
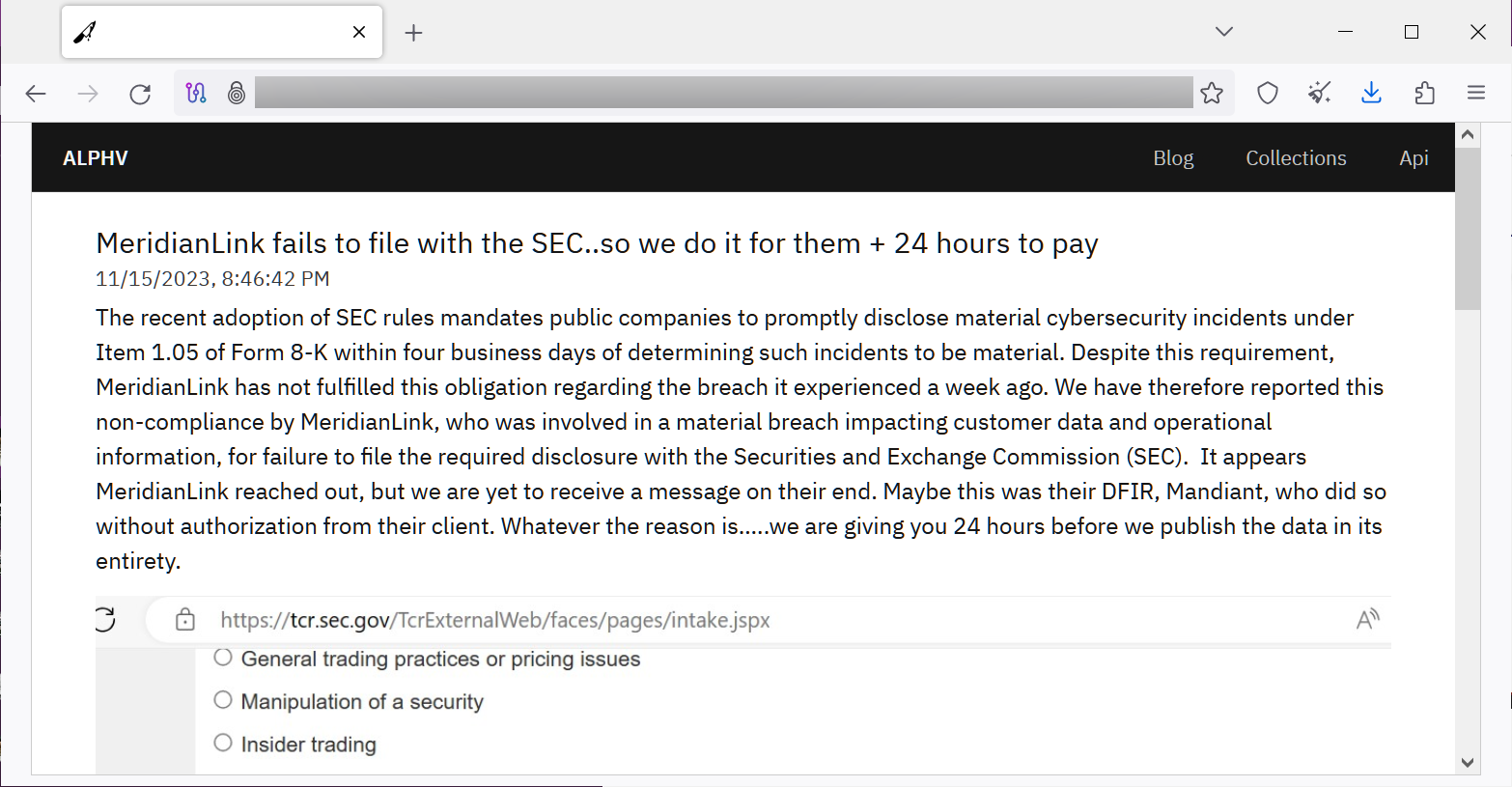
The ALPHV/BlackCat ransomware operation has taken extortion to a new level by filing a U.S. Securities and Exchange Commission complaint against one of their alleged victims for not complying with the four-day rule to disclose a cyberattack.
Earlier today, the threat actor listed the software company MeridianLink on their data leak with a threat that they would leak allegedly stolen data unless a ransom is paid in 24 hours.
MeridianLink is a publicly traded company that provides digital solutions for financial organizations such as banks, credit unions, and mortgage lenders.
Hackers snitch to the SEC
According to DataBreaches.net, the ALPHV ransomware gang said they breached MeridianLink’s network on November 7 and stole company data without encrypting systems.
The ransomware actor said that “it appears MeridianLink reached out, but we are yet to receive a message on their end” to negotiate a payment in exchange for not leaking the supposedly stolen data.
The alleged lack of response from the company likely prompted the hackers to exert more pressure by sending a complaint to the U.S. Securities and Exchange Commission (SEC) about MeridianLink not disclosing a cybersecurity incident that impacted “customer data and operational information.”
source: BleepingComputer
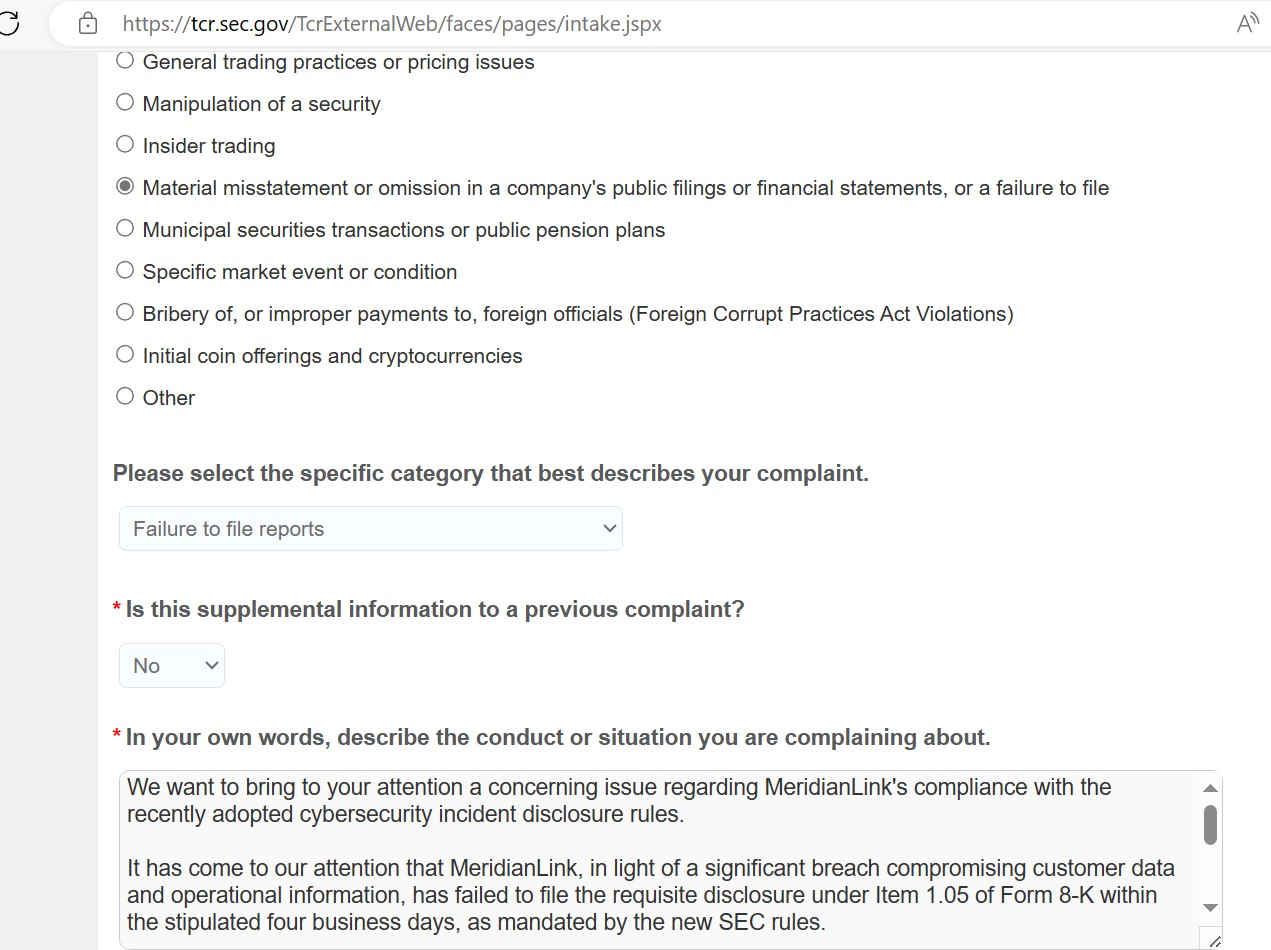
To show that their complaint is real, ALPHV published on their site a screenshot of the form they filled out on SEC’s Tips, Complaints, and Referrals page.
In their own words, the attacker told the SEC that MeridianLink suffered a “significant breach” and did not disclose it as required in Form 8-K, under Item 1.05.
source: BleepingComputer
Following a barrage of security incidents at U.S. organizations, the SEC adopted new rules that require publicly traded companies to report cyberattacks that have a material impact, i.e. influence investment decisions.
Cybersecurity incident reporting is “due four business days after a registrant determines that a cybersecurity incident is material,” the new rule states.
However, the SEC’s new cybersecurity rules are set to take effect on December 15, 2023, Reuters explained at the beginning of October.
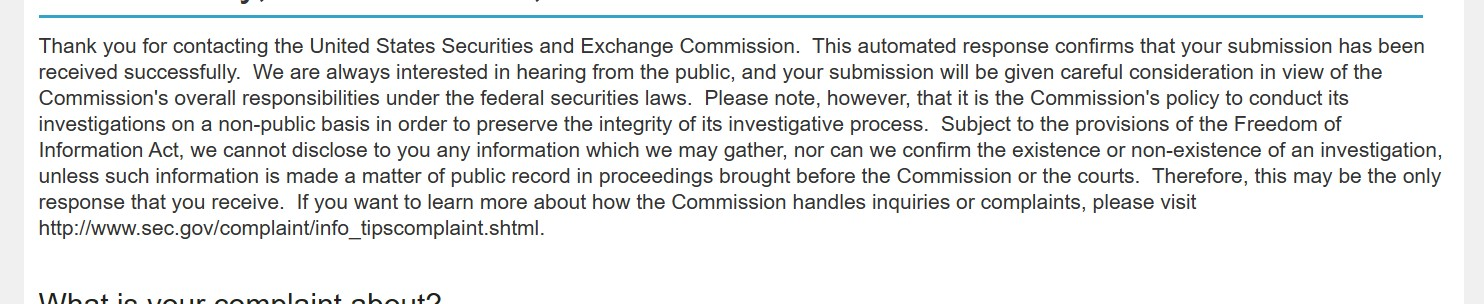
ALPHV also provided on their site the reply they received from the SEC to the complaint against MeridianLink, to show that the submission was received.
source: BleepingComputer
MeridianLink confirms cyberattack
In a statement for BleepingComputer, MeridianLink said that after identifying the incident it acted immediately to contain the threat and engaged a team of third-party experts to investigate.
The company added that it is still working to determine if any consumer personal information was impacted by the cyberattack and it will notify affected parties if so.
“Based on our investigation to date, we have identified no evidence of unauthorized access to our production platforms, and the incident has caused minimal business interruption.” - MeridianLink
While many ransomware and extortion gangs have threatened to report breaches and data theft to the SEC, this may be the first public confirmation that they have done so.
Previously, ransomware actors exerted pressure on victims by contacting customers to let them know of the intrusion. Sometimes, they would also try to intimidate the victim by contacting them directly over the phone.


Comments
gryphenwings - 3 months ago
I'm in no way condoning the ransome ware eco-system, but this does make you wonder if US cyber-security could have a division that tests various public and private networks. Something along the lines of "we've breached your systems, now show us the fix or you're stuck for a while". I get that sounds like big brother encroaching on private systems, but for gods sake, companies aren't going to fix their code flaws if nobody is trying to penetrate their systems.
h_b_s - 3 months ago
What makes you think a government administrative agency would have any more success than the thousands of researchers out there hunting for bug bounties?
The problem is structural and regulatory, not from a lack of workers. The computer use industry is based around cycles of updates. Successful attackers are inside those cycles so they can manage entry before IT teams can update. Long update cycles are both a problem of neglectful management, and in some cases, arthritic regulatory regimes that demand certain certifications be adhered to. Those certification processes take time and money and are too antiquated to deal with the current cyber security landscape. They were designed for safety and reliability, but not security.
Neglectful management is curable. You make management directly accountable for their negligence in data security. Note I said "negligence", not for breaches, there's a difference. You can be doing everything you can possibly do, and still be successfully attacked.
Regulatory regime change requires a functioning, competent legislative branch, and the US doesn't have that right now... arguably neither does the EU in as far as being competent is concerned (Article 45 anyone?).
Staylormoon - 3 months ago
Funny you should mention that:
https://www.cisa.gov/
They do pen testing and monitoring, this business I think would be on their critical list and could receive their services.
NoneRain - 3 months ago
Zero attention, zero payment. ALPHV crying on forums and issuing complains to authorities lol
For more companies with attitude like MeridianLink, (just don't "forget" to report to SEC if the leak indeed happened)
DyingCrow - 3 months ago
This is way, way too funny :)
AlGor1979 - 3 months ago
In other words the SEC is one more tool in the ransomware arsenal. Instead of pushing real protection from ransomware and viruses (I mean the Recordable Drive technology) bureaucrats are punishing victims.
h_b_s - 3 months ago
No, they're punishing management for being irresponsible douches for not notifying investors and customers their systems had been breached and therefore at risk of personal compromise.
You have no clue what you're talking about.
AlGor1979 - 3 months ago
Sorry to inform you, but you are wrong. “Management being irresponsible”? How do you know? Management can do everything the SEC demands and still be hacked. Because the current multi-billion dollar anti-ransomware industry does not give real protection to people. Actually, they do want more attacks because it helps them to take more money from companies for their useless recommendations. They do not like and they do not mention the Recordable Drives because it is the end of their business.
Recordable Drive technology has been available for many years. It creates complete, 100%, hardware based protection against ransomware and many other cyber-attacks. Once a file is recorded, it cannot be modified in any way, it cannot be encrypted by ransomware, it cannot be infected by a virus.
Does the SEC or any other government agency promote this technology? No, they take the side of ransomware criminals and attack the victims together giving to the criminals even more power.
Fever905 - 3 months ago
Maybe they are shorting the stock. Doesn't this formula make sense? Hack a company, short the stock, force the SEC reporting, make money whether they pay or not.
AlGor1979 - 3 months ago
Exactly! It is one more tool in the ransomware arsenal. More pressure on the victim.