
There's mounting evidence that Akira ransomware targets Cisco VPN (virtual private network) products as an attack vector to breach corporate networks, steal, and eventually encrypt data.
Akira ransomware is a relatively new ransomware operation launched in March 2023, with the group later adding a Linux encryptor to target VMware ESXi virtual machines.
Cisco VPN solutions are widely adopted across many industries to provide secure, encrypted data transmission between users and corporate networks, typically used by remotely working employees.
Reportedly, Akira has been using compromised Cisco VPN accounts to breach corporate networks without needing to drop additional backdoors or set up persistence mechanisms that could give them away.
Akira targets Cisco VPNs
Sophos first noted Akira's abuse of VPN accounts in May, when researchers stated that the ransomware gang breached a network using "VPN access using Single Factor authentication."
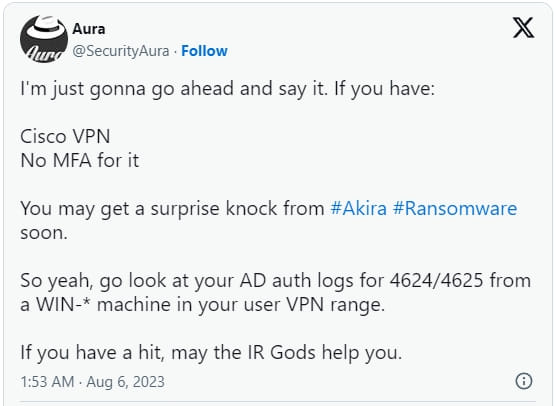
However, an incident responder, known as 'Aura,' shared further information on Twitter on how they responded to multiple Akira incidents that were conducted using Cisco VPN accounts that weren't protected by multi-factor authentication.
In a conversation with BleepingComputer, Aura stated that due to the lack of logging in Cisco ASA, it remained unclear if Akira brute-forced the VPN account credentials or if they bought them on dark web markets.
A SentinelOne WatchTower report shared privately with BleepingComputer and focusing on the same attack method presents the possibility of Akira exploiting an unknown vulnerability in Cisco VPN software that might be able to bypass authentication in the absence of MFA.
SentinelOne found evidence of Akira using Cisco VPN gateways in leaked data posted on the group's extortion page and observed Cisco VPN-related traits in at least eight cases, indicating this is part of an ongoing attack strategy by the ransomware gang.
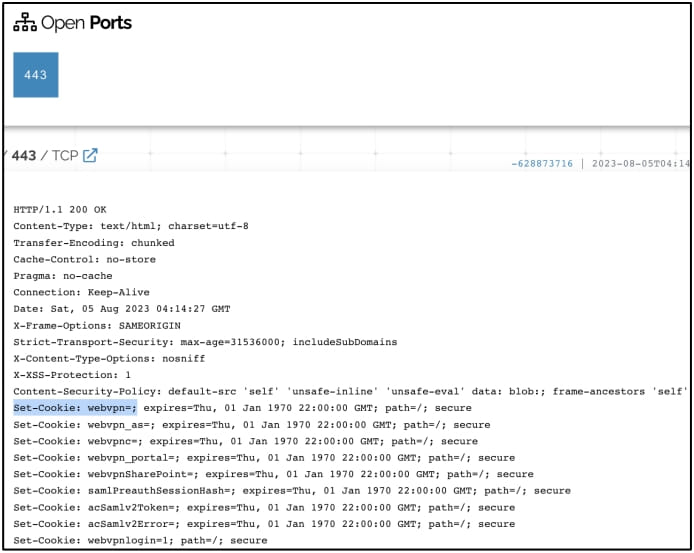
Source: SentinelOne
Remote RustDesk access
Additionally, SentinelOne WatchTower's analysts observed Akira using the RustDesk open-source remote access tool to navigate compromised networks, making them the first ransomware group known to abuse the software.
Because RustDesk is a legitimate tool, its presence is unlikely to raise any alarms, so it can offer stealthy remote access to breached computers.
Other benefits that arise from using RustDesk include:
- Cross-platform operation on Windows, macOS, and Linux, covering Akira's full targeting range.
- P2P connections are encrypted and hence less likely to be flagged by network traffic monitoring tools.
- Supports file transfer which can facilitate data exfiltration, streamlining Akira's toolkit.
Other TTPs observed by SentinelOne in Akira's latest attacks include SQL database access and manipulation, disabling firewalls and enabling RDP, disabling LSA Protection, and disabling Windows Defender.
These not-so-subtle changes are performed after the attackers establish their presence in the environment and are ready to proceed to the final phases of their attack.
In late June 2023, Avast released a free decryptor for Akira ransomware. However, the threat actors have patched their encryptors since then, and Avast's tool will only help victims of older versions.
Update 8/24 - A Cisco spokesperson has confirmed to BleepingComputer that its VPN products support MFA (multi-factor authentication) from vendors across the industry.
Also, customers can set up/configure logging on Cisco ASAs, and the recommended approach is to send logging data to a remote syslog server. This enables improved correlation and auditing of network and security incidents across various network devices.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now