
A patch that prevented NordVPN and ProtonVPN clients from running arbitrary code with administrator privileges on Windows machines implemented insufficient controls against the vulnerability, a security researcher discovered.
Both clients use OpenVPN open-source software to set up a secure tunnel from one point to another. The service needs to run with administrator permissions, so any code it runs enjoys these privileges.
Paul Rascagneres of Cisco Talos found that OpenVPN's configuration file can be altered to include arbitrary code can then pass to the service and executed with system rights under Windows.
The bug is similar to one disclosed in April by Fabius Watson of VerSprite security consulting firm, who showed that OpenVPN service would accept and run a configuration file containing a parameter like "plugin" or "script-security."
Both NordVPN and ProtonVPN fixed this by implementing a check for the presence of the two dangerous parameters as well as "up" and "down," which are all methods to execute code or commands via OpenVPN.
Looking through the OpenVPN source code for the configuration file parser, Rascagnares noticed that these controls were insufficient and the same effect could be achieved by placing the parameters between quotation marks.The researcher showed that by adding the following text to the configuration file
"script-security" 2
"up" C:\\WINDOWS\\system32\\notepad.exe
ProtonVPN and NordVPN launched the Notepad application on Windows.
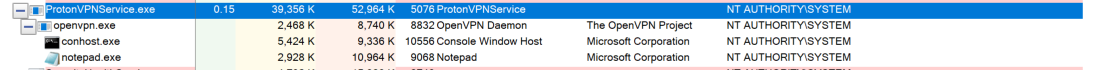
The two security bugs are currently tracked as CVE-2018-3952 for NordVPN and CVE-2018-4010 for ProtonVPN, and have a severity rating of 8.8, out of a maximum of 10.
Rascagnares disclosed the faults to the two VPN providers on July 5 and NordVPN released a patch on August 8, while ProtonVPN offered a fix on September 3.
This time, the two vendors opted for different corrective methods:
"The For ProtonVPN, they put the OpenVPN configuration file in the installation directory, and a standard user cannot modify it. Thus, we cannot add the malicious string in it. For NordVPN, the editor decided to use an XML model to generate an OpenVPN configuration file. A standard user cannot edit the template," Rascagnares discloses in a blog post today.
The client versions affected by the privilege escalation bug are ProtonVPN 1.5.1 and NordVPN 6.14.28.0. NordVPN users are automatically updated to the latest release of the application, while those using PrototonVPN need to start the process manually.
Update: ProtonVPN contacted BleepingComputer to inform that an update that fixed the vulnerability was released to all its users prior to Cisco publishing the report.


Comments
RansomBleed - 5 years ago
Would be interesting to know if that eventually works on Linux as well.
SassyScooper - 5 years ago
You scared me! They fixed it several months ago. I don't understand why you're writing about things that do not exist anymore. More VPNs are based on the OpenVPN configuration file and have faced CVE issues. Windscribe, Pure and OpenVPN had similar cases too.