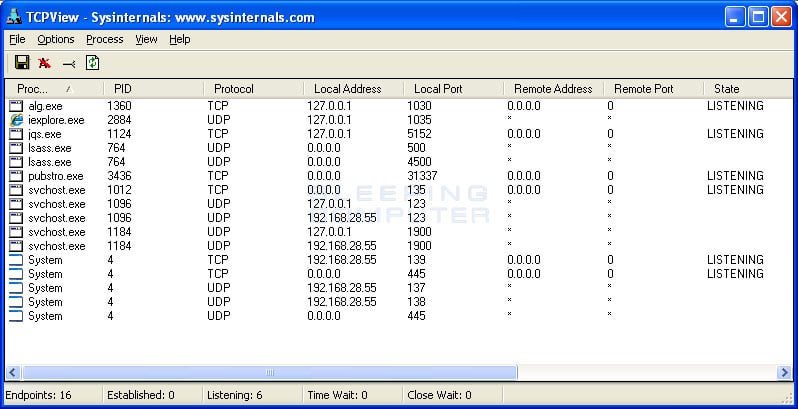
Notice how there is a process named pubstro.exe that is listening on a strange port. If you do a search for pubstro.exe you may not find any legitimate entries or may find information that alludes that this is not a legitimate file. In that case, you would right-click on the file and examine its properties. Finally, if you are concerned about the legitimacy of this file you would then right-click on it and click on the End Process option. This will then terminate the process and close the listening connection.
Once you determine that a program should not be there, you need to determine where it is starting from. To this you need to use a program like DDS or Autoruns that shows all the programs that automatically start in Windows. Once you have determined the launching point, you can then remove that launching point so that the program is no longer started.
Looking for further suspicious activity
Though TCPView can easily spot active connections or programs waiting for a connection, there are times when we want to dig down deeper for suspicious non-network related activity. To do this we use tools such as Process Explorer, Process Monitor, Show Hidden, TreeSize Free, and Wireshark. All of these tools have their different uses and can help spot different clues that may indicate you are hacked. This section will provide a brief overview of how to use each of these tools.
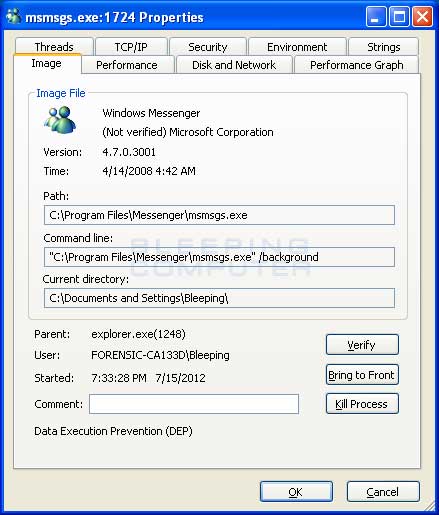
Process Explorer can be used to view all the running processes on your computer. This allows you to spot processes that do not appear legitimate and gather more information about them. To examine a process, just double-click on it and a properties screen will open. This screen contains numerous tabs that provide a variety of information about the particular process. In particular, you want to be concerned with the information on the Image tab and the Strings tab. The strings tab will contain a list of strings found within the executable. These strings may provide a clue as to what the process is doing. The image tab will display information about who created the file, what its name is, where it is located on your hard drive, and the actual commands that were used to execute the program. An example of the type of information you can view for a process is shown below.
Process Monitor is an advanced, but a very useful, tool. If you can master this program then you can essentially watch all the activity a particular process is performing on your computer. When run, this program will immediately start displaying an overwhelming amount of data. In order to harness the power of Process Monitor, you will need to configure display filters that will allow you to specify the particular processes that you wish to see information for. For example, if we wanted to see only the information related to the pubstro.exe process, we can setup a filter like this:
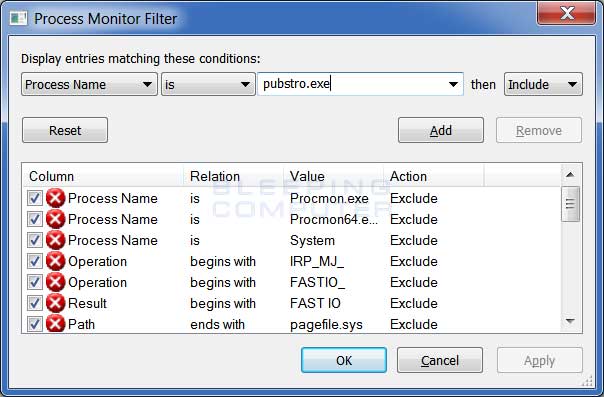
This filter would then only display the information related to the pubstro.exe process.
The Show Hidden is a very basic tool that simply lists all of the folders on your computer that have the hidden attribute. If you use the -f command line argument, then it will list all hidden files as well. When a computer is hacked, the hacker typically creates a folder that contains a variety of tools and programs that they need to hack other computers or setup various programs. Most of the time, this folder will be hidden so that it will not be seen during casual use. Using Show Hidden you can create a list of hidden files and folders that can then examined to see if they should be there. Please note, that there will be MANY legitimate hidden folders, so do not delete anything unless you know for sure it does not belong.
TreeSize Free is another useful program as it will generate a list of all the folders on a drive and how much hard drive space they take up. When a hacker sets up a Warez distribution site on your computer, the files typically take up a great deal of space. Using this program you can easily find folders that consume a lot of space and investigate them for suspicious files.
The last program is an advanced tool called Wireshark, which allows you to look at the data flowing over your network. This tool is not easy to interpret, but once you master it you will quickly be able to see the exact traffic that is flowing over your network and where it is going to.
What if a tool states another program is running but I can't find it!!!?!?
If you use a diagnostic tool and it states that a particular program is running, but you are unable to find it, you need to first make sure you have the option set to see all hidden and system files. You can enable this setting by following the steps in this tutorial: How to see hidden files in Windows. If you are doing a directory listing from the Windows command prompt, make sure you use the /a flag with the dir command to see hidden files.
After making these changes, if you are still unable to see the files then it is possible that a Rootkit is installed on your computer. A rootkit is a program that is used to hide files, Windows Services, and Windows Registry information so that they cannot be seen and removed with normal tools. If a rootkit is involved then the removal process will become much more complicated. Don't worry though, there are still ways to detect these rootkits and clean them up.
The first step is to scan your computer with a Rootkit detector. Our download section has numerous Rootkit scanners available with some being listed below:
- Malwarebytes Anti-Rootkit
- Panda Anti-Rootkit
- Trend Micro RootkitBuster
- RootRepeal
- TDSSKiller
- GMER
- aswMBR
Pick one of the programs above, or as many as you want, and scan your computer with them. If they find any known rootkits or unusual system hooks they will attempt to repair them for you.
If no rootkit is detected, and you are sure there is one involved, you can bypass the rootkit and see the hidden files by using a bootable CD. When dealing with rootkits, the easiest solution is to boot your computer into the Windows Recovery Environment. This environment gives you access to your file system and Windows Registry using a command prompt. Tutorials on how to use and access the Windows Recovery Environment can be found below:
How to install and use the Windows XP Recovery Console
How to use the Command Prompt in the Vista Windows Recovery Environment
How to use the Windows 7 System Recovery Environment Command Prompt
How to use the Windows 8 System Recovery Environment Command Prompt
Once you are booted into the recovery environment there will be no active infections or rookits and you will be able find and remove them easily.
Other Hacks? And are they detectable?
What I have covered so far are the more generic hacks that are used. This tutorial, though, can not cover all possible hacks and ways to detect them. Below is a brief summary of some other types of hacks that you may encounter.
Alternate Data Streams: Alternate Data streams were introduced into NTFS volumes to support the Macintosh Hierarchical File System and are widely undocumented. With the use of Alternate Data Streams, or ADS, a hacker can hide files, even executables, and make them almost invisible to the operating system and therefore yourself. There are tools out there such as LADS or ADS Spy that will enable you to see ADS files and remove them.
Kernel and Device Driver hacks: An experienced hacker may have the knowledge to actually patch system drivers, device drivers, or system calls. This will enable them to issue commands to the OS as Ring0 or at the operating system's kernel security level. If a hack like this occurs, usually the best situation is to backup your data and reinstall the OS. This is because if the hacker has that type of access to the box, then you really can never be sure what else has been compromised. If it is necessary to try and detect and remove these types of hacks, you can use the SFC command from the Windows Recovery Console to find patched system files.
As always, if you need help with any of these issues, feel free to ask us in the Security Forums.
Ultimately, if your computer is hacked you need to make the decision to try and clean it up or to backup your data and reinstall. If you have the time and ability, then it is definitely suggested that you backup your data and reinstall as you will then know you definitely have a clean computer. On the other hand, if you are unable to reinstall, you can use the steps above to detect any hacks and clean them up. This will have to be a judgement call on your part.
If you have any questions regarding these procedures, please do not hesitate to ask in our Security Forums.







