
In 2023, we saw numerous law enforcement operations targeting cybercrime operations, including cryptocurrency scams, phishing attacks, credential theft, malware development, and ransomware attacks.
While some of these operations were more successful than others, law enforcement has been increasingly using hack-back tactics to infiltrate operations and disrupt them.
BleepingComputer has provided a non-exhaustive list of these operations below in chronological order:
Hive ransomware disrupted after FBI hacks gang's systems
The US Department of Justice and Europol announced that an international law enforcement operation secretly infiltrated the Hive ransomware gang's infrastructure in July 2022, when they secretly began monitoring the operation for six months.
The Hive ransomware's Tor payment and data leak sites were then seized by the FBI in January 2023.

The ransomware gang has not been spotted until recently when they are believed to have rebranded as the Hunters International ransomware group.
Police hacked Exclu 'secure' message platform to snoop on criminals
The Dutch police dismantled the Exclu encrypted communications platform after hacking into the service to monitor the activities of criminal organizations.
The operation consisted of two separate investigations, starting in September 2020 and April 2022, when the police also carried out 79 targeted searches in the Netherlands, Germany, and Belgium and arrested 42 people.
Core DoppelPaymer ransomware gang members targeted in Europol operation
Law enforcement in Germany and Ukraine targeted two individuals believed to be core members of the DoppelPaymer ransomware group.
The operation consisted of raiding multiple locations in the two countries in February and was the result of a coordinated effort that also involved Europol, the FBI, and the Dutch Police.
Police seize Netwire RAT malware infrastructure, arrest admin
An international law enforcement operation involving the FBI and police agencies worldwide led to the arrest of the suspected administrator of the NetWire remote access trojan and the seizure of the service’s web domain and hosting server.
NetWire was a remote access trojan promoted as a legitimate remote administration tool to manage a Windows computer remotely.
Since at least 2014, NetWire has been a tool of choice in various malicious activities, including phishing attacks, BEC campaigns, and to breach corporate networks.
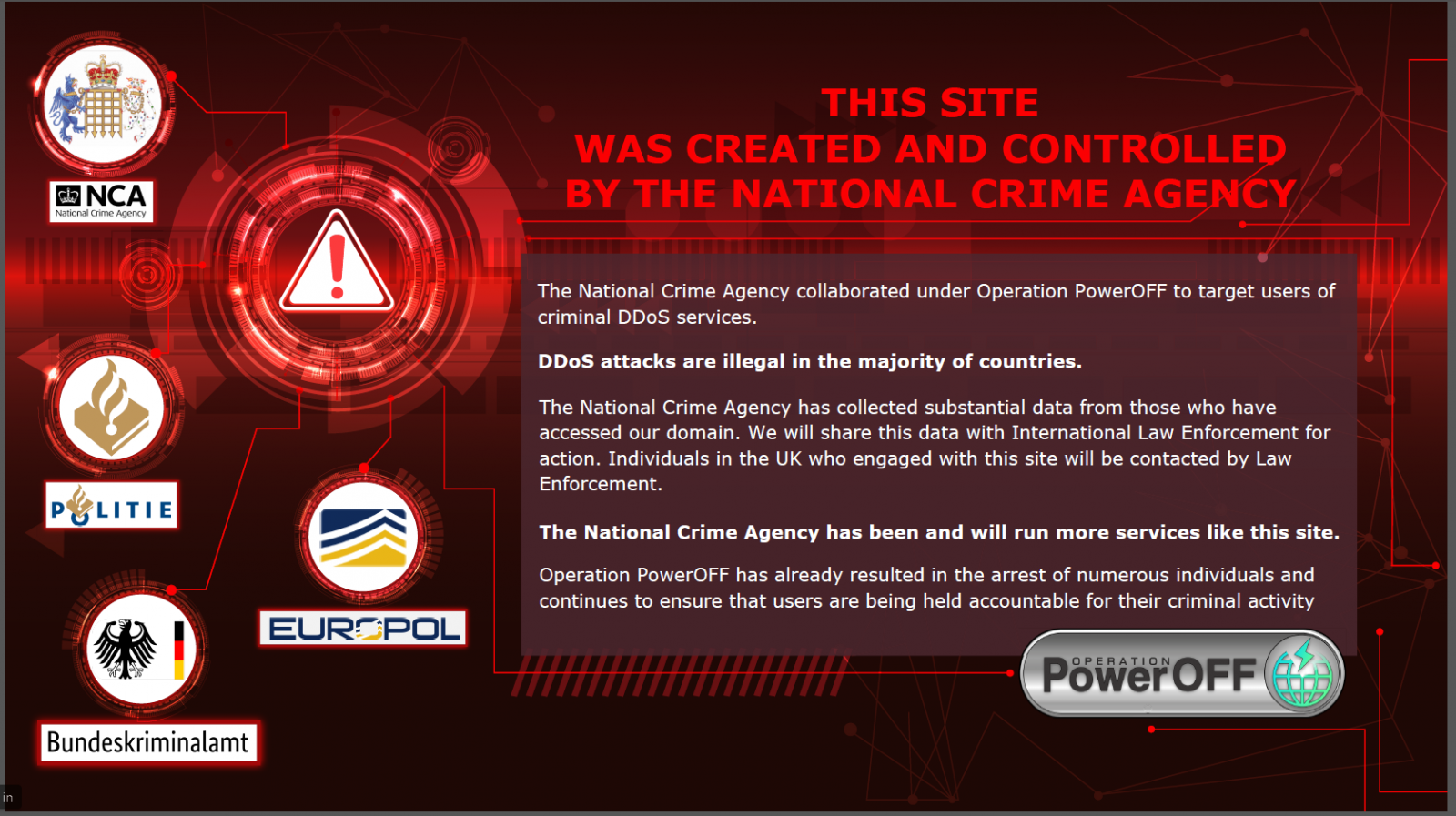
UK creates fake DDoS-for-hire sites to identify cybercriminals
As part of Operation PowerOFF, The U.K.'s National Crime Agency (NCA) created multiple fake DDoS-for-hire service websites to identify cybercriminals who utilize these platforms to attack organizations.
NCA says several thousands of people accessed its fake sites, which had a realistic appearance as a genuine booter service. However, instead of giving access to DDoS tools, they only served to collect information about those who wished to use these services.
After successfully infiltrating the cybercrime market and gathering information about those purchasing illegal services, the agency revealed the operation by displaying a splash page on only one of its fake sites.
US seizes $112 million from cryptocurrency investment scammers
The U.S. Department of Justice seized six virtual currency accounts containing over $112 million in funds stolen in cryptocurrency investment schemes.
The criminals behind these cryptocurrency fraud scams (also known as pig butchering or cryptocurrency confidence scams) approach their victims via various dating platforms, messaging apps, or social media platforms, build trust, and introduce them to investment schemes which eventually allow them to empty the targets' crypto wallets.
The DOJ says the next step is to return the stolen cryptocurrency to the victims.
FBI seizes stolen credentials market Genesis in Operation Cookie Monster
The domains and infrastructure for Genesis Market, one of the most popular marketplaces for stolen credentials of all types, were seized by law enforcement earlier this week as part of Operation Cookie Monster.
Genesis Market's full database had 1.5 million bots supplying more than 2 million identities; more than 460,000 bots were available for sale at the time of the takedown. In total, the platform offered about 80 million credentials and digital fingerprints, says UK's National Crime Agency.
Police operation 'SpecTor' arrests 288 dark web drug vendors and buyers
An international law enforcement operation codenamed 'SpecTor' has arrested 288 dark web vendors and customers worldwide, with police seizing €50.8 million ($55.9M) in cash and cryptocurrency.
The vendors were active in a marketplace known as the 'Monopoly Market' that sold drugs to customers worldwide in exchange for Bitcoin and Monero cryptocurrency.
FBI seizes 9 crypto exchanges used to launder ransomware payments
The FBI and Ukrainian police have seized nine cryptocurrency exchange websites that facilitated money laundering for scammers and cybercriminals, including ransomware actors.
The operation was carried out with the help of the Virtual Currency Response Team, the National Police of Ukraine, and legal prosecutors in the country.
FBI seizes BreachForums after arresting its owner Pompompurin in March
U.S. law enforcement today seized the clear web domain of the notorious BreachForums (aka Breached) hacking forum three months after apprehending its owner Conor Fitzpatrick (aka Pompompurin), under cybercrime charges.
Hosted at Breached[.]vc, the domain now shows a seizure banner saying the website was taken down by the FBI, the Department of Health and Human Services, the Office of Inspector General, and the Department of Justice based on a warrant issued by the U.S. District Court for the Eastern District of Virginia.

EncroChat takedown led to 6,500 arrests and $979 million seized
Europol took down the EncroChat encrypted mobile communications platform, which has led to the arrest of over 6,600 people and the seizure of $979 million in illicit funds.
EncroChat phones ran a special, hardened version of Android that promised users unbreakable encryption, anonymity, and no traceability.
In 2020, a large-scale European law enforcement operation quietly infiltrated the EncroChat platform and was able to analyze millions of messages shared between its users after breaking the encryption algorithm.
After analyzing 15 million conversations between roughly 60,000 users of the platform, police have arrested 6,558 users of EncroChat, including 197 high-value targets.
The data also allowed the police to locate and seize 270 tons of drugs, 971 vehicles, 271 properties, 923 weapons, 68 explosives, 40 planes, and 83 boats.
Qakbot botnet dismantled after infecting over 700,000 computers
The FBI disrupted the Qakbot botnet by seizing infrastructure and pushing out a module that uninstalled the malware from infected devices.
The botnet (also known as Qbot and Pinkslipbot) was linked by law enforcement to at least 40 ransomware attacks against companies, healthcare providers, and government agencies worldwide, causing hundreds of millions of dollars in damage, according to conservative estimates. Over the past 18 months alone, losses have surpassed 58 million dollars.
Throughout the years, Qakbot has consistently served as an initial infection vector for various ransomware gangs and their affiliates or operators, including Conti, ProLock, Egregor, REvil, RansomExx, MegaCortex, and, most recently, Black Basta.
However, the success of this law enforcement operation may be short-lived, as cybersecurity researchers have already seen QakBot rebuilding its botnet.
Ragnar Locker ransomware’s dark web extortion sites seized by police
The Ragnar Locker ransomware operation's Tor negotiation and data leak sites were seized as part of an international law enforcement operation.
Visiting either website now displays a seizure message stating that a large assortment of international law enforcement from the US, Europe, Germany, France, Italy, Japan, Spain, Netherlands, Czech Republic, and Latvia were involved in the operation.

Police dismantle ransomware group behind attacks in 71 countries
In cooperation with Europol and Eurojust, law enforcement agencies from seven nations have arrested the core members of a ransomware group linked to attacks against organizations in 71 countries.
The cybercriminals paralyzed major corporations' operations in attacks using ransomware such as LockerGoga, MegaCortex, HIVE, and Dharma.
FBI disrupts Blackcat ransomware operation, creates decryption tool
The FBI hacked the ALPHV ransomware operation's servers to monitor their activities and obtain decryption keys for victims.
BleepingComputer first reported that the ALPHV, aka BlackCat, websites suddenly stopped working, including the ransomware gang's Tor negotiation and data leak sites.
While the ALPHV admin claimed it was a hosting issue, BleepingComputer learned it was related to a law enforcement operation.
Ten days later, the Department of Justice confirmed our reporting, stating that the FBI conducted a law enforcement operation that allowed them to gain access to ALPHV's infrastructure.
With this access, the FBI monitored the ransomware operation for months while siphoning decryption keys and sharing them with victims.
Interpol operation arrests 3,500 cybercriminals, seizes $300 million
An international law enforcement operation codenamed 'Operation HAECHI IV' has led to the arrest of 3,500 suspects of various lower-tier cybercrimes and seized $300 million in illicit proceeds.
The latest operation, which occurred between July and December 2023, targeted threat actors engaging in voice phishing, romance scams, online sextortion, investment fraud, money laundering associated with illegal online gambling, business email compromise, and e-commerce fraud.
In addition, Interpol's financial intelligence mechanism, I-GRIP, flagged and froze 82,112 bank accounts in 34 countries linked to various cybercrimes and fraudulent operations.
$199 million of the seized amounts concern hard currency, and the remaining $101 million corresponds to the value of 367 digital/virtual assets, such as NFTs (non-fungible tokens) linked to cybercrime.
German police takes down Kingdom Market cybercrime marketplace
The Federal Criminal Police Office in Germany (BKA) and the internet-crime combating unit of Frankfurt (ZIT) have announced the seizure of Kingdom Market, a dark web marketplace for drugs, cybercrime tools, and fake government IDs.
The law enforcement operation also included authorities from the United States, Switzerland, Moldova, and Ukraine, while one of the administrators has been arrested in the US.
The police say the marketplace hosted 42,000 items for sale, 3,600 of which were from Germany.


Post a Comment Community Rules
You need to login in order to post a comment
Not a member yet? Register Now