Update 03/13/13: Please note that the steps in the guide below are outdated. Instead a new method may be available to generate the decryption password for your files. For more information please see this post in our forums:
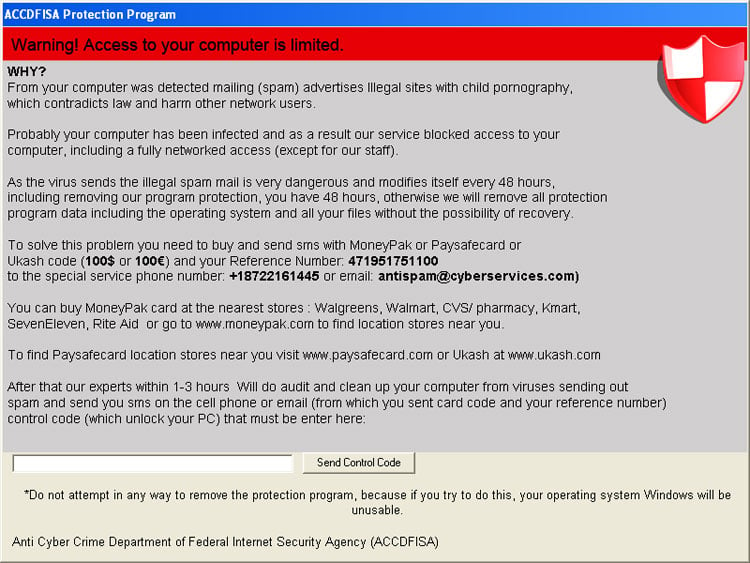
The ACCDFISA Protection Program is a ransomware computer infection that pretends to encrypt your files using AES encryption and then locks you out of the Windows desktop. When first encountered, this infection will state that it is from the Anti Cyber Crime Department of Federal Internet Security Agency and that a computer virus has been detected that is sending out SPAM email containing links to web sites hosting child pornography. The program then states that your data and computer will be inaccessible unless you use the Moneypak or Paysafecard services to send $100 via SMS to a particular phone number within 48 hours. It further warns that if you wait longer than 48 hours, the ACCDFISA program will delete your operating system and documents. As you can imagine this is all a scam that is being performed to scare you into paying $100 dollars for the proper operation of your computer and the restoration of your data. For no reason should you pay this ransom and should instead use the steps below to regain access to your data and computer.
What this program says it does, though, and what it really does is very different. When first installed, the ACCDFISA ransomware will configure itself to start automatically with a RUN key called svchost that points to C:\ProgramData\local\svchost.exe. It will also create two Windows services called Diagnostic Service System Host and Network List System Service. The infection will then proceed to scan your computer's hard drives for data files such as .txt, .doc, .xml, .dat, .docx, .pst, .xls, etc and use the RAR program to create create a password protected archive containing the original files. The original file will then be replaced by this rar file using the AES extension. For example, the file C:\Test.txt would be replaced by a renamed RAR file called C:\Test.aes. A list of all the files that have been "encrypted" can be found in the %System%\wcmtstcsys.sss file, which can be read using the Notepad program.
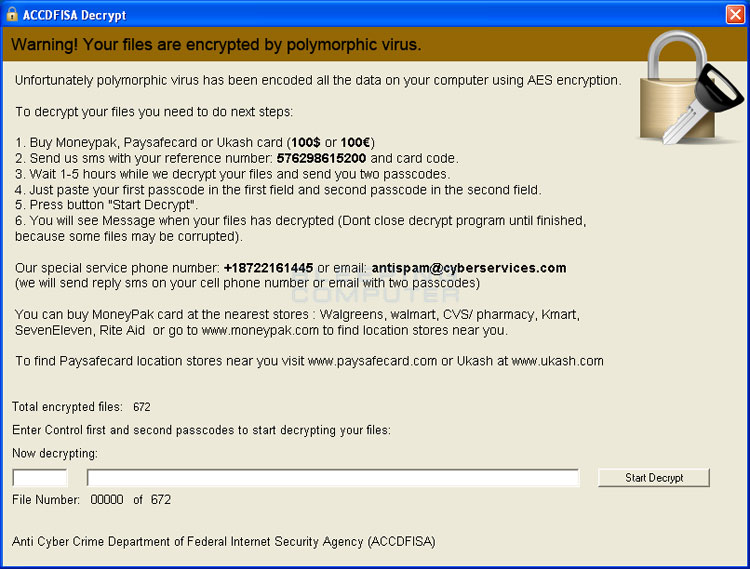
The program will also create a shortcut on your Windows Desktop labeled how to decrypt aes files. When you double-click this shortcut, the C:\Decrypt\decrypt.exe file will be launched and show a screen that states a polymorphic virus has encrypted your data files and that you need to send $100 in order to get the codes that can be used to decrypt the data. It should be noted that if you do decide to pay the ransom or use some of the codes posted on the Internet, this program will simply delete all of your data! Therefore, you should not, for any reason, attempt to decrypt the files using the decrypt program as you will just lose your data. Please remember that these files are not encrypted and are just password protected RAR files, which we will detail how to restore later in the guide.
Last, but not least, this infection will also launch a program when you first login to Windows. This program is displayed before your Windows desktop and will not allow you to access your Desktop unless you enter a Control Code. Once again, in order to get this control code you need to pay $100. Unfortunately, this infection will also delete with Windows Safeboot Registry key, so you will be unable to access Windows Safe mode in order help remove this infection.
From the reports we have had and from the blog post at nFocus Technologies, this infection does not appear to be one that you would get from other malware, hacked websites, or from downloading software. Instead it appears that the infected computers were actually hacked and that the infection was placed there manually. It also appears that these hacks are targeted at Windows Servers and not Windows Workstations. If you are infected with this malware, then it is strongly suggested that you perform a security audit on your computer for other possible security risks.
Thankfully, though, the Control Code and the password for the RAR/Encrypted files were able to extracted and we can guide you on how to remove this infection and restore your files. As said previously, please do not pay the ransom that the malware developers are requesting as you will only receive a code that will delete your files and not restore them. Instead, use the following guide to remove this infection and decrypt the data on your computer.
ACCDFISA Protection Program Removal Options
Self Help Guide
If you are uncomfortable making changes to your computer or following these steps, do not worry! Instead you can get free one-on-one help by asking in the forums.
- Before you start this process, please note that this infection appears to have targeted Windows Servers. Therefore, due to the sensitivity of the data stored on Windows Servers, it is strongly recommended that the System Administrator perform a complete backup of the entire computer before attempting the steps listed below. It is also important that the steps below should only be performed by someone who feels they have enough technical expertise to fully understand what each step performs and that they should be done at your own risk.
- If your computer has been rebooted and you are stuck at the screen asking you to enter a Control Code, you can enter the code 7534919801679213 and then click on the Send Control Code button to regain access to your Windows Desktop. If you already have access to the Windows Desktop, please continue to step 3.
- Now that you are the Windows Desktop, you may notice that you no longer have access to the Internet. This is because the infection will change the IP address of your network adapter(s) to the following:
IP Address: 172.248.0.1
In order to regain access to the network, you will need to go into your network adapter's properties and change the IP address, subnet mask, and gateway back to it's proper configuration.
Gateway: 172.248.0.1
Subnet Mask: 255.255.0.0
- Now that we have Internet access again, it is important to deactivate the virus. To do this, please open a Console window as Administrator and enter the following commands:
net stop netprofms
Then start Regedit and delete the following value: HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\\svchost
net stop WdiServiceSysHost
sc delete netprofms
sc delete WdiServiceSysHost
If you have Internet access on this computer, then you can download the following batch file that performs the above steps automatically for you:
http://download.bleepingcomputer.com/bats/kill-accdfisa.bat
- After you have performed the steps in in Step 4, make sure all your users are disconnected and data has been closed and reboot your computer. Once you reboot the computer, the infection will no longer be active and we can begin the process of restoring the RARed, or encrypted, data files.
- Once your computer has rebooted, download and install WinRar or 7-zip. WinRar or 7-Zip , or another program like it, is necessary in order to extract the file in each of the RARed files. I suggest you use WinRar because I am going to show an extra trick that can be used to automate the restoration of all your files.
- Once one of the above programs is installed, open the %System%\wcmtstcsys.sss file in Notepad. This file contains a list of each and every file that was turned into an RAR archive. I suggest you print this out in order to have a copy that you can refer to. You can then go to the folders listed in the wcmtstcsys.sss file and rename each of the .aes files to have an .rar extension. For example, if you have a file called C:\Windows\test.txt.aes, rename it to C:\Windows\test.txt.rar. You can then right click on the file an extract it. For an easier method, please continue reading this entire step before actually starting the extraction process.
When the extraction program prompts you for a password, please use the following password: 1a2vn57b348741t92451sst0a391ba72
When you extract the files, it will create a folder that contains the full path to the extracted file. This means that for each "encrypted" file, you will need to navigate to the extracted file and move it to its proper place. I know that this can be a large task, so there is a trick you can use to automate this process. This trick could probably be customized to work with a program like 7-zip, but I have only tested it with WinRar, so I suggest you use that program. This trick also requires WinRar to be installed in the C: drive. If installed to another path, please change the command in the batch file as necessary.
To process all the AES files on your your hard drive, open a console window and go to the root of the drive using the cd command. So if we are processing the C: drive, we would open a console window and type the following commands. After each command press Enter on your keyboard.
C:
Your console prompt should now show: C:\>
CD \
Now enter the following command and enter press Enter on your keyboard to process every .AES file and extract it to its proper location. You can use this command for any drive that has AES files by changing to that drive letter, changing to the root directory and issuing the following command again.
FOR /F "TOKENS=*" %G IN (' dir *.aes /a /s /b ') DO ( "C:\Program Files\WinRAR\Rar.exe" x "%G" -p1a2vn57b348741t92451sst0a391ba72 )
I have created a batch file that can be used for this purpose and that you can change for any drives you may need to process. Simply edit the batch file and change the drive line to the associated drive letter that you wish to process. This batch file can be found at the follow URL:
http://download.bleepingcomputer.com/bats/decrypt-aes.bat
All of the original files should now be extracted and back in their original locations.
- This infection also deletes the SafeBoot registry key. If you are unable to access Windows Safe Mode, then you may want to attempt to restore this key by exporting the HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot Registry key from a computer running the same version of Windows and then restore it back to the one that was infected. This should allow you to boot back into safe mode. Please note I was not able to test this on all Windows versions. You can also view this blog post for more information regarding restoring this key.
- You should now move the infection files into another folder that you can either delete or save for forensics. The infection files are:
Windows 32-bit infection files:
c:\how to decrypt aes files.lnk
C:\ProgramData\local\aescrypter.exe
C:\ProgramData\local\crdfoftrs.dll
C:\ProgramData\local\svchost.exe
C:\ProgramData\local\undxkpwvlk.dll
C:\ProgramData\local\vpkswnhisp.dll
C:\Decrypt\Decrypt.exe
%System%\csrsstub.exe
%System%\dcomcnfgui.exe
%System%\tcpsvcss.exe
%System%\tracerpts.exe
%System%\ucsvcsh.exe
%System%\wcmtstcsys.sss
Windows 64-bit infection files
C:\ProgramData\local\aescrypter.exe
C:\ProgramData\local\crdfoftrs.dll
C:\ProgramData\local\svchost.exe
C:\ProgramData\local\undxkpwvlk.dll
C:\ProgramData\local\vpkswnhisp.dll
C:\Users\Public\Desktop\how to decrypt aes files.lnk
C:\Windows\SysWOW64\csrsstub.exe
C:\Windows\SysWOW64\dcomcnfgui.exe
C:\Windows\SysWOW64\tcpsvcss.exe
C:\Windows\SysWOW64\tracerpts.exe
C:\Windows\SysWOW64\ucsvcsh.exe
C:\Windows\SysWOW64\wcmtstcsys.sss
C:\decrypt\decrypt.exe
C:\how to decrypt aes files.lnk - I now suggest that you perform a complete security audit, check event logs to see how the infection may have been installed, and run some anti-malware scans.
- Finally, once you are sure that you have restored all of the AES files back to their proper locations, you can use the following batch file to archive all of the AES files into a folder called aes-backup on the root of drive configured in the batch file.
http://download.bleepingcomputer.com/bats/archive-aes.bat
The ACCDFISA Protection Program infection should now be removed from your computer and your data restored. As already stated, it appears that the servers that contain this infection were hacked in order to install it. Therefore, it is strongly advised that you backup your data and do a complete reinstall to make sure there is nothing left behind that we do now know about. If a reinstall is not possible, then at the bare minimum you should due an audit on the accounts to make sure that new accounts have not been added and also add stronger password policies. Last, but not lease, you may want to use a sniffer or another tool like TCPView to check for processes listening on unusual ports.