
PayPal has filed a patent application for a novel method that can identify when "super-cookie" is stolen, which could improve the cookie-based authentication mechanism and limit account takeover attacks.
The risk that PayPal wants to address is that of hackers stealing cookies containing authentication tokens to log into victim accounts without the need for valid credentials and bypassing two-factor authentication (2FA).
"The theft of cookies is a sophisticated form of cyberattack, where an attacker steals or copies cookies from a victim's computer onto the attacker's web browser," PayPal says in the patent application.
"With stolen cookies often containing hashed passwords, the attacker can use a web browser on the attacker's computer to impersonate the user (or authenticated device thereof) and gain access to secure information associated with the user's account without having to manually login or provide authentication credentials," it is further explained.
System details
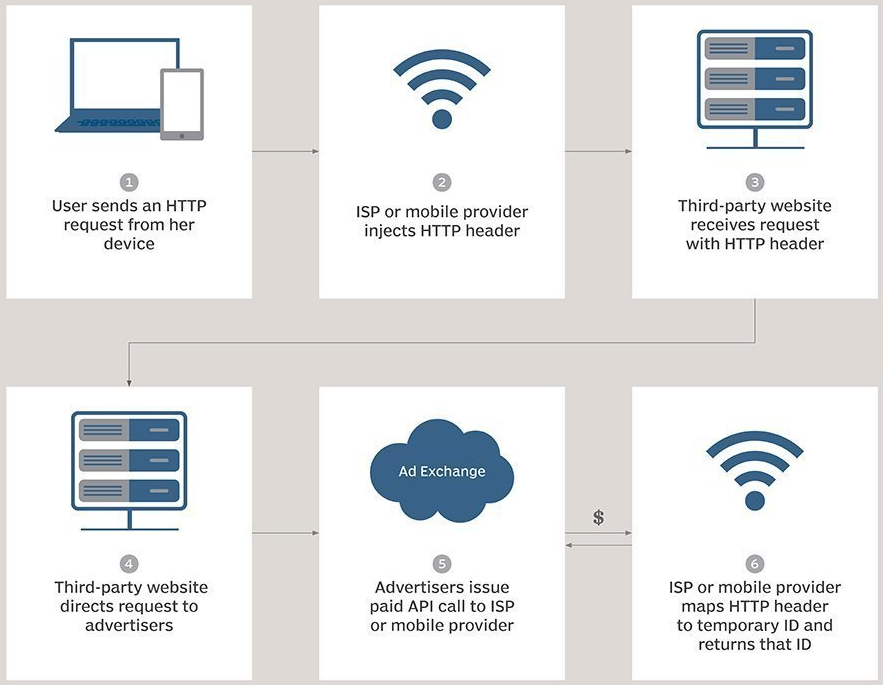
Unlike standard cookies stored locally, super-cookies (also referred to as "Flash cookies") are Local Shared Objects (LSOs) that are injected at the network level as unique identifier headers (UIDH) by the user's internet service provider (ISP).
These super-cookies are used primarily for cross-site tracking, following users across different browsers on the same device, collecting data on browsing activity, and serving as persistent "device fingerprints."
Super-cookies are more difficult to detect and wipe because they are not stored in the browser's standard cookie storage location.
PayPal's engineers have identified a method to calculate a fraud risk score in the cookie-based authentication mechanism to identify fraudulent login attempts on the electronic payments platform.
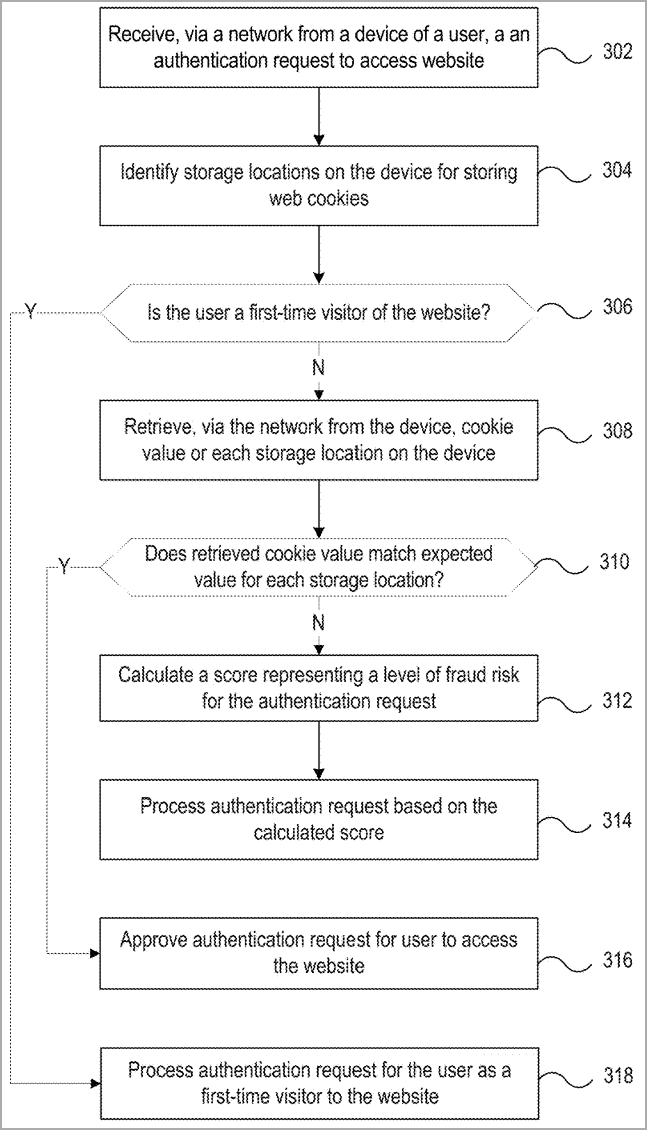
When a system receives a request for authentication from a user's device, it identifies the various cookie storage locations on the device and sorts them "in order of increasing fraud risk."
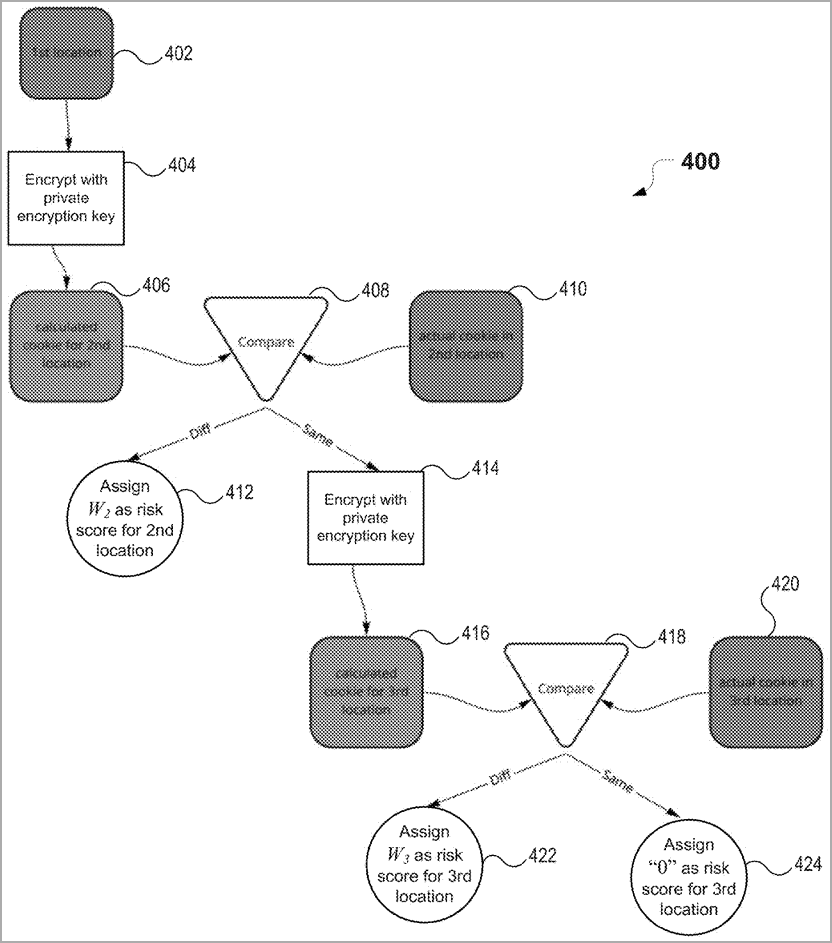
"A cookie value for each storage location is retrieved from the device. For each storage location after the first: an expected cookie value is calculated based on the cookie value of a preceding storage location," reads the abstract of the patent application.
PayPal's system then assesses a risk score by comparing the expected cookie values with the values assigned for the device's storage locations.
"The authentication request is processed based on whether the assigned score for at least one of the storage locations exceeds a predetermined risk tolerance for fraud detection."
Based on the risk assessment, the system manages the authentication requests accordingly, accepting, rejecting, or activating additional security measures for the approval of the login attempt.
To ensure safety against tampering, the retrieved cookie values are encrypted using a public key cryptographic algorithm.
PayPal's patent describes a method that aims to defend against cyberattacks by ensuring that cookies are used legitimately during the authentication process.
The electronic payments giant filed the patent titled "Super-Cookie Identification for Stolen Cookie Detection" in July 2022, and it was published by the United States Patent and Trademark Office earlier this month.
As with all patents, there's no guarantee that the tech described in the document will reach consumer portals, in that form or another, but it shows that stolen web cookies for unauthorized logins are enough of a problem to deserve new protection mechanisms.


Comments
nauip - 1 week ago
Girl Scouts everywhere rejoice!
h_b_s - 1 week ago
The article's last paragraph is very appropriate. It should be cautionary to stake holders and industry participants and observers: there's a net benefit to society when useful technologies are open to all comers. When a company patents otherwise useful software technology, the only benefit is to themselves. It's likely never to see wider adoption without a royalty free grant to open source projects because no one likes being sued. (Granted, that's assuming this scheme actually works and implementations aren't easily circumvented.)
b1k3rdude - 1 week ago
Indeed, this is PayPay, a thoroughly despicable company, founded by Peter Thiel, a thoroughly despicable human.