-
Cheddar Scratch Kitchen Exposes Card Data of Over 500,000
Restaurants in 23 states are on the list of Cheddar Scratch Kitchen locations affected by a cyberattack that exposed payment card information.
- August 23, 2018
- 07:14 PM
-
 0
0
-
Cybercriminals Undeterred by ToS For Remcos RAT
Researchers from Cisco Talos are calling out the developer of a remote administration tool (RAT) for allowing its use for malicious purposes.
- August 23, 2018
- 04:00 PM
-
 2
2
-
Microsoft Rolls Out New Intel Microcode for Windows 10, Server 2016
Microsoft has released multiple microcode updates that mitigate additional variants of the speculative code execution vulnerabilities discovered in Intel processors. The patches cover the recently disclosed CPU flaws generically referred to as Foreshadow or L1 Terminal Fault.
- August 22, 2018
- 07:03 PM
-
 0
0
-
Turla Outlook Backdoor Uses Clever Tactics for Stealth and Persistence
The Outlook backdoor Turla APT group uses for espionage operations is an unusual beast built for stealth and persistence, capable to survive in highly restricted networks.
- August 22, 2018
- 05:15 PM
-
 0
0
-
Legacy System Exposes Contact Info of BlackHat 2018 Attendees
Full contact information of everyone attending the BlackHat security conference this year has been exposed in clear text, a researcher has found. The data trove includes name, email, company, and phone number.
- August 22, 2018
- 08:55 AM
-
 1
1
-
Supply Chain Attack Hits Organizations In South Korea
Security researchers have uncovered a new supply chain attack that targets organizations in South Korea. The threat actor chooses the victims selectively, based on an IP range for groups of interest.
- August 22, 2018
- 05:38 AM
-
 0
0
-
TLS Certs Outliving Domain Ownership Open Door to MitM and DoS
Digital certificates that allow secure data exchange over the internet can survive domain ownership transfer and can open the door for malicious actions to the previous holder.
- August 21, 2018
- 11:04 AM
-
 0
0
-
USBHarpoon Is a BadUSB Attack with A Twist
Several security experts have built a malicious version of a USB charging cable, one that can compromise a computer in just a few seconds. Once plugged in, it turns into a peripheral device capable of typing and launching commands.
- August 20, 2018
- 05:54 PM
-
 7
7
-
Apple Cleans Chinese App Store of Thousands of Fake Apps
Apple has purged its Chinese App Store of fake gambling and lottery software. The company also banned a number of developers that tried to peddle these apps through its market.
- August 20, 2018
- 11:58 AM
-
 0
0
-
Zero-Day In Microsoft's VBScript Engine Used By Darkhotel APT
A vulnerability in the VBScript engine has been used by hackers working for North Korea to compromise systems targeted by the Darkhotel operation.
- August 18, 2018
- 06:02 AM
-
 0
0
-
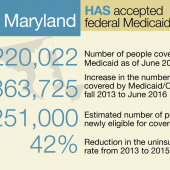
Severe Security Gaps In Maryland's Medicaid Management Information System
Maryland's Medicaid program is threatened by security gaps exposing data and information systems to unauthorized access and disruption of critical operations.
- August 16, 2018
- 01:37 PM
-
 0
0
-
Synthetic Clicks (Still) Work for Sensitive macOS Security Alerts
Bypassing security prompts in High Sierra, the latest version of macOS, is still possible with synthetic clicks thanks to a bug triggered by just two lines of code.
- August 16, 2018
- 03:31 AM
-
 0
0
-
Microsoft Cortana Flaw Could Allow Browsing on Locked Systems
Security researchers have shown that having Microsoft Cortana enabled on the Windows lock screen could be a security risk. In such a configuration, users could compromise a system or lead to or impersonate a user using credentials stored in the browser cache.
- August 15, 2018
- 12:00 AM
-
 0
0
-
A First Look at the North Korean Malware Family Tree
Security researchers have analyzed malware samples from threat actors associated with North Korea and discovered connections with tools from older unattributed campaigns.
- August 09, 2018
- 09:34 AM
-
 0
0
-
DarkHydrus Relies on Open-Source Tools for Phishing Attacks
A threat actor named DarkHydrus that is relatively new to the scene relies on open-source tools for spear-phishing attacks designed to steal credentials from government and educational institutions in the Middle East.
- August 08, 2018
- 06:32 PM
-
 0
0