Today a new Locky Ransomware variant was released that now uses the .asasin extension for encrypted files. Personally, I thought the previous extension, ykcol, was more clever, while this one seriously needs a spell checker. Thankfully, the current distribution for this variant is broken due to malformed spam campaign, which is described below.
It is important to note that if you are infected with this ransomware, you are not infected with the Asasin Ransomware, as some sites may call it. You are instead infected by Locky, which is using the .asasin extension.
Asasin Variant Distributed Via Broken Spam Campaigns
This variant is currently being distributed via spam emails that have a subject line similar to "Document invoice_95649_sign_and_return.pdf is complete" and is being spoofed to appear from RightSignature with the email documents@rightsignature.com. Thankfully for us, and not so much for the Locky devs, the only thing working in this campaign is the subject line.
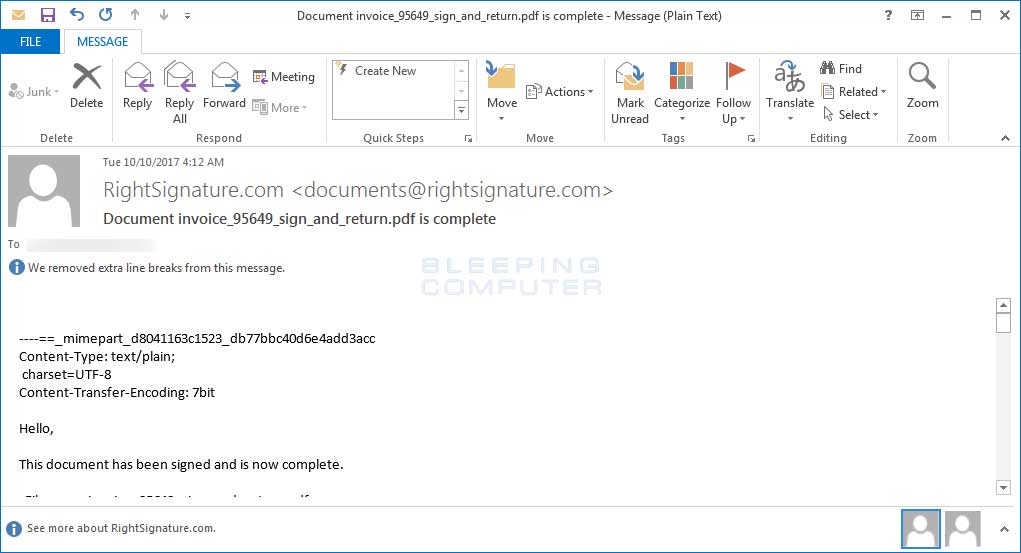
Whoever is distributing these spam emails are not adding the attachments correctly, which is causing the attachments to not be visible to recipient other than as a blob of base64 encoded text as shown in the image below.
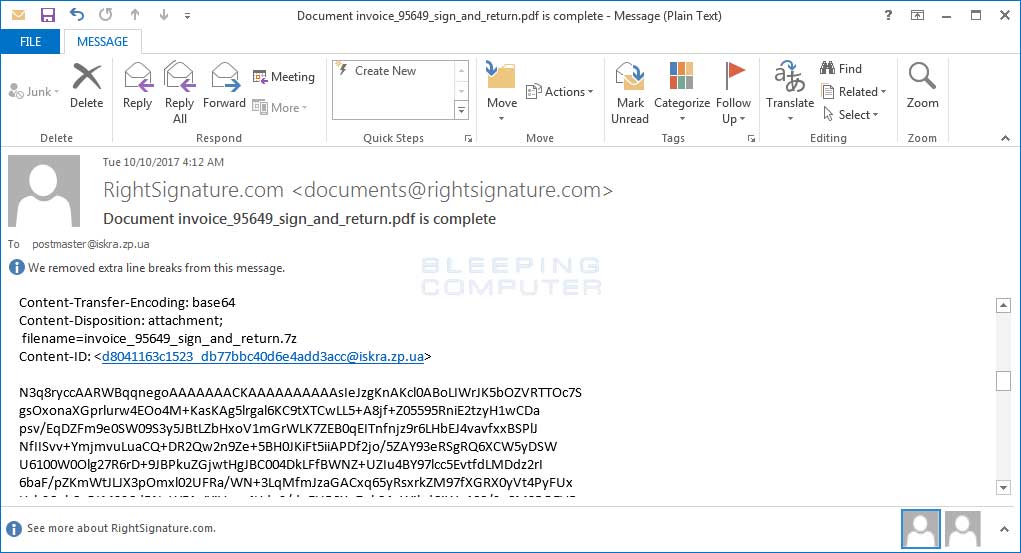
Furthermore, even if the attachment was working correctly, the attachments are 7zip, or .7z, archives which the vast majority of people would have no idea how to open. These 7zip attachments contain a VBS file, which when executed will download the Locky executable from a remote site and execute it.
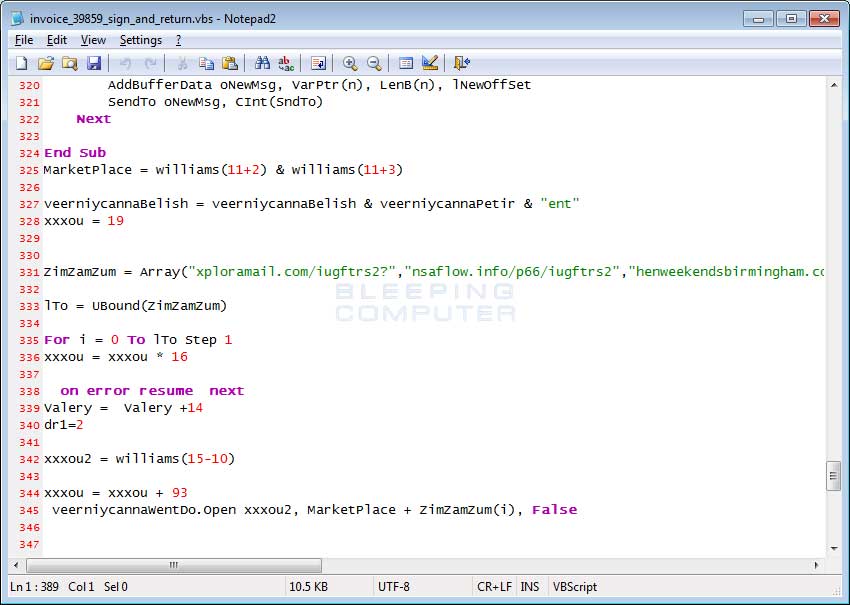
Asasin Locky Ransomware Changes
There really are not much differences between this variant and the previous ykcol variant. The biggest change is that when this variant encrypts a file it will modify the file name and append the .asasin extension. When renaming the file, it uses the format [first_8_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[8_hexadecimal_chars]-[12_hexadecimal_chars].asasin.
This means that a file named 1.png would be encrypted and named something like as E87091F1-D24A-922B-00F6B112-72BB7EA6EADF.asasin.
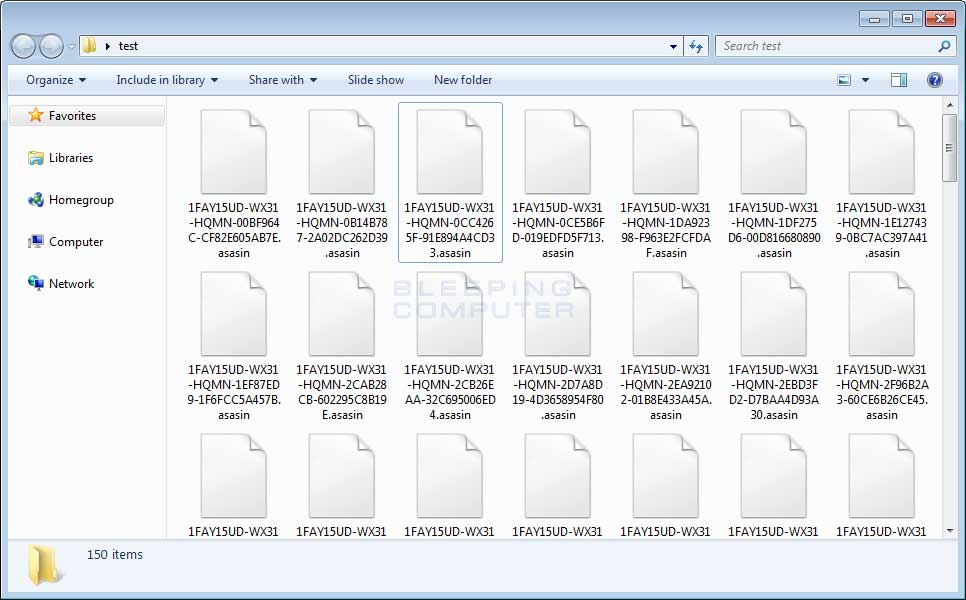
When Locky has finished encrypting the computer, it will remove the downloaded executable and then display a ransom note that provides information on how to pay the ransom. The names of these ransom notes have changed for this version to asasin.htm and asasin.bmp.
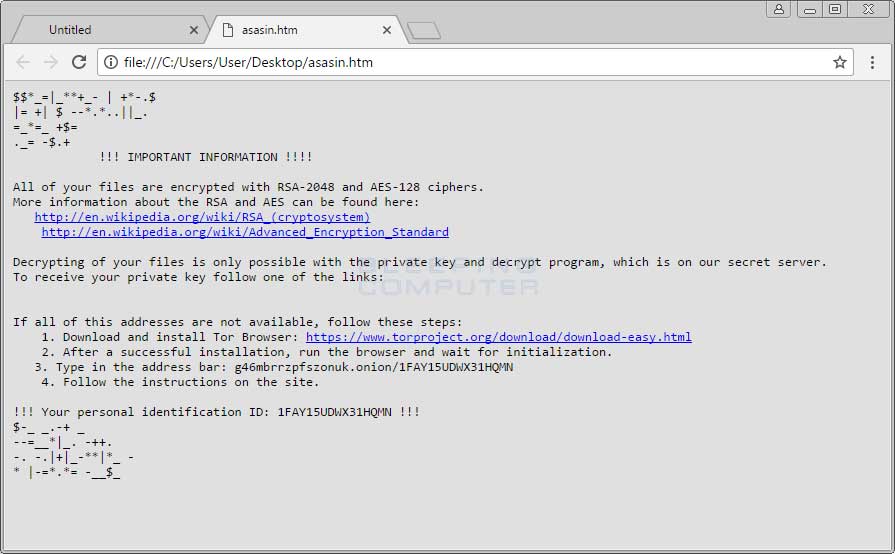
At the time of this writing, the Locky Decryptor TOR payment site has the ransom set to .25 BTC or approximately $1.200 USD.
It is not possible to decrypt the Locky Asasin Ransomware Variant
Unfortunately, at this time it is still not possible to decrypt .asasin files encrypted by the Locky Ransomware for free.
The only way to recover encrypted files is via a backup, or if you are incredibly lucky, through Shadow Volume Copies. Though Locky does attempt to remove Shadow Volume Copies, in rare cases ransomware infections fail to do so for whatever reason. Due to this, if you do not have a viable backup, I always suggest people try as a last resort to restore encrypted files from Shadow Volume Copies as well.
For those who wish to discuss the Locky ransomware or need support, you can use our dedicated Locky Ransomware Help & Support Topic.
How to protect yourself from the Locky Ransomware
In order to protect yourself from Locky, or from any ransomware, it is important that you use good computing habits and security software. First and foremost, you should always have a reliable and tested backup of your data that can be restored in the case of an emergency, such as a ransomware attack.
You should also have security software that contains behavioral detections such as Emsisoft Anti-Malware, Malwarebytes, or HitmanPro.Alert.
Last, but not least, make sure you practice the following good online security habits, which in many cases are the most important steps of all:
- Backup, Backup, Backup!
- Do not open attachments if you do not know who sent them.
- Do not open attachments until you confirm that the person actually sent you them,
- Scan attachments with tools like VirusTotal.
- Make sure all Windows updates are installed as soon as they come out! Also make sure you update all programs, especially Java, Flash, and Adobe Reader. Older programs contain security vulnerabilities that are commonly exploited by malware distributors. Therefore it is important to keep them updated.
- Make sure you use have some sort of security software installed.
- Use hard passwords and never reuse the same password at multiple sites.
For a complete guide on ransomware protection, you visit our How to Protect and Harden a Computer against Ransomware article.


Comments
Amigo-A - 6 years ago
Thank you!
Amigo-A - 6 years ago
Please this is
[first_8_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[4_hexadecimal_chars]-[12_hexadecimal_chars].asasin
correct for this: 8-4-4-8-12
[first_8_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[next_4_hexadecimal_chars_of_id]-[8_hexadecimal_chars]-[12_hexadecimal_chars].asasin
Lawrence Abrams - 6 years ago
Thx. Fixed