
Threat analysts report that zero-day vulnerability exploitation is on the rise, with Chinese hackers using most of them in attacks last year.
Zero-day vulnerabilities are security weaknesses in software products that are either unknown or have not been fixed at the time of discovery
Zero-day disclosures are of particular interest to hackers because they have a wider exploitation window until vendors address the flaws and clients start applying the updates.
Typically, this window of opportunity lasts for at least a couple of days, and since not all admins apply security updates immediately, the number of vulnerable targets remains high for a while.
2021 zero-day landscape
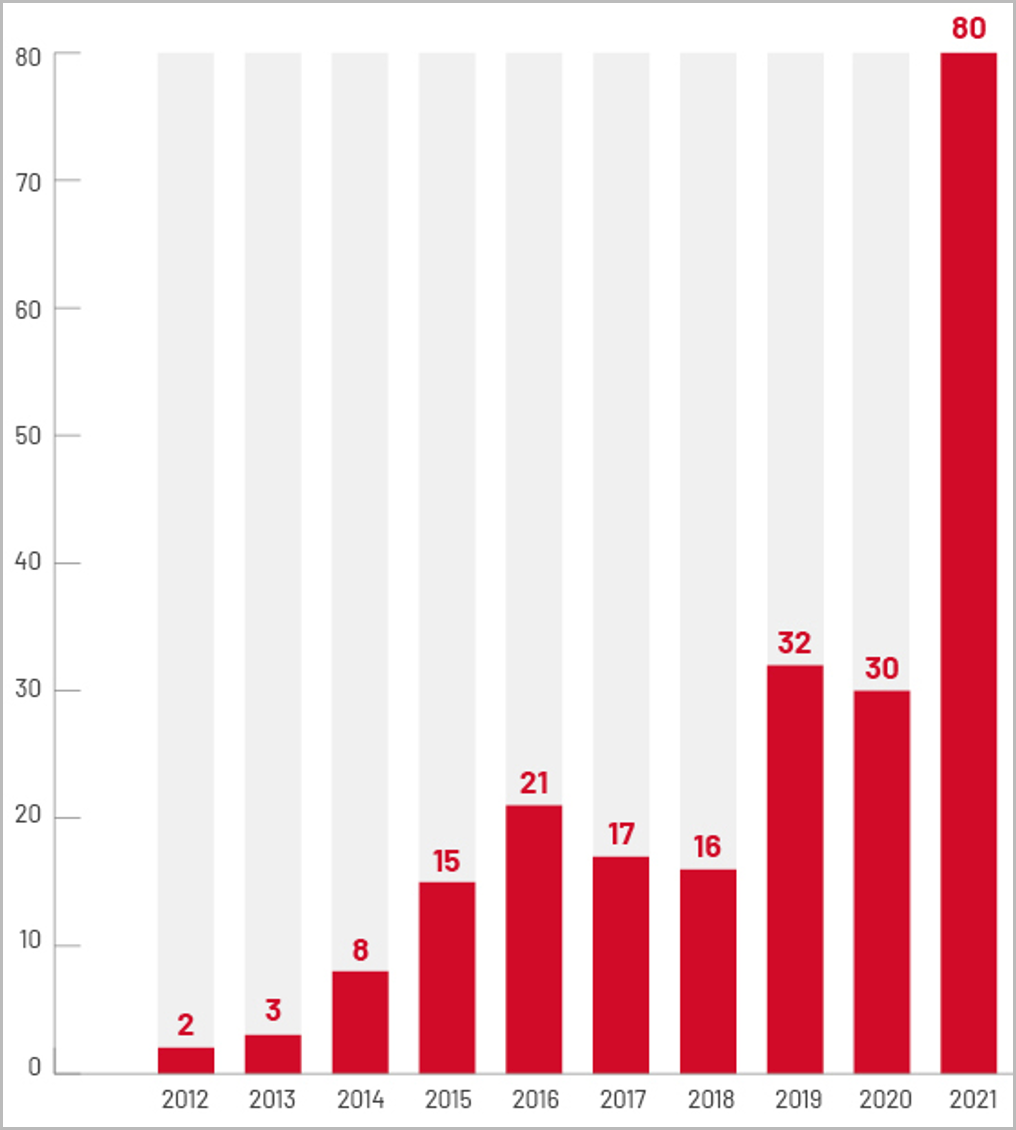
According to an analysis from cybersecurity firm Mandiant, last year there were 80 cases of zero-days exploited in the wild, 18 more than 2020 and 2019 combined.
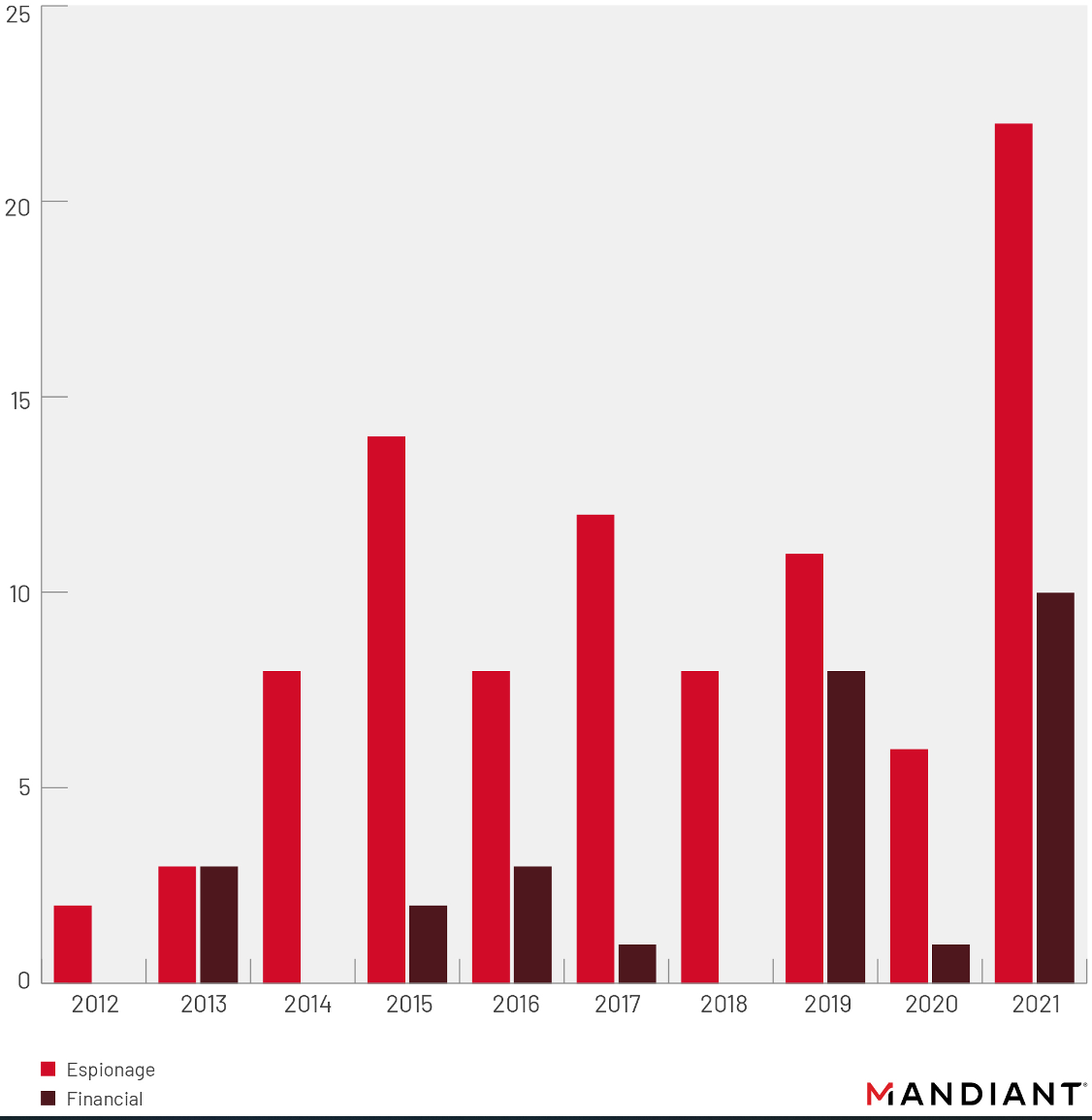
Most of them were attributed to cyberespionage operations from state-backed actors.
However, the company found that one out of three malicious actors exploiting zero-day vulnerabilities was financially motivated, a statistic that continues a growing trend from previous years.
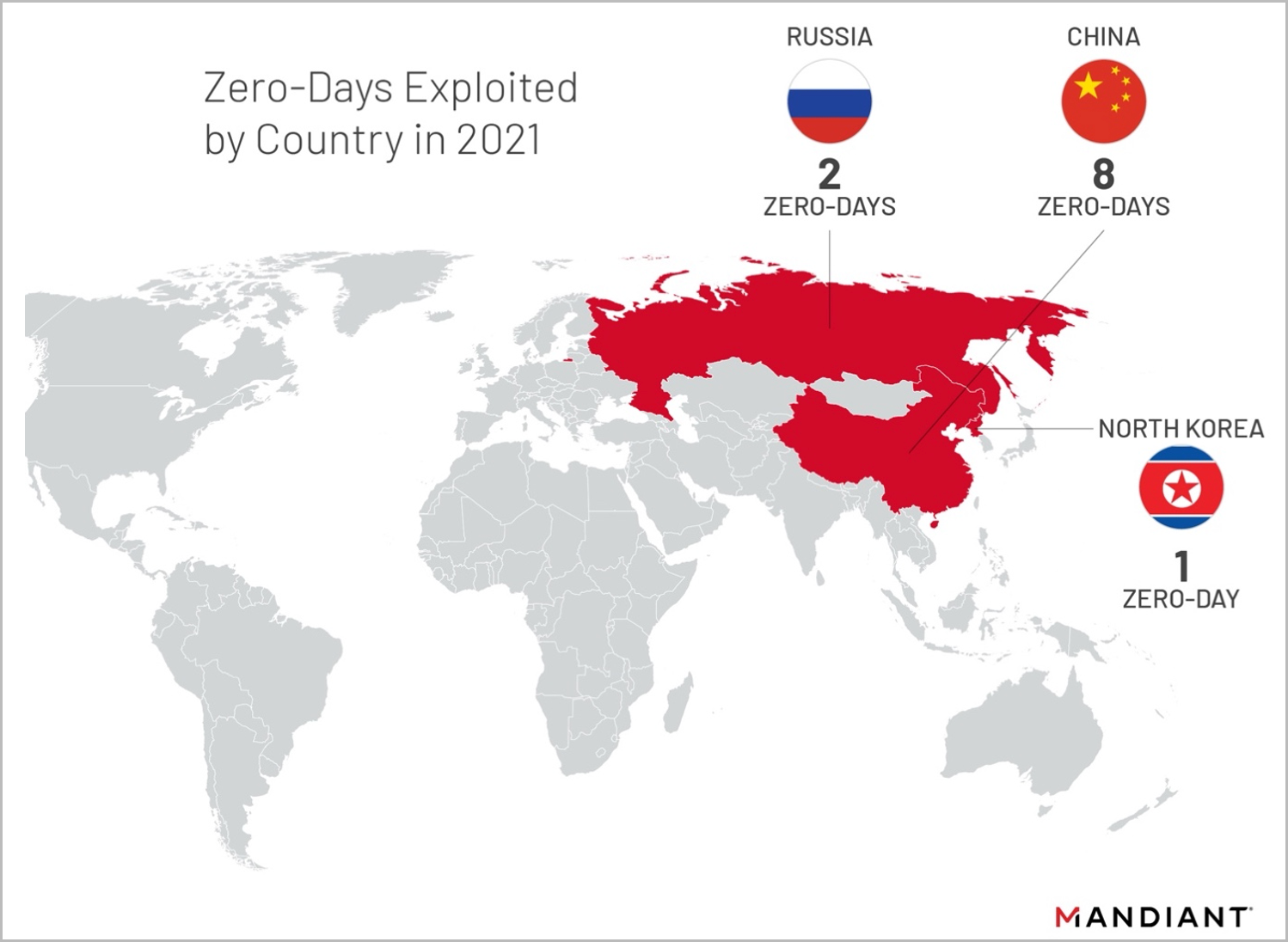
In terms of threat actors, China tops the list with eight zero-days used in cyberattacks in 2021, followed by Russia which used two, and North Korea with one.
The most notable case was that of Hafnium, a Chinese state-sponsored hacking group that utilized four zero-day vulnerabilities on the Microsoft Exchange servers to access email communications of Western organizations.
Mandiant also recorded an uptick in ransomware operatives exploiting zero-day flaws to breach networks and deploy their file-encrypting payloads.
One prominent example of this activity was that of HelloKitty ransomware operators, who exploited a zero-day bug in SonicWall SMA 100 VPN appliances.
The most targeted vendors in 2021 zero-day attacks were Microsoft, Apple, and Google, accounting for over 75% of all attacks.
As BleepingComputer reported recently, the number of mobile OS zero-days targeting Android and iOS is also on an ascending trend, going from under five in 2019 and 2020 to 17 in 2021.
.png)
What to expect in 2022
Last year saw a record break in zero-day exploitation, and current evidence indicates that it will be worse this year.
“We suggest that significant campaigns based on zero-day exploitation are increasingly accessible to a wider variety of state-sponsored and financially motivated actors, including as a result of the proliferation of vendors selling exploits and sophisticated ransomware operations potentially developing custom exploits” - Mandiant
Google’s Project Zero team on Tuesday published a report on the same topic, underlining that the rise in zero-day exploitation is partly a result of greater visibility and detection and not necessarily an increase of activity or attacks' complexity.
As the report details, only two out of 58 new zero-days Project Zero disclosed in 2021 exhibit technical excellence and uniqueness, which could point to software security maturity.


Comments
yawnshard - 1 year ago
Name me one nation state without dirt. Any exploit used by the "enemy" is good, because then an exploit gets closed faster.
We would never had the drama if NSA closed their own EternalBlue and just reported them as CVE. Always assume, if you can find and 0day, other nations can too.
Close them, spooks, even if you lose access yourself.