
The Russian-backed Turla cyber-espionage group used stolen malware and hijacked infrastructure from the Iranian-sponsored OilRig to attack targets from dozens of countries according to a joint United Kingdom's National Cyber Security Centre (NCSC) and U.S. National Security Agency (NSA) advisory published today.
Turla is an advanced threat group tracked by security outfits as Waterbug, Snake, WhiteBear, VENOMOUS BEAR, and Kypton, an advanced persistent threat (APT) group with a focus on cyber-espionage and a wide range of victims, from military and government to education and research entities. [1, 2, 3]
Also monitored under multiple monickers (Crambus, APT34, and HelixKitten), OilRig is an APT with Iranian government links known for operating worldwide cyber-espionage campaigns, usually targeting Middle Eastern companies and government agencies.
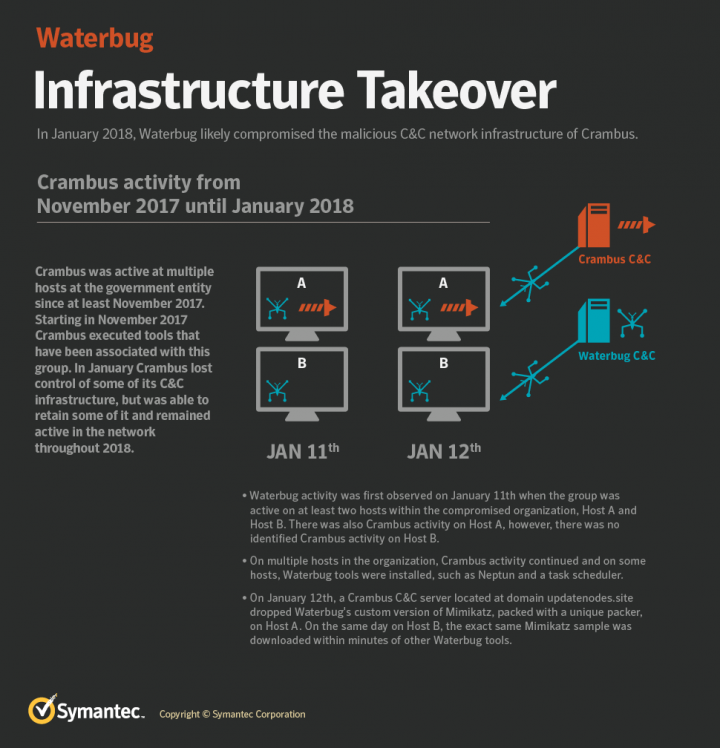
Turla's hijack of OilRig's infrastructure was previously documented in June by Symantec whose researchers observed the Russian APT while using some of the Iranians' command and control (C2) servers to compromise the system of a target from the Middle East.
Earlier during 2019, in January, the NCSC published yet another advisory detailing Turla's use of multiple Iranian malicious tools including the Neuron and Nautilus implants, an ASPX-based backdoor beside the Snake rootkit, to compromise, maintain persistence, and exfiltrate data.
Turla as OilRig as Turla
Turla used victim networks previously compromised using Snake to find servers infected with the ASPX shells "in at least 35 countries, including Saudi Arabia, Kuwait, Qatar and UAE."
"Victims in this region included military establishments, government departments, scientific organizations and universities. Some of these victims, but not all, also had a Snake implant present," adds NCSC's advisory.
"After acquiring the tools – and the data needed to use them operationally –Turla first tested them against victims they had already compromised using their Snake toolkit, and then deployed the Iranian tools directly to additional victims," says the NSA advisory.
"Turla sought to further their access into victims of interest by scanning for the presence of Iranian backdoors and attempting to use them to gain a foothold. The focus of this activity from Turla was largely in the Middle East, where the targeting interests of both Advanced Persistent Threats (APTs) overlap."
While attribution of attacks and proving authorship of tools can be very difficult – particularly in the space of incident response on a victim network – the weight of evidence demonstrates that Turla had access to Iranian tools and the ability to identify and exploit them to further Turla’s own aims. — NCSC/NSA
While investigating Turla's operations, the two government agencies were able to observe that, while some of the malware implants were dropped using the Russian group's infrastructure, they were later being used or they were connecting to Virtual Private Server (VPS) IP addresses connected to the OilRig Iranian APT group.
This shows how Turla abused OilRig's C2 servers and malware to run their own operations, just as it does the fact that the Russian hackers were seen dropping the Iranian's Neuron implants on systems of victims already compromised using Turla's Snake rootkit.
Definitely not teamwork
All of this happened while Turla was also exfiltrating data from OilRig's infrastructure, including but not limited to "directory listings and files, along with keylogger output containing operational activity from the Iranian actors, including connections to Iranian C2 domains."
This allowed the Russian hackers to get an eagle-eye view of the Iranian APT group's tactics, techniques and procedures (TTPs), as well as to "lists of active victims and credentials for accessing their infrastructure, along with the code needed to build versions of tools such as Neuron for use entirely independently of Iranian C2 infrastructure."
On top of it, according to the advisory, the Iranian hacking group wasn't aware that someone else was using their malware and C2 servers, nor were they part of a joint hacking effort. "Those behind Neuron or Nautilus were almost certainly not aware of, or complicit with, Turla’s use of their implants," says the NSA.
In support of the two hacking groups not working together, the advisory also states that while Turla "had a significant amount of insight into the Iranian tools, they did not have full knowledge of where they were deployed."


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now